Zero-Trust Network Access: Designing a Zero Trust Network

As more and more employees prefer to work remotely and IoT devices flood networks and environments, it becomes increasingly important to verify devices and users accessing corporate data and applications. Zero-trust network access is one of the most effective ways to improve cybersecurity. A zero-trust approach to network access considers verifying each account, device, and the user attempting to connect to the organization’s systems before giving it access.
However, most organizations still stick to traditional security models and hesitate to embrace the zero-trust network architecture. This guide lets us understand how businesses can design a zero-trust network and implement secure access to their corporate network.
On this page:
What is a Zero-Trust Network Access?
Zero-trust network access is a technology concept that provides secure access to services and applications based on predefined policies. Zero-trust network access solutions only give access to services the user has been permitted.
Applying this model to network access lets organizations move away from the traditional VPN model, which offers unrestricted network access.
A Zero-trust model grants access to users on a per-session basis only after verifying the user and devices. The policy applies to users regardless of their physical location. The service, after verification, provides access to the application through a secure tunnel to offer an additional layer of security for corporate services and apps.
This type of network architecture includes several technologies already used by organizations for data protection. However, zero-trust takes a step further in cybersecurity defense. Instead of defending a single perimeter, it considers the system, network, users, and devices inside and outside the organization.

Zero-Trust architecture is facilitated by multi-factor authentication, strong identities, access controls, network segmentation, trusted endpoints, and user attribution to regulate critical data and systems access.
Benefits of Zero-Trust Network Access
The primary benefit of using a zero-trust approach to a corporate network is to ensure protection from all sides. Traditional security models focusing on protecting the network perimeter often fail as most of today’s breaches occur from inside, either from threats infiltrating the network through browsers, email, VPN connections, and other sources or by employees, knowingly or unknowingly.
Those who are given access to the network can easily intrude. Zero-trust handles this problem by taking away access from everybody until the network verifies the identity. Once authenticated, it continuously monitors how you use the system and may revoke some permissions based on what you intend to do.
Cybersecurity is today more critical than ever before. Executives are compelled to protect their systems and data against the growing number of threats. Investors, customers, and clients also insist on improving data security.
Cybersecurity becomes complicated when some data and applications are on the cloud and others on the premise. Employees, partners, and customers use various devices across locations to access them.
Government and regulatory bodies quickly revise their requirements to secure critical business data. Zero-trust network access helps show compliance to strict security regulations and gives the business an edge with a more robust cybersecurity strategy.

Principles of a Zero-Trust Network
As the name suggests, a zero-trust network is based on the principle that nothing and nobody is trusted until verified. The technology supporting this approach advances rapidly, making it more practical to deploy.
Several principles and best practices make up this security approach, and there is no single technology or approach for implementing this framework. Instead, technology components work together to ensure only authenticated devices and users can access critical data and applications.
Here are some of the main principles behind a zero-trust approach.
- Least-privileged access – This principle ensures users can access only the data they need to get their job done. This can be accomplished with one-time-use credentials and expiring privileges that automatically get revoked once access is no longer required. Such a practice minimizes the chances of data theft and prevents malware from moving from one system to another.
- Data usage controls – Usage controls limit what users can do with the data after accessing it. This is often done in real-time, like revoking permission to copy a previously downloaded file to another location.
- Micro-segmentation – This will divide the network into segments with different access credentials. It improves protection and keeps attackers away from the network even when one of the parts is breached.
- Proxies – Zero-trust proxies work as a relay between the client and the server, keeping attackers from invading a private network.
- Software-Defined Perimeter – This security framework is based on a strategy where the identity and posture of a device are verified before giving access to infrastructure.
Traffic on a network is continuously monitored and logged, and access is confined to predefined perimeters to prevent unauthorized data movement across the network.
A zero-trust network employs several technologies, including role-based access control, identity and access management, multi-factor authentication, network access control, policy enforcement, encryption, logging, file system permissions, analytics, and more.
Several technology standards and protocols supporting the zero-trust approach are also available. Some networks use the Software-Defined Perimeter (SDP) model developed by the CSA (Cloud Security Alliance).
Another framework is introduced by the Internet Engineering Task Force (IETF) in the form of the HIP (Host Identity Protocol) that adds an extra layer of security in the zero-trust security model.

Key Steps in Designing a Zero-Trust Network
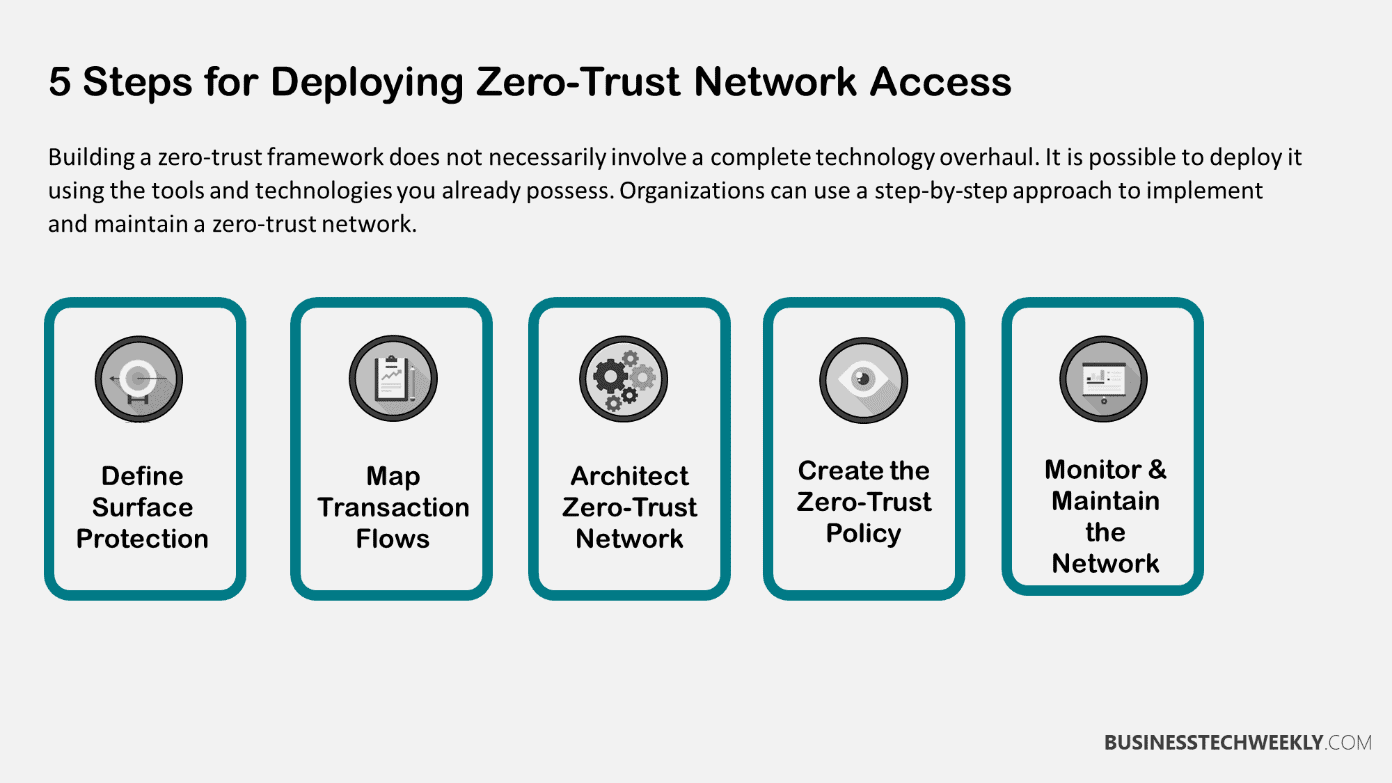
Building a zero-trust framework does not necessarily involve a complete technology overhaul. It is possible to deploy it using the tools and technologies you already possess. Organizations can use a step-by-step approach to implement and maintain a zero-trust network.
Define the Surface
Focusing on your attack surface is insufficient for a zero-trust network access framework. You must define your protect surface that comprises the most critical and valuable applications, data, services, and assets for your business.
Some protect surface examples include intellectual property, credit card details, point-of-sale terminals, IoT devices, Active Directory, and more.
After defining the protect surface, you can move the controls closer to build a micro-perimeter with comprehensive, precise policies.
Map Transaction Flows
How the traffic moves across a network decides how it should be protected. This is why you should acquire some information about the interdependence of your assets. Documenting how resources interact helps enforce controls and ensure security with minimum disruption to operations and users.
Implement a Zero-Trust Architecture
A zero-trust network is customized and does not follow a universal design. Such architecture is generally built around the protected surface. After defining the protected surface and transaction flows for your business needs, it is easy to map a zero-trust architecture with a firewall that creates a perimeter around the surface.
Such a gateway helps enforce additional layers of access control for anything trying to access the resources.
Craft Zero-Trust Policies
After a network architecture is created, you need to create policies for zero-trust access. To do this, you must identify who the users are, what applications they need access to, why they need access, what devices they use to access the applications, and what controls can secure the access.
Granular enforcement of policy helps ensure only legitimate connection to application is permitted, and only known traffic is allowed access.
Monitor and Maintain the Network
The final step involves reviewing internal and external logs and focusing on different operations associated with zero-trust. As it is an iterative process, logging the traffic gives valuable insights into how the network can be improved over time.
Best Practices for Zero-Trust Network Access
Let us discuss some best practices for organizations willing to adopt a zero-trust network access model.
- Before selecting a technology or architecture, it is vital to ensure you have the right strategy in place. A zero-trust approach focuses more on data, so you should consider where it lies, who requires access to it, and what approach can secure it. It is good to divide data into three segments – Confidential, Public and Internal.
- Consider starting small and gradually increasing your confidence. The scale for zero-trust implementation in an organization can be massive. Keep expanding the experience to proceed and achieve the targeted scope.
- Take into consideration the user experience. Implementing the zero-trust network approach should not disrupt employee functions even when verified. Most of these processes can be run in the background to be unaware of them.
- Implement strict measures for user and device authentication. The Zero-trust approach is based on the notion that nobody and nothing can be trusted until verified to have access rights. An enterprise-wide identity and access management system with strong identities, strict authentication, and dynamic permissions can be put in place.
- Include the zero-trust model in other digital projects. By redesigning processes, you can transform your cybersecurity model for better results.
Final Thoughts
While implementing zero-trust network access can seem overwhelming at first, it can be easily achieved with the right combination of practices, tools, and technologies.
There is no better time than now to adopt this security model. A new approach to cybersecurity helps organizations protect their customers, data, applications, and competitive advantage in this rapidly changing landscape of cyber threats.

