Threat Management Best Practices & Common Challenges

Organizations have started prioritizing threat management to help defend against existing and newly emerging security threats and vulnerabilities.
Every organization, regardless of industry and size, faces security threats daily. Digital threats are more dangerous than physical attacks as they give attackers a great deal of security and anonymity.
Lack of awareness about online exploitation leaves businesses vulnerable to security breaches, causing considerable losses in the form of data, capital, and property and threatening business continuity.
Here, we explain the importance of threat management for organizations, the common challenges faced by security teams, and the best practices that make threat management efficient and successful.
On this page:
What is Threat Management?
Threat management is a framework implemented by security professionals to manage the life cycle of threats to identify and respond quickly and accurately.
For organizations, threat management is a precautionary practice to detect threats to a system using advanced programs.
At its core, threat Management comprises of five primary functions: identify, protect, detect, respond, and recover:
- Identify – Cybersecurity teams must have a firm grasp of the organization’s most valuable assets and resources. The identify function encompasses various areas, including asset management, business environment, governance, risk assessment, risk management strategy, and supply chain risk management.
- Protect – Responsible for a large portion of the technological and physical security controls necessary for creating and executing suitable safeguards and safeguarding critical infrastructure. These include identity management and access control, awareness and education, information protection processes and procedures, data security, and maintenance and protective technology.
- Detect – Automates the process of alerting an organization about cyberattacks. Anomalies and occurrences, continuous security monitoring, and early detection methods are all examples of detect categories.
- Respond – Guarantees that cyberattacks and other incidents are responded to appropriately. Response planning, communications, analysis, mitigation, and improvement are all included in these categories.
- Recover – Implements plans for cyber resilience and ensure business continuity in the event of a cyberattack, security breach or another cybersecurity event. The recovery functions are recovery planning improvements and communications.
Threat management employs different procedures like machine learning, artificial intelligence, behavioural analysis, prediction tools, IoT modules, and others to ensure data integrity and prevent any holes in the security systems.
Threat management relies on seamless integration between people, processes, and technology to stay ahead of unknown and emerging threats and security risks.
Threat Lifecycle Management
Threat Management Lifecycle services is a series of aligned security operations capabilities, which encompass a set of proactive activities to:
- Recognize threats and their relevance to you, your vertical, or area
- Discover previously undiscovered threats in the environment
- Allow for fast triaging of threats to increase automation and efficiency
- Capture insights from hunting operations and threat intelligence to fine-tune rules for improved detection and reaction
Threat Lifecycle Management (TLM) begins with the ability to monitor and search broadly across your IT environment. It concludes with the mitigation and recovery from incidents.
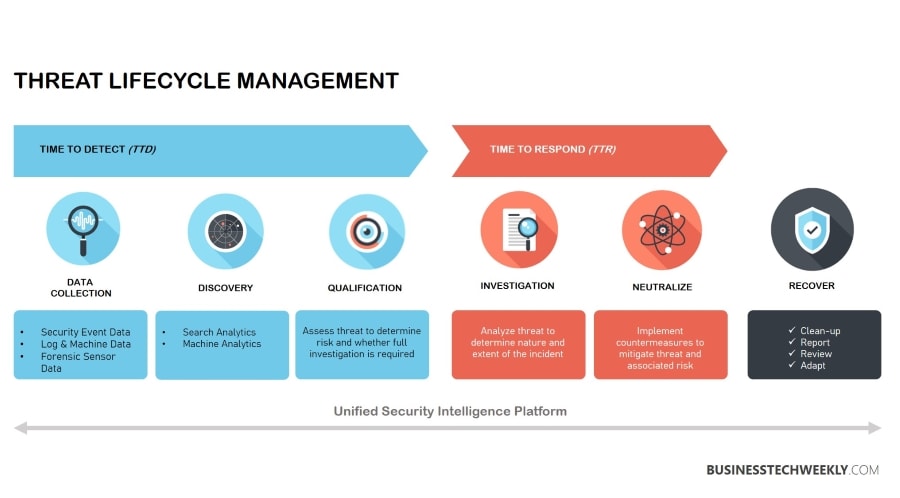
Threat Lifecycle Management aims to reduce the time to detect and time to respond to threats and incidents without adding excessive resources to accomplish the job.
Why is Threat Management crucial?
There is an ever-increasing rise in threats to systems and networks across the world. Enterprise systems are becoming more susceptible to security breaches with new technologies to improve collaboration and communication.
Whether internal or external, security threats result in financial losses and affect the reputation and trust in the business.
As security attacks get more complex and the variety of threats increases, organizations constantly struggle to protect their systems with advanced mitigation and prevention solutions.
Organizations that prioritize adoption and implementation of a practical threat management framework enjoy benefits like:
- Reduced risk with faster threat detection, faster response, and consistent checking
- Continuously improving security system through built-in process analysis and reporting throughout the lifecycle of threats
- A unified security team through increased skills, morale, and effective threat management solutions
A reliable threat management system also helps satisfy the compliance and regulatory requirements for security teams. Most businesses consider integrating a threat mitigation strategy to prevent risks of data theft and corruption.
Compliance policies in an organization focus on protecting sensitive data and keeping the network safe against external threats. However, an effective threat management strategy should focus on protecting businesses against existing and emerging threats.
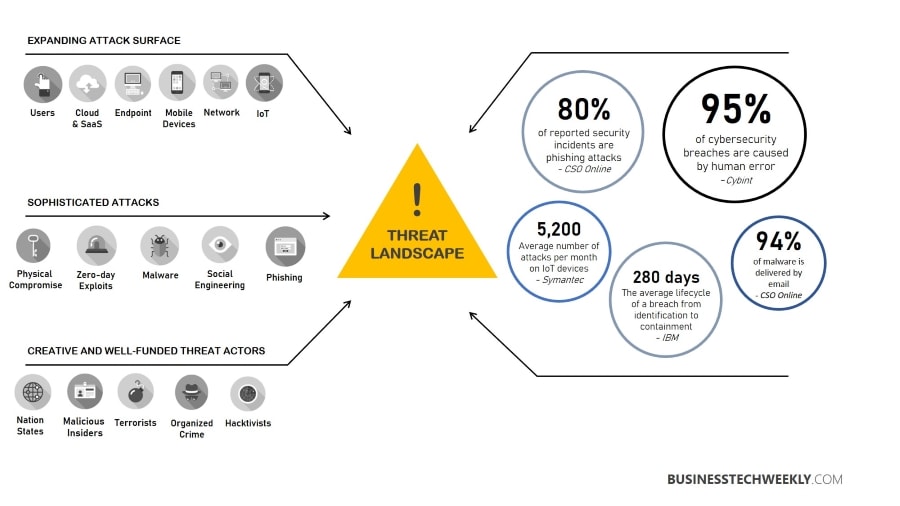
Common Threat Management Challenges
Security teams often find it hard to protect the system against advanced, more complex threats and threats emerging from internal sources. Security leaders in the industry face many challenges.
Lack of System Visibility
Security professionals don’t always find the resources available to get complete visibility into the threat landscape in proper context.
For effective threat management, teams must have insight into internal data like databases, HR, and cloud and external data from social media, the dark web, and threat intelligence.
This challenge often results from departmental silos in the organization, lack of integration between solutions, insufficient coordination among security teams, and inconsistent processes across the entity.
Lack of Useful Insights and Insufficient Reporting
Security teams often don’t have insights into the right key performance indicators and metrics that should be tracked.
Lack of integration between solutions in the organization makes it difficult for them to create reports showing the progress against compliance and standards. Moreover, if security teams are measured against varying performance indicators, it becomes difficult to align them on a unified organizational goal.
According to cybersecurity experts, one of the most prominent challenges organizations face when creating effective threat management solutions is the complexity of the IT landscape.
Staff Burnout and Shortage of Skills
Burnout of security analysts and increasing skill shortage in the market makes it challenging to acquire skilled staff and keep the existing teams motivated. Security leaders also face the challenge of additional staff budget.
They should look for creative ways to use talent from other units like sales, customer support, and others. They often consider training these employees to work effectively in the security field.
Budgetary Constraints
Threat management programs are often challenging to plan and implement as businesses don’t have a sufficient budget for IT.
A report on IT budgets suggests that information officers worldwide anticipate a negative growth for IT budgets compared to other areas.
The shrinking budgets mean companies prioritize AI and cloud services and ignore incident management, threat management, and other security processes.
Insider Threats
Many cybersecurity frameworks are built upon the assumption that attacks originate from external sources like hackers trying to intrude.
However, this is not necessarily the case. A significant challenge impeding threat management’s success is that organizations are not well-equipped to handle the threats from within. Some of the most common attackers are those possessing privileged access to the company network.
Disgruntled former and current employees, contractors with temporary access, and careless staff members are likely to compromise business information security and give rise to internal attacks. Insider attacks are more dangerous as they can go undetected for longer, creating more havoc than external attacks.
Best Practices for Effective Threat Management
Managing threats is not easy, particularly when businesses face a host of challenges from several internal and external factors. Enterprises today want their threat management practices to align with compliance management as well.
Security teams must identify and address threats beyond existing strategies and plan for future security risks. This is challenging because creating a strategy against unknown and emerging threats is challenging than existing ones.
Below, we provide some best practices a threat management framework should consist of:
 Awareness – There are two types of context considerations associated with threat management. Internal context includes comprehending the potential impact of the affected systems relating to the people in the organization. In contrast, external context consists of understanding infections from outside sources.
Awareness – There are two types of context considerations associated with threat management. Internal context includes comprehending the potential impact of the affected systems relating to the people in the organization. In contrast, external context consists of understanding infections from outside sources.
When an attack reaches an internal system, it is necessary to pull data from infected machines to confirm the infection. How quickly security teams can do this is critical for response time.
 Existing Preventative Measures – When a threat is detected, it is essential to find whether it was contained using existing tools and devices.
Existing Preventative Measures – When a threat is detected, it is essential to find whether it was contained using existing tools and devices.
Detection is different from protection. You may receive several alerts every week. Still, you should find a way to verify whether existing security layers have been adequate. The only way is to get into the context of the threat.
 Threat Detection – An essential step in threat management is the detection phase of a threat. Detection gives you a large number of signals, and compromises but you need to investigate further to validate the threat and take preventative action.
Threat Detection – An essential step in threat management is the detection phase of a threat. Detection gives you a large number of signals, and compromises but you need to investigate further to validate the threat and take preventative action.
 Response – When equipped with a rich threat context, analysts can ensure sensitive data, departments, and teams are treated for security. Some of the most effective protective responses include improved logging, communication limitation, additional scans, network segment isolation, blocking IPs, etc.
Response – When equipped with a rich threat context, analysts can ensure sensitive data, departments, and teams are treated for security. Some of the most effective protective responses include improved logging, communication limitation, additional scans, network segment isolation, blocking IPs, etc.
Automation of enforcement updates gives the best assurance. However, it is vital to verify and confirm that all the devices have been appropriately updated if done manually. A single outdated device can turn out to be a vulnerability and a source of infection spreading across the system.
 Enforcement – Another essential practice is to evaluate the enforcement devices to confirm they are updated and performing all the time.
Enforcement – Another essential practice is to evaluate the enforcement devices to confirm they are updated and performing all the time.
An IT audit of responses can be of great help. However, when done manually, enforcement audits and updates can be subject to errors.
A proper enforcement procedure should be based on priorities influenced by internal and external factors. This means low priority incidents are addressed after securing high-priority systems and networks.
 Testing – Everything should be tested regularly to ensure both automated and manual processes are working well. Keeping track of your system performance assures you that you have an effective threat management strategy in place.
Testing – Everything should be tested regularly to ensure both automated and manual processes are working well. Keeping track of your system performance assures you that you have an effective threat management strategy in place.
You should at least perform a conformance test and multiple regression tests per quarter.
With robust best practices and intelligent automation, IT teams can reduce risk and save time with solid threat management and response system. Such a system closes any gap between threat detection and response, giving organizations a better chance to stay secure in case of an attack.
Emerging threats can either exploit a technology implemented in the organization or target newly deployed hardware, software, or architecture. Threats emerging against IoT, public clouds, mobile devices, and AI are examples of such risks.
An effective threat management strategy should contain protection against traditional and new threats. The business should combine defense and response mechanisms to prevent threats more efficiently and quickly succeed.
Final Thoughts
The rise of data theft and online hacking makes it essential for businesses, small and big, to protect their data and systems.
Threat management is one of the simplest ways to ensure business data remains secure and protected, thereby saving capital over time and increasing reputation and trust among customers.
Though security teams face many challenges, organizations can implement best practices to make their threat management process effective and successful.

