Top 5 Identity and Access Management (IAM) Best Practices

Ensuring you adhere to Identity & Access Management (IAM) best practices is vital to your organization’s cybersecurity.
The primary goal of IAM systems is to provide a single digital identity for each human or item. Once a digital identity has been created, it must be preserved and monitored throughout the access lifecycle of each person or device.
However, maintaining secure IAM can sometimes be incompatible with agility, mainly when experimenting with new technologies.
On this page:
What Is Identity and Access Management (IAM)?
Identity and access management (often abbreviated to IAM, or sometimes IdAM) is a set of policies, procedures, and technologies that enable you to bind an individual (or, in some cases, a system) to a group of rules within your system.
IAM systems are designed to perform three functions: identify, authenticate, and authorize. To put it another way, only authorized individuals should have access to computers, hardware, software apps, IT resources, or perform specific tasks.
These authorizations allow the individual to do the following:
- carry out tasks
- create, access, and modify data
- manage your system
The list of access privileges must be kept up to date and consistent regularly, whether new users are added or existing users’ roles are changed. IAM functions are typically handled by IT departments or cybersecurity and data management teams.
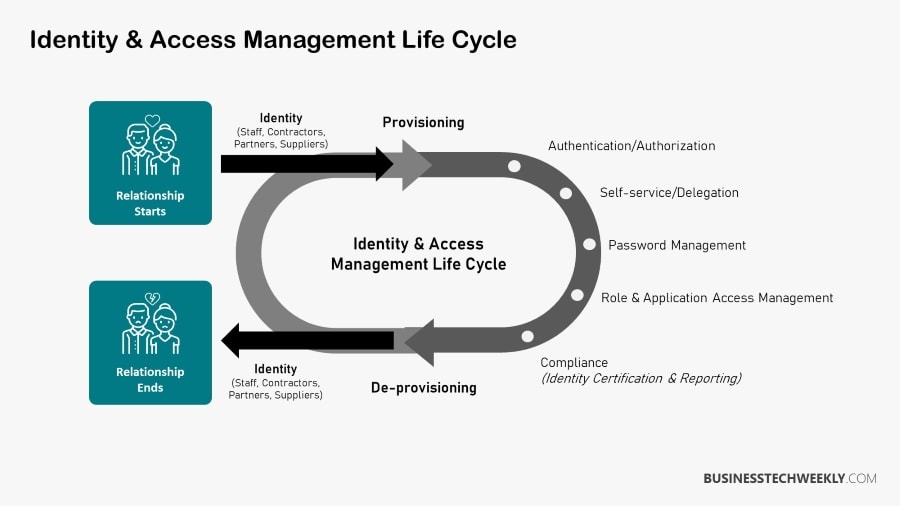
Identity and Access Management (IAM) Components
Regulating user access has conventionally involved authentication methods to verify a user’s or device’s identity, including passwords, digital certificates, hardware and smartphone software tokens.
Identity and access management, IAM, can be broken down into the following broad areas:
- Policy – your strategy defines who is authorized to access systems, data, or functionality, how they can request access when their access should be revoked, and whether any specific operations should necessitate the collaboration of several users.
- Process – the processes and technologies that facilitate detecting and investigating policy or control violations.
- Access – refers to the different processes and controls that should be put in place to protect the system’s most sensitive functions.
- Identity – refers to how you establish a person’s identity, both at the point of initial contact and later interactions with your systems or processes.
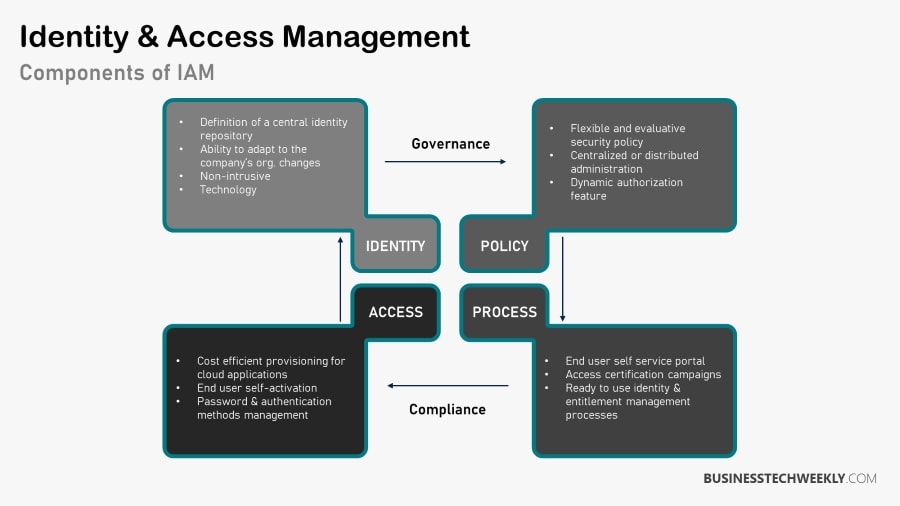
What are the benefits of IAM?
While we have understood identity and access management and the different types of Identity and Access Management systems, let us now delve into some of the critical benefits of identity and access management.
- Enhances Security – One of the significant advantages of IAM systems is improving data security throughout the enterprise. Companies can avoid any risk associated with a data leak by implementing limited access. IAM systems can also prevent unauthorized access to sensitive information and unauthorized access to any corporate data. Robust IAM systems can assist businesses in avoiding phishing attacks and protecting against ransomware.
- Improves IT processes and workload – When the security policy is modified, all-access restrictions across the organization are updated simultaneously. Implementing IAM can also reduce the number of support tickets the IT helpdesk receives.
- Supports Compliance Requirements – Implementing IAM can ensure that the firm adheres to all regulatory compliances, such as GDPR and HIPAA and best practices.
- Improves productivity through collaboration – Companies that deploy IAM systems can grant selective access to the system to external parties such as customers and suppliers without jeopardizing security measures.
- Enhances user experience – Implementing IAM systems makes it easier for users to remember complex passwords. SSO ensures a consistent user experience.
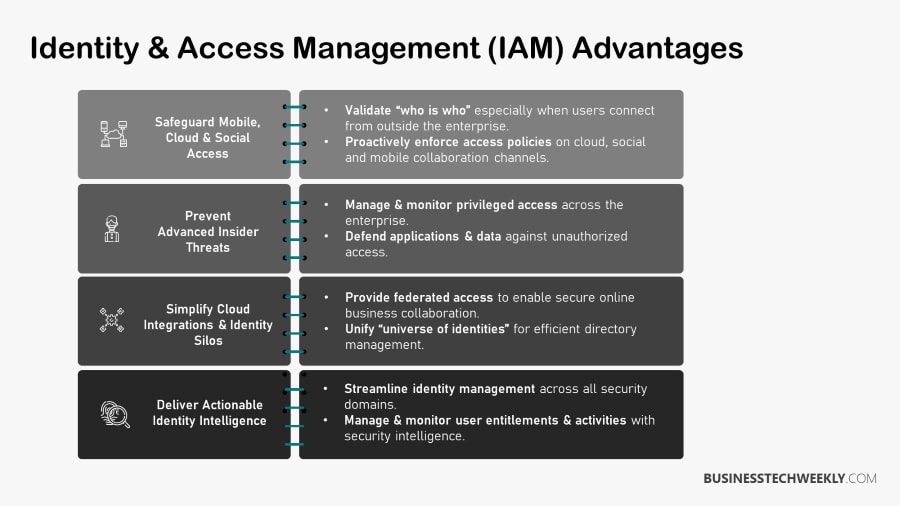
Identity and Access Management (IAM) Best Practices
The likelihood of a security breach can be considerably lowered by adopting IAM best practices such as multi-factor authentication and eliminating unused credentials with periodic audits.
The following (IAM) Best Practices will help you boost your identity management system to ensure better security, efficiency, and compliance and help you create a successful IAM implementation
1. Implement zero-trust security
In the dynamic environment of modern corporate networks, the best strategy is to assume that no one is trustworthy unless proven differently.
The zero-trust strategy is centred on constantly authenticating consumers—activities are tracked, and risk levels are assessed during each session. A device with zero trust is equipped to detect aberrant actions that indicate a breach or violation of the law.
RELATED: Zero-Trust Network Access: Designing a Zero Trust Network
2. Implement Role-based Access Controls (RBAC)
Numerous IAM systems provide role-based access controls (RBAC). The roles of these individuals are predefined in this technique. These roles come with predefined access rights. For example, if one person is in charge of training in the HR department, other members of the HR function will not have access to anything relating to training.
3. Deploy Single Sign-On
Implementing Single Sign-On is another method of enforcing IAM (SSO). With SSO in place, users need to validate themselves once. Once the authentication is complete, users can access all systems without logging in to each one individually.
If your organization uses single sign-on (SSO), to support password and IAM best practices, each user’s password must be unique and difficult to guess. Passwords must be complex enough to thwart potential cyber attacks, changed regularly, and not used for different sign-on requirements.
4. Use Multi-Factor Authentication
If additional authentication is required in addition to the existing approaches, businesses can use 2-Factor Authentication (2FA) or multi-factor authentication (MFA).
The authentication combines something the user knows, such as a password, and something the user possesses, such as an OTP (one-time-password).
If one of these authentication methods is compromised, an infiltrator still has at least one more obstacle to overcome before successfully getting into your system.
RELATED: How Multi-Factor Authentication (MFA) keeps business secure
5. Automate onboarding procedures
Self-service onboarding allows your customers to onboard themselves. The onboarding process frequently begins with a registration page. Your job is to get your customers beyond the registration page and onto the activation page. It also helps you retain them in the long run.
Automation also makes it simple to log, audit, and generate compliance reports regularly. This eliminates one of the most time-consuming manual processes many IT staff face.
Passwordless login, password reset, profile management, consent management, and preference management are other areas where automation can deliver.
Future of Identity and Access Management
As more businesses use mobile-friendly and cloud-based systems, the requirement for a safe and secure location to keep personally identifiable information becomes more critical.
Some emerging IAM technologies ensure that personalized information is restricted to the concerned user and not spread across databases within the organizations.
This means that a decentralized identity setup will ensure that every individual has control of maintaining their own identities. They can also control where personal data is shared, thereby reducing the risk at the corporate level.
IAM systems require constant innovation because there is an imminent threat of cyber-attacks as organizations go digital. IAM systems play a pertinent role in ensuring that such attacks (which are likely to be more in the future) can be evaded.

