10 steps to cyber security every small business must take

Whether you are managing your business’ cybersecurity directly, or whether you have outsourced to a third-party, if there is a data breach, the blame is on you. With online threats increasing, and new weakness targets being targeted all the time, the 10 crucial steps presented below, will be invaluable to small businesses in managing their cyber security.
You may think having a firewall, and a good IT company is sufficient, but are you willing to bet your business on that?
On this page:
Why small businesses are a target for cybercrime?
The gap between unprepared organizations and those that have added policies and processes like incident response plans, encryption, and employee training, is widening.
While small business owners may consider themselves too small to be a target, security by obscurity is never an effective policy.
The most likely reason why small and medium businesses are targeted is intelligence gathering. A successful attack could result in a data breach, providing the intelligence the attacker was seeking.
Data breaches can often provide several types of information that a cybercriminal may find useful, from documents and intellectual property, to credit card and financial data. In some cases, cyber attackers may even obtain information about you, your employees and customers.
Implementing the 10 steps to cyber security, presented below, will help deter any potential attackers from making your business a target.
See also: A guide to cyber security for small and medium businesses
How is your Business Impacted by a Cyber Attack
Failure to take concrete steps to bolster your organizational cyber security may drastically impact your business.
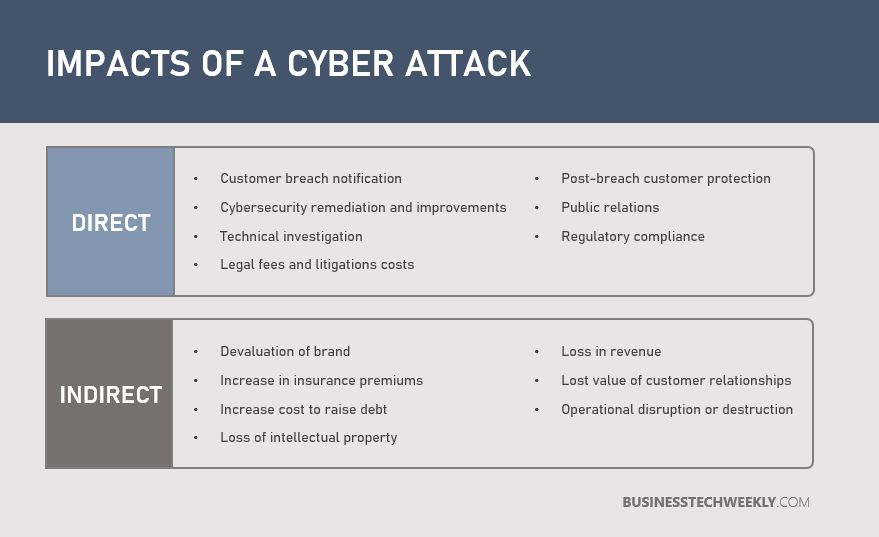
A significant data breach or cyber attack may result in direct and indirect expenses for your organization, as well as costs in terms of lost opportunity:
- Direct cost – the costs incurred to accomplish a specific activity, such as forensic investigations, setting up a customer hotline, or providing free credit monitoring subscriptions for victims, and offering customers discounts for future services and products.
- Indirect cost – time and effort spent by internal resources during and after a breach, for example, in-house investigations and communications.
- Opportunity cost – following a breach, the cost of lost business opportunities as a result of decreased brand reputation. The price of lost business opportunities could be significant if the beach has been publicly revealed to the media.
Why you should care about Cyber Security
Simply put, cyber attacks put your investment, data and IT systems at risk. If a cybercriminal gains unauthorized access to your systems, they could cause damage to the information they may find. These may include:
- Access customer details
- Obtain customer credit card data
- Access your company’s banking details
- Gain knowledge of your pricing strategy
- Steal product designs & expansion plans
- Illicitly obtain proprietary manufacturing processes
Such attacks don’t just put your business at risk, either. Hackers will use your network to access the networks of other companies in your supply chain. If your IT systems are found to be at the cause of a significant data breach, you may face claims for compensation in addition to any fines.
Following an attack, getting your business up and running again is only the first obstacle. Small organizations can face several repercussions if they fail to take the necessary steps to improve their cyber security:
- Business disruption – An attack on your systems may force you to segregate and close off parts of your business to prevent cyber criminals from accessing your data. By the time you investigate the cause of the breach and get your business online, you are likely to have experienced a loss in production.
- Remedial costs and regulatory fines – If the incident was severe, you need to contact affected customers and your data protection supervisory authority. In the UK, this is ICO (Information Commissioner’s Office). The ICO could decide that the incident violated the General Data Protection Regulation, in which case you may face a financial penalty and legal action. Notifying potential victims can be a time-consuming and expensive process. You may need to set up a support number, to enable those affected to learn more. You may also need to offer complimentary credit checks to provide assurance that the breach has no personal financial implications for them.
- Reputational damage – The incident could cause long-term reputational damage to your organization. Long-term reputational damage can make it challenging to retain customers’ trust – and that’s particularly true for small businesses.
10 steps to improve your cyber security
Cybersecurity threats are growing, both in number and complexity. Costs of a cybersecurity breach could continue to accumulate for many years after the initial incident.
Cybersecurity best practices should not only be established but kept up to date and followed to keep up with such versatile threats. Based on GCHQ guidelines, presented below are the 10 steps SMEs need to be taking to ensure better cyber security practices:
1. Implement Information Risk Management Capability
- Embed an organizational Information Risk Management practice to assess the risks to your organization’s information assets.
- Ensure IT risks are given the same level of importance accorded to legal, regulatory, financial or operational risks.
- Obtain support by the Board, senior managers and empowered information assurance (IA) structure for this iniative.
- Make your employees, vendors, and suppliers aware of your organization’s risk management processes, by communicating your risk management policy across your organization.
2. Ensure All Your Systems & Devices Are Securely Configured
- Develop and introduce policies and processes to ensure your devices are built to secure baselines.
- Make certain these policies and processes ensure the sensible use of your IT systems.
- Pro-actively manage the configuration and use of your IT systems, including the patching of systems against known vulnerabilities.
- Reduce your business’ exposure to threats and vulnerabilities, and decrease the risk to the confidentiality, integrity and availability of systems and data by removing or disabling unnecessary functionality from IT systems.

3. Prioritize Your Network Security
- When configuring your perimeter and internal network, follow industry best practices and design principles.
- Ensure all your network devices are configured to a secure baseline build.
- Configure devices to filter all traffic at the network perimeter, only allowing traffic explicitly needed to support your business.
- Implement traffic monitoring and ensure alerts are set up to inform you of any unusual or malicious incoming and outgoing activity that could indicative of a potential attack attempt.
4. Manage User Privileges
- All employees accessing your systems and data, must only be provided with the level of access needed to do their job.
- Privileged accounts, such as system or database administrators, must be controlled to prevent these accounts from being used for high risk or day-to-day user activities.
- User activity should be monitored, particularly access to sensitive data and privileged account actions (such as creating new user accounts, changes to user passwords and deletion of user accounts and audit logs).
5. Increase User Education And Awareness
- User security policies should describe and promote the acceptable use of your organization’s systems.
- These policies should be formally acknowledged by the employee in the terms and conditions of their employment.
- All employees must receive regular cyber security training, to promote secure practices and principles, and provide guidance on the cyber risks they face as users and individuals.
- Some specialist training may be required for security-related roles (such as system administrators, incident management team members and forensic investigators).

6. Implement Incident Management Capabilities
- Your incident management plans (including disaster recovery and business continuity) must be regularly tested and updated to ensure their validity (in particular, to account for the introduction of new systems or new starters or leavers).
- Specialist training across a range of areas, both technical and non-technical, may be required for your incident response team.
- Any online crimes must be reported promptly to the relevant law enforcement agency to help build a national view of potential threats.
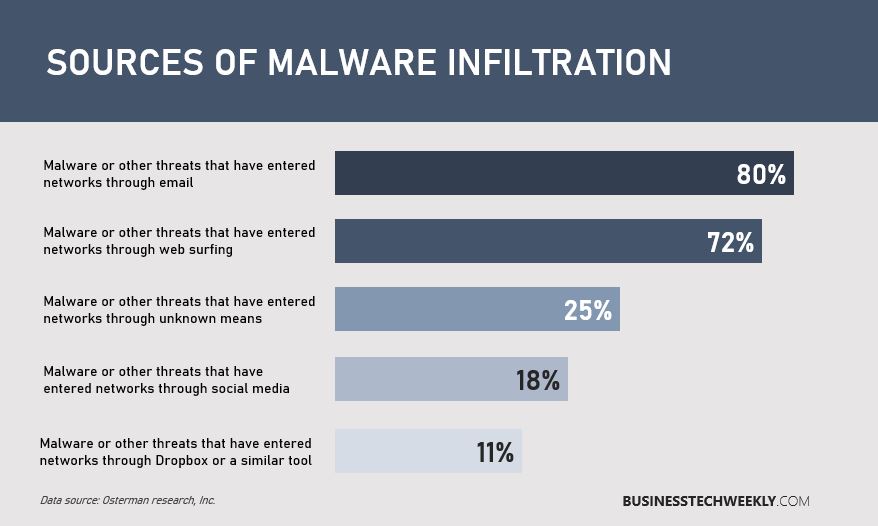
7. Take Steps To Protect Against Malware
- Implement policies to address business functions (such as email, personally owned devices, removable media and web browsing) which is susceptible to malware.
- Protect all devices and systems with antivirus solutions, and enable regular, and active malware scanning your organization.
- Scan any data and information, digitally transferred to and from your organization, for malicious content.
8. Enable Monitoring
- Take into consideration previous security incidents and attacks to establish an approach to monitoring.
- Develop supporting policies, taking into account your organization’s approach to incident management.
- Constantly monitor network traffic, both inbound and outbound, to identify unusual trends or activity which may be indicative of an attack and potential data breach.
- Use Network and Host Intrusion Detection Systems (NIDS/HIDS) and Network and Host Prevention Systems (NIPS/HIPS) to monitor all your IT systems.
9. Employ Controls for Removable Media
- Employ controls, via policies, for removable media, including the use of removable media for the transfer of information.
- If using removable media is unavoidable, apply limits to the types of media that may be used together with the users, systems, and types of information that can be transferred.
- Use a standalone media scanner, to scan all removable media for malware, before any data is transferred onto your systems via removable media.
10. Develop Security Measures for Remote working
- Assess the risks for all remote workers, and develop adequate security policies. Educate remote workers and mobile users on using their mobile devices securely.
- Apply the secure baseline build to all types of mobile devices used. Protect data-at-rest using encryption (if the device supports it) and protect data in transit using an appropriately configured Virtual Private Network (VPN).
Why you should implement these 10 steps to Cyber Security?
A majority of IT professionals have experienced at least one data breach, and on average have handled six breaches over the course of their career. Nearly 75% of all breaches have required public disclosure or have impacted financial results, with 60% of small businesses that experience an attack shut down within six months after the breach.
While the 10 steps to improving your cyber security outlined above won’t stop attacks completely, they will provide a significant hinderance to any malicious intent.

