Wi-Fi security: Securing your wireless network

Compared to traditional wired networks, wireless networks can be at an increased risk of an attack. These issues can have adverse effects on your business, including the denial of service attacks, spoofing, and session hijacking. As with any security measure, wireless security aims to prevent the unauthorized access, or damage, to your systems and data, which use a wireless network.
Presented below are some of the common potential security issues found in wireless networks and how these can be addressed.
On this page:
Wireless network security issues and threats
One of the primary concerns with wireless transmission is eavesdropping. Others’ listen in’ on your business conversation or activities and use this information against you to cause damages to your business, such as undercutting your prices.
While there are several wireless security threats, the three most common WLAN security threats are:
- Denial of Service Attacks (DoS) – intruder sends tons of messages to the network which affects the network resources
- Spoofing and Session Hijacking – intruder steals identity and pretends to be a valid user to enter the network data and resources
- Passive Capturing or Eavesdropping – unauthorized parties stop data transmission through secure network and spy
Make sure your WLAN is configured appropriately to prevent or fight these threats. There are some security features that you should consider enabling like standard authentication and encryption, alongside other access control mechanisms. In short, take as many measures as possible to stay on the safer side.

Implementing basic WLAN security features
If you look back, there were some basic security methods used for the old WLAN hardware too. Such as:
- Service Set Identifiers (SSIDs) – if a device doesn’t use a given identifier properly, it prevents any connection to access points
- Media Access Control (MAC) – this security method needs the addresses attached to every device, so the connection to access points can be limited
- Wired Equivalent Privacy (WEP) – to ensure the maximum security WEP uses encryption keys which allows the devices with correct keys to communicating with access points
Since many users faced compatibility issues with newer equipment, they adhered to the good old WEP, and that’s why WEP is still in the field keeping the devices safe.
Sadly WEP isn’t strong enough to protect the devices from hackers. You need something more substantial to chase hackers off of your device. So go ahead and upgrade the WEP technology devices.

No matter how many security measures you take, basic WLAN features won’t give you the best protection. On top of that, some WLAN equipment has a security switch. Often the switch is turned off, and until you turn it on, you will be left completely unprotected. This is not worth the risk.
Upgrade your WLAN security protocols
Make sure you set up the basic security features of WLAN correctly so that you get maximum effective protection.
For a better experience and security, you must upgrade the system to a better protecting security method, for example, WPA (Wi-Fi Protected Access) and WPA2. WPA3 is the latest version of this protocol and is also the most secure.
Wi-Fi protected access (WPA)
The previous security methods of WLAN were not very strong. The WEP (Wired Equivalent Privacy) is exceptionally vulnerable to hacking.
All these inadequate security measures called for better security protocols and the Wi-Fi alliance – representative of most wireless hardware suppliers – heard it. They started producing better security protocols named Wi-Fi protected access along with its successor WPA2.

What is Wi-Fi Protected Access?
Since the WPA and WPA2 are using more durable and better encryption methods, it’s not as weak as it was with WEP. Check for ‘Wi-Fi WPA’ in the specification to be sure if the product is using WPA and WPA2. Choosing a product that complies with WPA will work together, meeting a very crucial requirement.
The WPA and WPA2 have two operative modes:
- Personal mode – this mode requires a pre-shared password or passphrase for verification. This will help keep the security of WLAN intact and prevent all sorts of invasion if there’s no match found with the access point’s password.
- Enterprise mode – this is more suitable for larger organizations needing better and stronger protection. This mode provides a more sophisticated and smart encryption method.
Which standards to use with WPA2?
The IEEE‘s 802.11i standard is based on a pre-existing standard 802.1X used for wired networks.
This approach makes sure that all the network-connected devices are authenticated. Moreover, it doesn’t allow the network to get access until these devices pass the verification. It even uses different upgraded security methods such as:
- temporal key integrity protocol
- counter-mode/CBC-MAC protocol
Over time, you may find this more useful for your business as the developing technologies are becoming more compatible with the 802.11i standard. WPA2 is derived from standard 802.11i.
A small business selecting standard 802.11n or 802.11ac will get more help for particle uses. WPA2-based devices will work best with standard 802.11i since it has more additional features for the future.
However, notice that you might not always get the wireless hardware with active security as they often supply with the security settings turned off. So while setting it up, don’t forget to check the device thoroughly. Help yourself with ten tips for better wireless network security.
Improve network security with VPN and firewalls
You can use Wi-Fi protected access based latest security protocols. This will increase the defense of your wireless local area network.
However, using virtual private networks (VPNs) and firewalls can also strengthen your overall network security, including security for your wireless networks.
Virtual private networks
Using a VPN gives you the benefits of creating a secure network with an insecure WLAN system even. Using a VPN will encrypt all of the data passing over the network. This will prevent the eavesdropper from reading it.
Although VPN encryption is sufficient to secure the wireless traffic, there are some drawbacks as well. For example, you may notice that some VPNs are:
- difficult to set up internally, which means you have to get expert advice and get yourself an effective VPN system
- troubling users that need to be in different rooms always for work. This is the case mostly with large buildings that have multiple access points transferring data between your devices. The reason behind this is the need for transferring data from one access point to another.
Firewalls
A firewall is a network security system device or software that controls the ingoing and outgoing network traffic. A firewall is used to:
- detach any unsafe network from the secured data management area
- detach the irrelevant wireless data traffic from your wired network
However, setting up a firewall would not be a pleasant experience if you don’t have some prior technical knowledge. So, your best bet would be hiring an IT specialist unless you want to keep loopholes.
You may already have a firewall in place if you have any pre-existing internet connection. But remember, you can’t use this to protect your WLAN. You need better security and an extra device according to your network design.
In case you don’t have good internal IT security skills available, don’t hesitate to ask for help from an expert consultant to help you out with the network design.
Keep in mind that you can’t ensure complete protection with one solution only. Because many network vulnerabilities need proper attention. The best way you can ensure maximum safety to your wireless network is to:
- correct setup and adequate maintenance of the network and connected devices
- apply the right and proper safety measures
- teach your staff the acceptable use and the best networking practices
General tips for reducing wireless network security threats
Thankfully, there are many steps organizations can take to address the several wireless network threats presented above:
- Ensure that your staff and employees use strong passwords.
- Restrict access to authorized users only. If a guest requires access, you can set up a guest account with specific privileges using a separate wireless channel and a unique password. This will enable you to maintain the privacy of your primary credentials.
- Rename you SSID, change its default values, and disable its broadcast to other users.
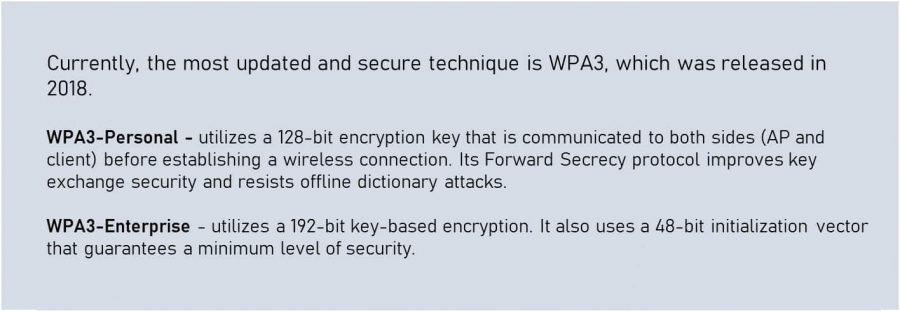
- Use the WPA3 protocol to encrypt your data. WPA3 is currently the strongest level of Wi-FI encryption available.
- Implement a host-based firewall.
- Unacceptable file-sharing practices must be discouraged, for example:
- Do not use public networks to share files.
- If you do need to share files, create a restricted and dedicated sharing directory.
- If file sharing is not needed, it should be disabled
- Regularly update and install security and software patches for all your wireless access points (WAP).
- To enable out-of-office network connectivity for your employees, you should deploy a VPN (Virtual Private Network).
If not implemented already, you should seek to implement the above tips before you suffer a breach. You learn more about improving Wi-Fi security by reading ten tips for better wireless network security.

