5 Cybersecurity Tips for Remote Workers
With an increasing number of employees working remotely, organizations are facing additional challenges, necessitating the implemention of additional cybersecurity controls for remote workers.

With a boom in digital cloud environments, and with the onset of the recent pandemic, many employers have relied on staff working remotely. However, remote and mobile employees can pose an information security threat, primarily due to the lack of robust cybersecurity practices for remote workers.
On this page:
The Growth of Remote Working
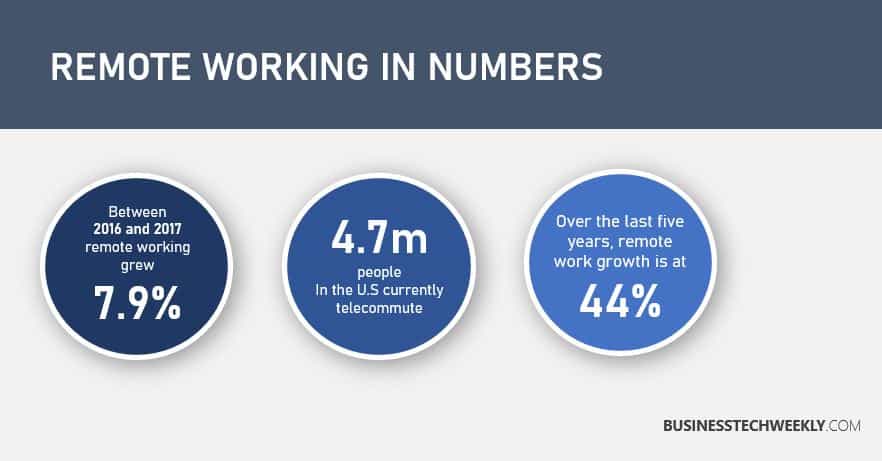
Businesses are increasingly migrating their operations online. Cloud-based Software as a Service (SaaS) applications has helped organizations provide an uninterrupted service around the clock for their customers. However, this also means businesses and organizations are exposed to another potential threat source whilst offering remote working benefits to their workforce. The rise in remote and mobile working has meant that the traditional perimeters of the office environment have increased from a single, or handful of, locations, to hundreds. Even organizations which previously had identified practices and processes to support remote working may find themselves struggling to support mobile and remote workers on such scale. This situation provides ample opportunity for cybercriminals to flourish. Consequently, with the majority of employees working remotely, there’s one thing organizations need to be concerned about – cybersecurity.
Top Cybersecurity Risks Facing Remote Workers
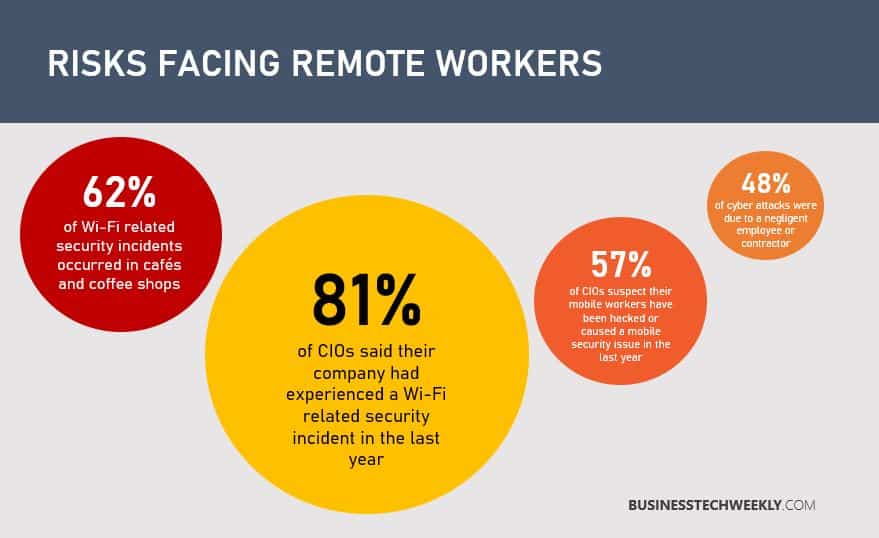
Several recent reports indicate that remote working or work from home benefits will increasingly become more commonplace with businesses. Not only as part of a business continuity plan during a pandemic but in the future, too. However, cyber threats are not just limited to malicious outsiders. Simple mistakes made by employees – who are unaccustomed with working from home, or haven’t received the appropriate training – can compromise their security and that of the entire organization. Presented below are the top three cyber risks that organizations need to address:
- Use of Unsecured Wi-Fi Networks – Employees accessing company networks using Wi-Fi from popular locations (such as a coffee shop) can be more susceptible to cyberattacks.
- Lack of Cybersecurity Awareness and Training – Ensuring that there is a training program in place for best practices on security is paramount in defending against cybersecurity threats.
- Lack of Physical Security or Personal Use of Laptops – Leaving work devices in the open, letting non-employees, such as family and friends, borrow devices for personal use, or using corporate devices to answer personal emails, shop online or visit social media pages, are all examples of risky behaviour that employees may engage in whilst working remotely.
5 Essential Cybersecurity Tips for Remote Workers
While organizations can opt for cyber liability insurance to safeguard themselves from cyber attacks, its imperative that cybersecurity best practices for remote workers are firmly in place. By implementing and following cybersecurity best practices and policies for remote working, you can effectively deal with the potential threats, saving your company from potential financial and data loss. Presented below are five tips for ensuring the cybersecurity of your remote employees:
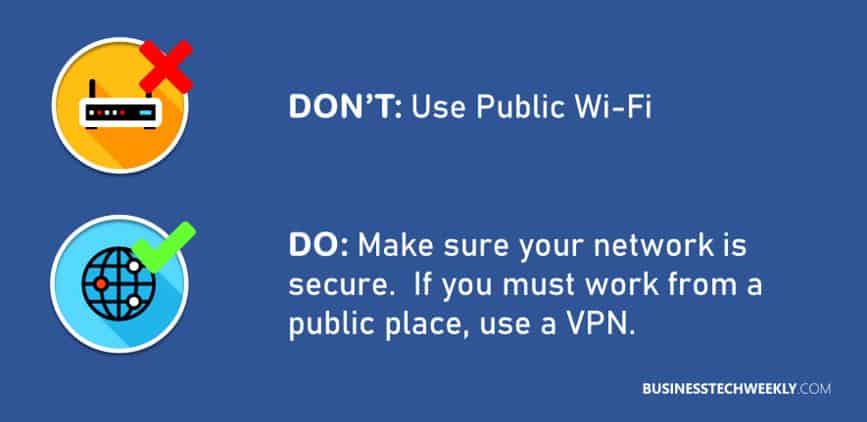
Public Wi-Fi is a significant security risk. No authentication is required on many public Wi-Fi networks, and you need to avoid it. When you use a public Wi-Fi connection, you face two problems:
- Firstly, there are lots of other people who have access to this connection, and no firewall exists between you and them.
- Secondly, a malicious individual can observe your traffic because, in public networks, the data unencrypted between you and your workplace.
When using public Wi-Fi, it’s better to use a VPN to access remote company resources. VPNs offer flexible connections and allow you to connect with (email, webpage, a SQL server, etc.) while protecting your traffic.
2. Keep Your Work Data on your Work PC
When you use your work computer, you should take precautions such as VPN, antivirus, encrypted drives, and endpoint protection. However, if you use a personal computer to access work files, it can pose a severe risk for you and your company. Most organizations have a dynamic IT team, who regularly run antivirus scans, install updates, and block malicious sites. Your personal device is unlikely to have secured to such stringent levels. Consequently, your personal computer isn’t safe for work-related matters. By using a personal computer for office work, you are potentially placing your company’s network at risk. A good practice is to use your personal computer for individual work and a work-issued laptop or PC for your company.

3. Encrypt Sensitive Data
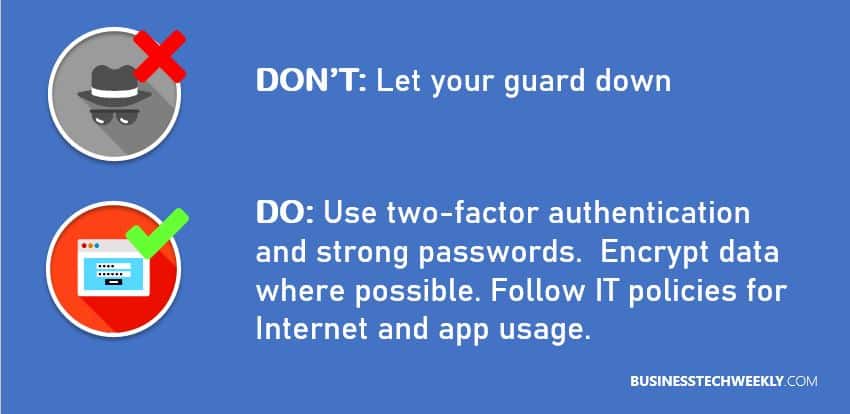
When you send emails containing sensitive data, it’s always risky. It can be seen and intercepted by a third-party. When you encrypt the data attached in an email, it won’t allow an unauthorized person to view this. Moreover, ensure that your device has all the data encrypted so that you and your organization can feel safe in case the device is stolen.
4. Maintain Good Physical Security Practices
Maintaining the physical security of company devices issued to remote workers can be challenging. Leaving a device in an unlocked car, or something as simple as leaving a device out in the open at home could lead to a security breach. Here are some physical security measures to incorporate into your cybersecurity best practices for remote workers:
- The importance of physical security should be emphasized for remote employees, and it should be one of the core pillars of your business’s cybersecurity policy and best practices
- If available, enable the “find my device” setting in case the device is misplaced
- Monitor company-issued device usage to observe any non-work-related activity, or the potential use of a work device by a non-employee
- Instil in remote workers (and all employees) to keep devices on themselves. When not in use, these devices must be stored securely
- Remind all employees to be aware of their surroundings when working in public so that no one can see their screen, and not to leave devices unattended.
5. Avoid Using Unidentified USB Drives
In some cases, a cybercriminal may “drop” large capacity USB drives near their targeted company, where an unwitting employee may pick it up. The USB drive is likely to contain malware, which could provide a hacker with unauthorized access to your systems. Unless you know its source, random USB thumb drives should not be used. If you are unable to verify the source of the USB device, don’t use it. When you charge your phone at a public charging station, use a USB data blocker. It will protect against malware and prevent data exchange. This USB protection allows you to charge your device without exposing the data pins present in your device. It will ensure that power leads are connected instead of data ones.
Employing Cybersecurity Controls for Remote Workers
Remote working can pose severe cyber security threats for organizations of all sizes. The investment in developing a comprehensive cybersecurity policy for remote and mobile workers is a small price to pay in comparison to the potential costs to the organization in the event of a data breach. It should be recognized that cybersecurity risks associated with remote working will always be present. However, employing the controls outlined above, and following best practices, will help organizations address the cybersecurity risks and threats that make remote workers particularly susceptible. Organizations should also take steps to ensure all employees are regularly updated about any potential security vulnerabilities, and how they can recognize and avoid them. If you’re struggling with developing your own set of cybersecurity best practices, policies and procedures, you should engage with a local IT security provider. They can advise, develop and implement customized policies and procedures, specifically based on your operating model.
Adopting Cybersecurity Best Practices for Remote Working
The widespread adoption of cloud computing has provided businesses with multiple opportunities, including the practice of “working from home.” Globally, the work-from-home culture has already been adopted by many businesses, and these numbers are expected to grow. Staff working from home can be more productive, prompting employers to consider this option as a permanent feature of their business operating model. To reduce your remote workers from being exposed to cyber threats, you should consider incorporating the following into your remote working and cybersecurity best practice and policies:
- Ban the use of unsecured connections.
- Use geolocation to restrict the locations from where company networks can be accessed.
- Mandate VPN connections for remote access to work resources, such as files, documents, email.
- Refrain users from accessing personal emails, and files, from work devices.
- Educate employees about cyberattacks and social engineering techniques.
- Make Multi-factor Authentication (MFA) mandatory for your remote employees if they’re accessing critical accounts from outside the office network.
- Deploy a secure backup mechanism. Device encryption and setting a regular backup of daily tasks completed will safeguard you if the users lose their work device.
- Promote the use of secure collaboration tools like Microsoft Teams and G Suite.

