What is Cloud Identity Management?

On this page:
What is Cloud Identity Management
Definition and Overview
Cloud identity management provides a complete, centralized framework for managing user identities and orchestrating access and permissions across multiple cloud applications.
By centralizing user provisioning, authentication factors, and access control, this method offers a streamlined experience for users and administrators alike.
Key components include shared processes such as user provisioning, which automates adding and removing users, and secure authentication methods like Single Sign-On (SSO).
SSO enables users to log in to various cloud apps using one set of credentials, significantly enhancing the login experience.
Cloud identity management systems also integrate seamlessly with current IT infrastructures, which is essential in a secure cloud environment.
This integration saves time and cuts costs while bringing automation to processes like onboarding and offboarding users through centralized platforms, including the Google Admin console.
Transitioning from traditional identity management systems to cloud identity management solutions is a game-changer, largely due to scalability.
These robust identity management solutions provide flexible, scalable options that evolve and expand with your organization’s specific security needs.
Solutions such as JumpCloud Directory as-a-Service™ offer an encrypted, seamless, and secure connection to devices, applications, and networks, continuously evolving to meet today’s business demands and ensuring effective access management solutions.
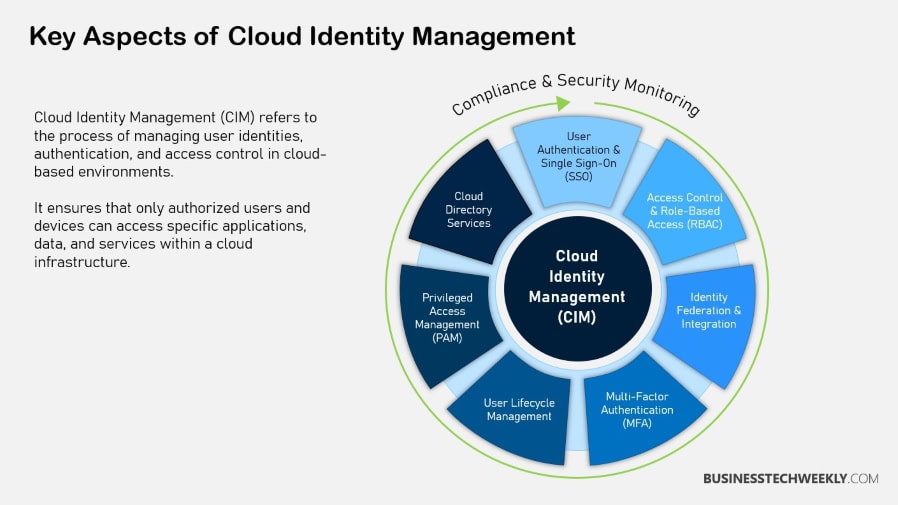
Importance in Modern IT Environments
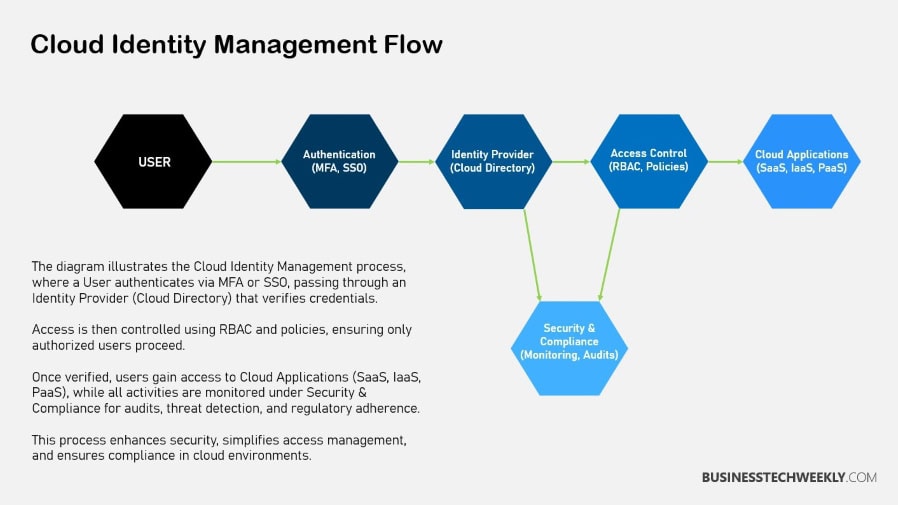
As businesses increasingly move to a tech-centric environment, cloud identity management plays a key role in enabling a remote workforce.
By protecting secure access to apps anywhere, it helps keep employees productive and engaged no matter where they are.
To put it simply, this technology improves user experience with passwordless authentication solutions, eliminating the friction users are used to.
In addition, cloud identity management is key to achieving and upholding compliance with stringent data privacy regulations.
Now that 80% of organizations use cloud services, compliance with these regulations through proper identity management is more important than ever.
Security is the other foundation of cloud identity management. It safeguards against unauthorized access and data breaches with strong default security such as multi-factor authentication (MFA) and secure self-service password reset.
These features are key to protecting sensitive cloud environments and ensuring people have the right permissions to do their jobs.
By using automated provisioning and deprovisioning, organizations can quickly adapt user access to changing needs, reducing potential security risks and improving operational efficiency.
Key Features of Cloud Identity Management
1. Multi-factor Authentication Explained
MFA is a key feature of cloud identity management. Multi-factor authentication also increases account security by adding multiple layers of verification to ensure that a user’s identity is legitimate.
Common methods are push notifications, SMS code and hardware security keys.
By using MFA, organizations significantly reduce the chances of account takeovers, ensuring a strong protection against unauthorized access.
This assurance helps to safeguard even the most sensitive information while also strengthening user trust as they access important applications.
Cybercrimes can average $9.44 million in losses per incident for U.S. Companies. In this high-stakes environment, MFA is your best line of defense.
RELATED: Why MFA Cloud Security is Critical for Your Business Data Protection
2. Single Sign-On Benefits
Single sign-on (SSO) enhances user experience and security by allowing users to access multiple applications with one set of login credentials.
This capability is a huge boost to productivity, enabling employees to seamlessly move from app to app without having to log in over and over.
Security benefits include decreasing password fatigue, encouraging better password hygiene.
Especially in remote work environments, SSO ensures users have constant access to their cloud and on-premises apps.
That’s because it works well with your current technology stacks and workflows.
In addition to being a cost-efficient solution, the scalability provided by cloud IAM with multi-tenant capabilities makes this a smart solution for any business large or small.
3. Understanding Endpoint Management
Cloud-based endpoint management is vital to protecting the devices that are used in–or to conduct the work of–an organization, while simultaneously keeping those devices secure and compliant.
Centralized console management increases visibility and control across all endpoints.
This improvement allows greater enforcement of security policies without slowing down application deployment.
A must-have feature like remotely wiping company data from lost or stolen devices is crucial.
This important, proactive step prevents sensitive information from getting into malicious hands.
Cloud Identity Free serves as a core solution for managing users and endpoints, even for those not utilizing Google Workspace services.
In 2022, 98% of monitored cloud tenants were targeted by brute-force or precision attacks, underscoring the critical need for robust Cloud IAM solutions.
4. Context-Aware Access Controls
Context-aware access controls improve security by using adaptive measures based on user activity, like their location and type of device.
All these controls are fundamental for deploying a zero-trust security model.
In this never-trust model, we do not assume trust; we just assume the need to evaluate every access request rigorously.
By providing the ability to implement granular access controls, organizations can help reduce the risks associated with unauthorized access.
This ensures that permissions are always automatically aligned with user context.
This flexibility also helps organizations avoid the potential security stumbles of lackluster identity management and comply with industry best practices.
5. Access Control Recommendations
To better implement the principle of least privilege in your access control policies, routinely audit and revise permissions according to user roles.
Use automated tools to make permissions easier to manage, lightening the administrative load.
Training staff on best practices is vital in mitigating security risks, ensuring that employees understand the significance of their access privileges.
Cloud IAM solutions provide fine-grained access control.
They automatically keep permissions up to date, whenever roles or places change, creating a more resilient security framework for you.
RELATED: Top 5 Identity and Access Management (IAM) Best Practices
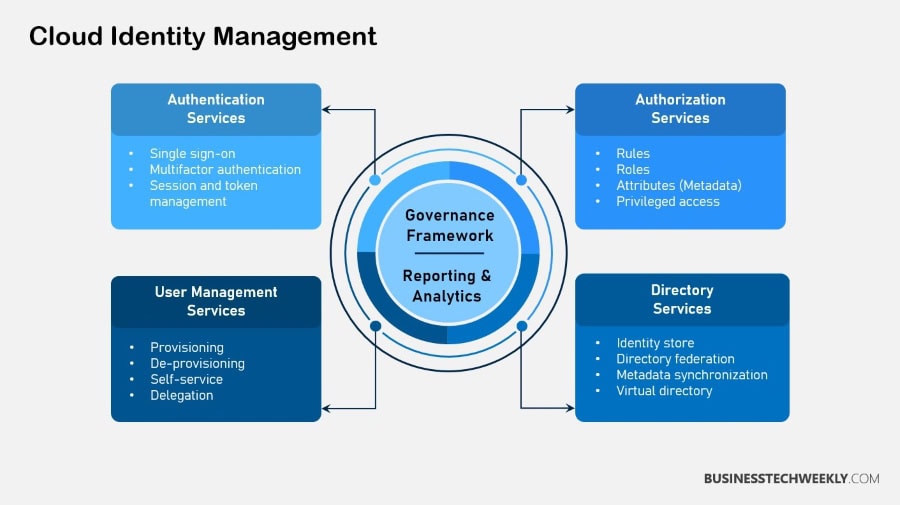
Benefits of Cloud Identity Management
The benefits of cloud identity management are continuously helping organizations thrive. It allows them improve their efficiencies while increasing their security posture.
Implementing these solutions allows organizations to strengthen access control, enhance security, and maintain compliance with regulatory requirements.
This strategy streamlines the process of user management and offers a scalable, adaptable solution that grows with your organization.
Enhanced Security Measures
Cloud identity management is a crucial tool to improve security with capabilities, including multi-factor authentication (MFA) and context-aware access.
MFA increases security by asking users to confirm their identity. They should be able to authenticate user identities through second-factor authentication, such as one-time passwords or biometric data.
This minimizes the chances of unauthorized access and potential data breaches. The strategy is further reinforced by round-the-clock monitoring, which helps detect and eliminate threats in real time.
By integrating security policies into the identity management strategy, businesses can protect sensitive data and maintain a robust security framework.
Simplified User Access Management
The degree to which user access processes can be automated is an impressive benefit of cloud identity management.
By automating these processes, organizations can save time on administrative tasks and boost productivity.
A single, centralized identity management system streamlines user provisioning and de-provisioning, making it easier to manage identities from their creation to their eventual removal. This new approach facilitates a better user experience by enabling SSO capabilities.
Users win by getting fast access to the applications they need most without compromising security.
As of 2022, the majority of IAM solutions are deployed on-premise, comprising a substantial market share of 58%, indicating a prevalent preference for organizations to maintain IAM systems within their infrastructure.
Improved Compliance and Audit Trails
Cloud identity management solutions are vital for compliance.
By controlling who has access to sensitive information, they help organizations stay compliant with data protection regulations like HIPAA and GDPR.
Comprehensive audit trails are crucial for tracking user access and activity, giving you a complete user overview for audits.
Additionally, these automated reporting capabilities aid organizations in their compliance efforts, eliminating the manual effort and improving accuracy in reporting.
This increased capacity to track and manage detailed records improves the organization’s capacity to quickly respond to regulatory requests.
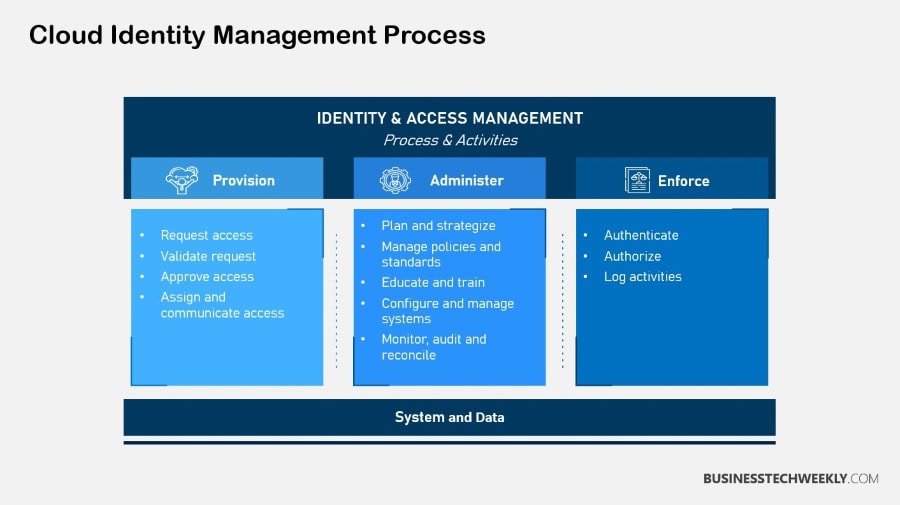
Active Directory User Provisioning
Active Directory (AD) user provisioning is one of the most important aspects of ensuring the proper control over user identities in organizations today.
This process involves creating, updating, and maintaining user accounts within a directory, ensuring that employees have access to the resources they need.
When you connect Active Directory to cloud identity platforms, you create a more seamless onboarding experience for users that spans cloud and on-prem.
This integration has made the onboarding of new employees a breeze. Now they are able to hit the ground running with immediate access to the applications and systems they need.
Automating user provisioning processes removes the risk of manual errors. This increase in productivity is what makes it such a valuable tool for IT departments.
Role in Streamlining Access
Active Directory user provisioning makes on-boarding new hires fast and easy by automating the account creation and access assignment process.
A single, authoritative directory that controls the user account and access permissions streamlines how you can control who has access to what.
Automated synchronization between Active Directory and cloud identity systems also makes sure that access rights are never stale.
This level of automation ensures users have the right access from day one, reducing downtime while also getting them productive faster.
Integration with Cloud Identity Systems
Connecting Active Directory to cloud identity management systems improves security and efficiency. It provides users with seamless access to both cloud and on-premises applications with a single identity.
This integration ensures user information is always up-to-date on every platform.
In doing so, it greatly reduces the threat to unauthorized access due to stale user data.
Keep AD user provisioning in its own OU. Alternatively, you can limit users to certain groups to keep very tight control over who has access.
In addition, synchronization updates made to the source system are regularly pushed, keeping both systems in sync.
Best Practices for Cloud Identity Management
Implementing Smart Access Control
Smart access control utilizes technology to inform the best decision regarding access management solutions.
It governs who receives access to what resources in your secure cloud environment. This zero trust model enhances security by continuously evaluating user behavior and context to determine appropriate access to cloud resources.
RELATED: Zero-Trust Network Access: Designing a Zero Trust Network
By employing user behavior analytics, you can learn the normal patterns and identify the unusual.
This powerful insight allows you to make informed decisions about when to grant or deny access.
For instance, if an employee attempts to access sensitive data during nonstandard work hours, the cloud identity management platform can rapidly identify this as anomalous, subsequently triggering additional verification measures to maintain security.
Adaptive security measures are key components of modern cloud identity management solutions. They dynamically change who gets access to what and when, adapting to shifting contexts such as location or personal devices.
This flexibility is what makes cloud IAM so powerful—ensuring that access decisions are contextually aware, timely, and secure.
Smart access control reduces the risk of insider threats by up to 75%. It provides access only when needed, leveraging a profound insight into the patterns of user behavior and user requirements.
Establishing Flexible User Roles
User roles are crucial in addressing the diverse job functions within an organization, especially in the realm of cloud computing.
Role-based access control (RBAC) simplifies permission management by organizing users into groups based on their roles, granting them the necessary access to perform their jobs effectively without exceeding their permissions.
This method enhances the enforcement of the principle of least privilege, which is vital for maintaining a secure cloud environment and meeting specific security needs.
Regularly recertifying user roles is essential to ensure they remain relevant to today’s responsibilities, as roles and job functions evolve.
Implementing a cloud IAM solution can streamline this process, allowing security teams to manage access effectively and adapt to changes in real-time.
Additionally, transparent communication regarding role changes is critical for maintaining robust identity management and ensuring proper security measures are in place.
Such transparency not only enhances user awareness of their access but also fosters trust and compliance among employees.
By leveraging cloud identity management tools, organizations can ensure that their access policies are up to date, ultimately contributing to a more secure digital infrastructure.
As of 2022, 73% of organizations operate in a hybrid environment, utilizing both cloud and on-premises systems, while only 19% rely exclusively on on-premises systems.
Ensuring Enterprise Identity Simplicity
Enterprise identity management should be simple. It provides for a better user experience by making it easy for users to get to the resources they need without jumping through unnecessary hoops.
A unified identity platform unifies multiple identity management functions.
This reduces friction in operations and allows end users to have more control over their access.
This combined effort continues to minimize the burden of juggling multiple logins and passwords, increasing user convenience and productivity.
Minimizing complexity in user access processes leads to better user adoption and satisfaction.
When users experience the system as easy to navigate, they are empowered. This confidence boosts their chances of adhering to security measures and actively engaging with the system.
Making identity management smarter and simpler increases productivity while improving security by minimizing potential user mistakes.
Choosing a Cloud Identity Solution
When you’re considering your options for a cloud identity management solution, there are a lot of factors to take into account. These factors can have a significant influence on your organization.
Second, evaluating vendor support, training and flexibility will be key.
Consider the quality of support offered by potential cloud identity solution providers.
Responsive customer support goes a long way in improving your overall cloud experience.
A provider’s ability to adjust to your evolving needs is just as crucial.
Scalable solutions ensure your organization can expand, evolve, and respond to changing needs.
More importantly, they make sure you stay agile and able to tackle whatever challenges the future may hold.
For instance, with Google Workspace you get a built-in, seamless SSO experience, which can reduce friction for users while enhancing security.
Cost vs. Value
The cost vs. Value of cloud identity solutions is an equally important factor.
A transparent framework for evaluating cost-effectiveness should take into account more than just upfront costs and look at value in the long-term.
Cloud identity management can deliver real cost savings by not just enhancing security but also reducing the costs of access management through greater efficiencies. IAM, or Identity and Access Management, is the cornerstone of your cybersecurity strategy.
Through an investment in a robust solution such as the JumpCloud Directory Platform, you’ll be able to securely facilitate user access to both VPN and Wi-Fi networks—improving your operational efficiency in the process.
Because companies can easily expand or contract their usage, cloud solutions are often more cost-effective than on-premise solutions.
Choosing new cloud identity solutions that align with your organization’s policies is equally important. Ensure that any cloud identity management solutions you consider are compatible with your existing IAM policies.
This will allow you to minimize potential risks, such as preventing unauthorized access.
Robust documentation supports these practices, ensuring that policies are enforced to keep organizations in line with regulatory obligations.
Limiting administrative privileges as a general IT best practice helps to further limit attack surfaces and potential security vulnerabilities.
A cloud access manager will set up cloud IAM solutions. This ensures they play nicely with your company’s current apps and bolsters your security strategy.
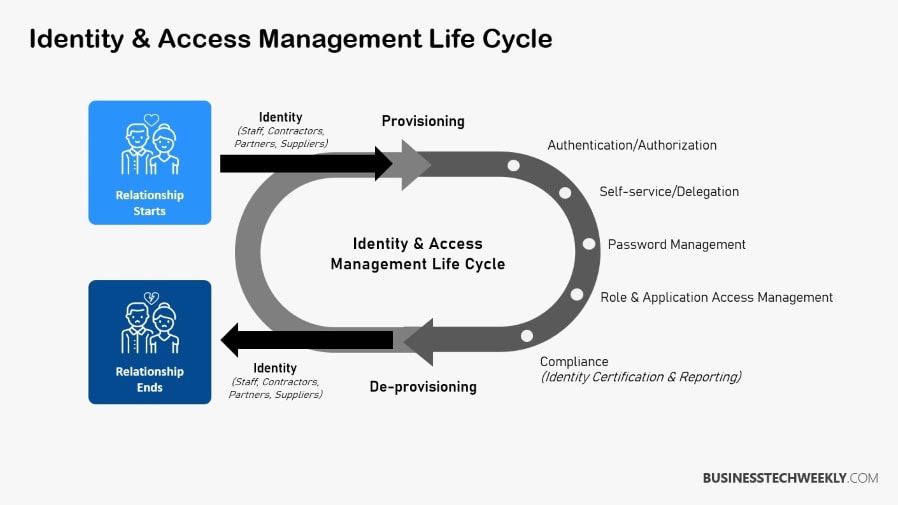
Key Points to Note
Cloud identity management is a critical resource in our increasingly digital environment. It provides you with flexibility and protection for your digital assets.
- Cloud identity management provides a more secure, centralized, and efficient approach to managing user identities and access across multiple cloud services. This method improves security while also enabling effortless collaboration across organizations.
- Multi-factor authentication and single sign-on are two security features that offer major user-friendly advantages. They improve overall security posture and simplify access management, especially for third parties, so you can minimize the risk of unauthorized access.
- Integrating cloud identity management with existing IT infrastructure streamlines operations, supports remote work, and enhances user experience through frictionless login processes.
- Implementing strong security practices is a key defense against data breaches. Adaptive, context-aware access controls are also essential for compliance with today’s stringent data privacy regulations.
- Best practices for cloud identity management include establishing clear access control policies, regularly reviewing identity strategies, and providing ongoing training for employees.
- When selecting a cloud identity solution, consider whether the vendor will support you with flexibility. Additionally, evaluate the cost vs value and make sure it fits your organization’s policies to get the best security level with operational efficiency.

