5 Social engineering techniques that exploit business employees

Cyber criminals employ several social engineering techniques to extract information from business employees. Social engineering techniques include carrying out particular background research on social media and other sites. Armed with this knowledge, scammers can employ their social engineering techniques discretely, putting staff members at ease, and even build a rapport with them.
It is simpler than you can imagine. Once the hackers gain access to a business’ confidential data, will then target:
- Login information
- Network private data
- Background and personal information of employees
- Private data on payrolls
- Company Gantt charts
- Customer private information
- Tax papers
- Access to the company building
Unfortunately, the lack of proper security training at many businesses fuels the viability of employee exploitation by scammers, leading to more cyber attacks.
Robust access controls implemented as part of cybersecurity significantly contribute to a secure environment. Yet, if cybercriminals can exploit members of staff, even the best cybersecurity is useless.
Consequently, firms must ensure that their staff are trained correctly and adequately to recognise social engineering techniques, exploits and methods.

Exploiting human nature
Many people are willing and trusting, both crucial traits to build a prosperous society. Such people will help out another person without any suspicion. Unfortunately, those with malicious intent, identify generous human nature for exploitation as a means of access to data and profit. Social engineers target several elements of human nature, including:
Avoiding conflict
Most people try to avoid confrontation, particularly if they are not empowered to do so. For example, very few employees will challenge someone entering a building. Not many people will state their concerns about building security, and deny entry.
Desire to follow directions
Generally, employees are conditioned to comply with commands or requests from senior management. Social engineers may impersonate an authority figure, either from within the business or as an external official to gain sensitive and confidential business information. Such examples can be seen in W-2 schemes, whereby scammers pose as company executives demanding access to tax documents.
Willingness to help other people
Many people are not suspicious, willing to help out another individual. When scammers know this, they will attempt to target victims to compel them to act out of an unselfish desire to be helpful. Often, this is propositioned as the verification of information or help in solving a problem.
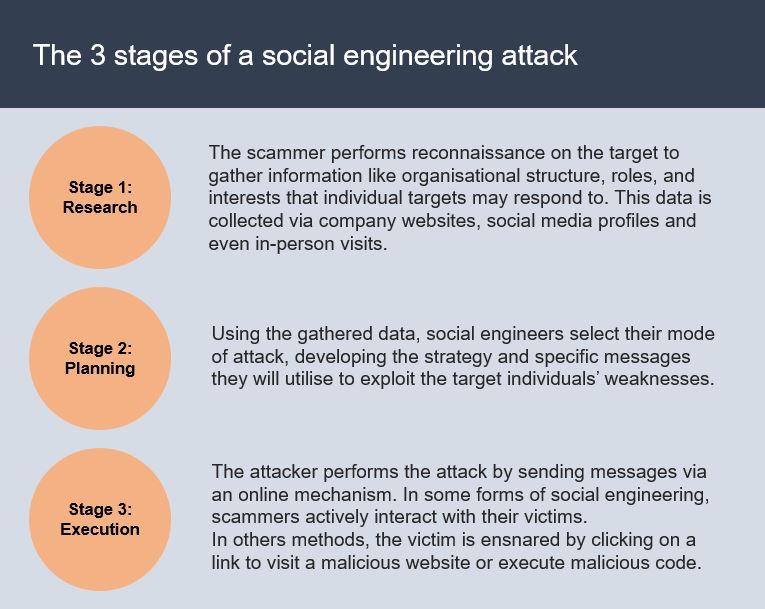
Top 5 social engineering techniques
In terms of information security, social engineering aims to extract confidential information through the psychological manipulation of people. Below are presented some of the common social engineering techniques employed:
1. Phishing
Currently, the most common social engineering exploitation method. Scammers will create emails, chatbots, or sites which mimic and impersonate a real system, web site or authoritative entity. Messages are sent to the target victims to pry out information by soliciting a response given by the employees.
For instance, an employee may receive emails purporting to be from the bank. The email could state that someone has hijacked the business and that all authentication details must be updated immediately by clicking a specified link. By clicking on the link, the victim will lead to a malicious website which will either capture the data entered or automatically, and discretely, download malicious code to the victim’s system.
2. Baiting
Similar to phishing, this social engineering technique lures staff members leading to the inadvertent downloading of malware. How successful the attack is, depends on the victim’s need, curiosity or even greed. Baiting can be performed digitally or physically.
The “bait” could be a film or the latest game that can be accessed on a P2P site. The bait may be removable media, such as a USB drive, purporting to contain employee salaries, and left purposefully unattended for the finder load its content.
Once the bait has been plugged in or download (depending on the mechanism used), any malware will infect the business systems and discretely allow access to the cybercriminals.
3. A favour in return
Or Quid professional quo, aim to entice the target victim with a trade. For example, purporting to be from an IT vendor, the cybercriminal may offer a free network audit. The catch is that they require network credential to perform the free service.
4. Pretexting
In pretexting, a scenario is fabricated, or a false identity is assumed to deceive someone into providing confidential information. Pretexting is a social engineering technique which can be pursued via several channels, such as email, over the phone, or in person.
In pretexting, the scammer will aim to build trust with potential victims, purporting to be a colleague or somebody in a position of authority. If the scammer can build the rapport with the target member of staff, the employee may provide their network credentials without thinking.
Pretexting is easier than people think. It is easy to see how employees, particularly if they are busy and never a hundred per cent focused, may be deceived.
5. Tailgating
Also known as piggybacking. Tailgating occurs when an unauthorised individual follows an authorised person into a restricted area or system.
A frequently cited example of this is when an ’employee’ asks to hold a door open as a result of forgetting their security pass.
See also: What is shoulder surfing?
Preventing social engineering attacks
Similar to malware and other security threats, social engineering is becoming more complicated. The measures presented below can contribute to the prevention of social engineering attacks against your staff and business.
Antivirus and endpoint security tools
As cybersecurity best practice, businesses should ensure that all user devices have antivirus and other endpoint security measures installed. The latest endpoint protection tools are feature-rich, with the capability to identify and block known phishing messages, links to malicious websites or IPs listed in the vendor’s threat databases. These tools can block malicious processes in the event they are executed on a user’s device.
Penetration testing
Social engineers can identify several ways of breaching a business’ network. By performing penetration testing, any weakness and vulnerabilities are identified. A successful penetration test which compromises sensitive systems will help detect members of staff or systems which require attention – either by identifying which areas need improved protection or are particularly susceptibale to social engineering.
Security awareness training
Businesses need to ensure that members of staff receive periodic security awareness training. Members of the team might not be aware of the dangers, methods, or techniques of social engineering.
Regular security awareness training will ensure that staff members are kept informed of the latest developments in social engineering techniques and how to recognise such attempts. Conducting, and continuously reinforcing staff security awareness is the first step in protecting against data breaches, particularly social engineering.

