Getting started with Data Privacy: What is it and why is it important?

As reliance on technology increases, unprecedented levels of data are being shared and stored online. Due to this digitisation, the privacy, and security, of data has become an increasingly important concern for individuals, businesses, and governments. A single company may hold data on millions of customers, and they need to keep that data private to ensure their customers are secure and protected. Here we explain what data privacy is and why it is important.
On this page:
What is data privacy?
Data privacy focuses on the handling of confidential and sensitive data in accordance with its importance. Data privacy covers how data should be collected, stored, and shared with any third parties, and ensure it is handled in compliance with applicable privacy laws. The level of importance attributed to a piece of data, and the context it is collected in, is core to data privacy.
For instance, you may wish to tell someone you don’t know your name, but you are unlikely to share further personal information until you are more familiar with that person. However, when opening a bank account, you are required to divulge personal data rather than just your name.
Critical personal information, or Personally Identifiable Information (PII), can include financial data such as ATM and bank account numbers, health and medical records, and Social Security numbers. Moreover, it can also include necessary yet sensitive information such as addresses, full names, and birthdays.
Why is data privacy important?
Technology is developing at a rapid pace, and organisations are keen to leverage the latest developments in technology to protect the personal and sensitive information of customers and employees. However, the anonymity and borderless nature of the Internet has allowed cybercriminals to exploit confidential data for malicious purposes.
Personal and sensitive data must be secure, and when it goes to the wrong hands, they can misuse your data. A data breach can happen at private firms and government agencies, with your sensitive information, falling into the hands of enemies or hackers.
A data breach can happen at schools, doctor’s offices, or any business corporation, allowing cybercriminals to manipulate this data for identity theft. That’s why data privacy is essential, and you need to put locks on personal and sensitive information to protect customer and employee data from cyber-attacks and data breaches.
What is the difference between data privacy and data security?
While both terms are used interchangeably, data privacy is not the same as data security. Organisations believe that protecting personal data from malicious actors ensures compliance with data privacy regulations; however, this is not the case.
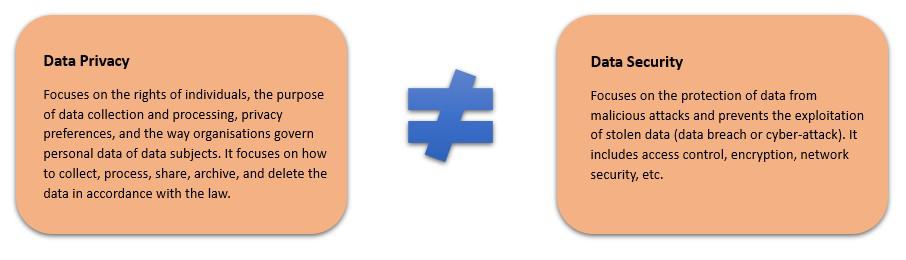
Data privacy is primarily focused on determining what data needs to be collected and what information should not be asked for from your clients or users. Data security, on the other hand, focuses on the protection of the data which has been collected by creating and maintaining a secure network and environment.
- Data Privacy – relates to the way organisations govern personal data, particularly how to collect, process, share, archive, and delete data. Data privacy seeks to ensure compliance with data protection laws and regulations, such as the EU General Data Protection Regulation (GDPR) or the US Health Insurance Portability and Accountability Act (HIPAA).
- Data Security – relates to the measures an organisation takes to prevent any unauthorised access to the data. Data security seeks to ensure that adequate controls are in place to protect the data.
Generally, businesses are unable to collect Personally Identifiable Information (PII) without the consent of the individual concerned – even the data is secured. If you do this, you violate the regulations of data privacy.
Five tips for maintaining data privacy: Keeping financial and Personally Identifiable Information (PII) secure and safe
To prevent personal identifiable data from being exposed, organisations are spending lots of money on technology to protect customer and employee data. While some of the larger organisations can afford to fund human and financial resources to address data privacy needs, many small and medium businesses don’t have the same luxury.
As such, SMEs have to prioritise the technologies that they deploy to ensure data privacy and protection. SMEs looking to focus their resources in the right areas can follow the tips presented below to ensure cost-effective data privacy and protection:
1. Prevent the unauthorised collection of data
Malicious actors and cybercriminals will try various methods to breach an organisation’s cyber defences to obtain confidential and sensitive data illicitly. Some of the techniques, and ways to prevent them, are presented below:
- Social engineering – Social engineering is a technique in which a person attempts to manipulate or influence a person or group of persons to gain some benefit for themselves. Fortunately, most common social engineering methods are well known. Business owners should make their employees aware of such malicious tactics.
- Online scams & phishing – There are many real dangers to your business’ security when you use social networks, particularly when employees or customers may share sensitive information online. Social media scams, such as phishing, are common, and raising awareness of these amongst employees will help prevent such frauds from occurring.
- Malware – Malware, including rootkits and trojans, are another way unscrupulous individuals may use to obtain sensitive information. One way to prevent malware is to install business anti-virus software. If you already suspect malware, there are a range of free malware removal tools.
- System exploits – Hackers like security flaws, also called software vulnerabilities. These are essentially a security hole or weakness found in a software program or running system. Ensuring your systems are up-to-date with the latest version or patch will keep hackers from making use of any security flaws.
2. Ensure data is shared and stored securely
One way to ensure data privacy, and that PII is kept private and secure is through encryption. Encryption allows the data to be only accessible by those individuals with the correct encryption key.
While encryption itself does not prevent a malicious actor from attempting to access the data, it does deny the cybercriminal the ability to read the “data at rest” by rendering the content intelligible. Some common forms of encryption are presented below:
- Cloud backups/storage – For SMEs, it is essential you have a back-up facility in place in the event that your business data is stolen, deleted or sabotaged. One of the most effective strategies is to opt for cloud-based back-ups, which are easily managed and accessible. Typically, cloud data is stored in an encrypted format. As part of the encryption process, the data is pseudonymised by replacing easily identifiable information in data with unique symbols or characters.
- Full-disk encryption (FDE) – Disk encryption will encrypt every piece of data residing on a disk or disk volume via disk encryption software or hardware. Once you enable full disk encryption, no one is able to access the computer without the correct credentials. This makes FDE useful laptops and other small computing devices that can be physically lost or stolen.
- File-encryption/password protection – File encryption is typically used in conjunction with disk encryption to provide a more secure environment. File encryption encrypts individual files and does not decrypt them until an individual with the correct permission to view the documents accesses them.
Note: – Storing your data with a third-party cloud provider can be an additional security risk. If you are using a cloud service, check with your provider to ensure that data is encrypted both at rest and in transit.
3. Always transmit data securely
Businesses now operate in an age where an increasing number of employees are either working from home or on-the-go. This increases the need to transmit data securely and safely, whether it is to a supplier, customer, financial institution or the cloud. Using a VPN can help ensure information remains protected and private from prying eyes.
A VPN makes a secure and private connection over other less secure networks, like public Wi-Fi networks. This is done by encrypting the information you send and receive and then sending that encrypted information across an unsecured network. This way, data is protected against the possibility of unauthorised access.
There are several types of VPN. While some require a subscription, others are entirely free. If you’re looking for the best Internet privacy, however, you might want to consider a subscription to one of several VPN services available on the market.
4. Control access to data
Employees are often unpredictable, and it is, therefore, crucial to have a business-wide strategy for data privacy and security, including regular training and protection on every level. Of all the security threats, the most difficult to anticipate is human error, with employees being one of the most significant risks to cybersecurity.
- Role-based access (RBC) – Role-based access-based authentication is a method of restricting system access to only those who have been assigned to perform a specific action. RBC can significantly simplify administration by grouping employees together based on their job roles. RBC also prevents new employees and contractors not be inadvertently being granted access to systems they should not have access to, potentially putting the business at risk.
- Secure passwords and a password manager – Using ‘weak’ passwords can leave a business vulnerable to hackers. Strong passwords will help ensure accounts stay private and secure keeping sensitive information away from cybercriminals. Using a password manager will provide secure client-side encryption, while still being accessed by multiple users at any given point in time. Password managers can also be used to allow access to information only on an as-needed basis, and revise access rights when employees leave.
- Multi-Factor Authentication (MFA) – MFA, also referred to as two-factor authentication (or 2FA), requires users to present two pieces of evidence for authentication. MFA helps protect businesses by providing an additional layer of security, making it more difficult for malicious actors to breach accounts.
5. Integrate data privacy and protection into your organisational culture
Organisations handling Personally Identifiable Information (PII) must adopt and integrate data privacy and protection throughout the business at all levels to ensure the data is stored securely and appropriately disposed of.
This will ensure that when data is no longer required, confidential and sensitive data is handled in line with data privacy regulations, such as PCI DSS, to avoid audit failures or, worse still, cybercrime.
- Have an information security policy – An information security policy will help the business operate effectively, by providing a framework for assessing cybersecurity risk. Typically, such a policy is segregated into sub-topics, focusing on areas such as theft, unauthorised access and improper use. Without an information security policy, businesses may be putting their data in danger.
- Regularly audit your data and data controls – By regularly auditing data and associated controls, a business can determine whether the controls, policies and procedures meet the compliance requirements and, if not, where they need to be improved.
- Educate your employees – Educating employees, suppliers and customers on best practices for data privacy and protection will teach them to avoid compromising activities and scams, and encourage them to be an active participant in maintaining and monitoring data privacy and security.

