GRC Cyber Security: Understanding its Importance

On this page:
What is GRC?
GRC is an acronym for Governance, Risk Management and Compliance. It’s a cohesive framework that assists organizations in developing core competencies to manage their cybersecurity efforts.
GRC cyber security strategies help businesses align risk management with compliance regulations, ensuring a proactive approach to cyber threats. Integrating these three pillars enables enterprises to develop an organized approach to processes.
This method fosters accountability, reduces cyber threats, and guarantees adherence to legal standards.
This approach reduces uncertainty and aligns security efforts with broader business objectives, making it a critical component for companies navigating today’s complex digital landscape.
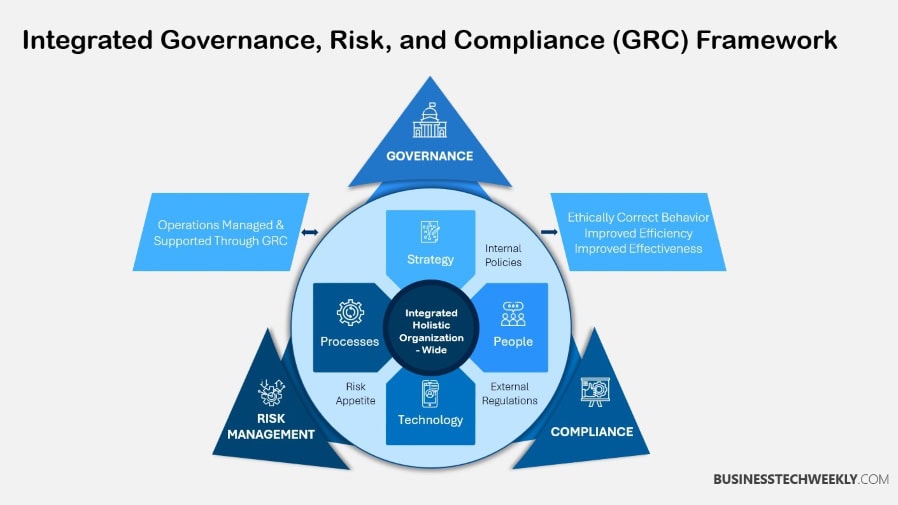
Define Governance
Governance in the context of cyber security is about defining who is responsible for what, how decisions are made, and what data informs those decisions. Most importantly, it creates accountability by setting out clear roles and responsibilities.
With this approach, each member of the organization understands their role in safeguarding the organization’s digital resources.
The Chief Information Security Officer (CISO) or similar title is responsible for the implementation of security controls. In the background, team leads are responsible for keeping compliance in check for their departments.
These policies not only lay out a decision-making framework, but establish firm principles guiding everything from procurement processes to cybersecurity practices.
For example, a company might decide to adopt a policy requiring all sensitive data to be encrypted.
Here, the action taken ensures that the communication is secure both in transmission and when stored. Access controls are very important to have when it comes to governance, protecting sensitive data from outside eyes.
By adopting preventative actions such as multi-factor authentication (MFA) or role-based access controls, enterprises can reduce their risk of being breached.
Standard operating procedures (SOPs) ensure uniform security protocols. They walk you through incident response and day-to-day operations in a way that’s easy to understand and apply.
Define Risk Management
Risk management focuses on identifying and addressing potential cybersecurity threats. Organizations begin by conducting comprehensive risk assessments, evaluating vulnerabilities such as outdated software or unpatched systems.
For example, a financial organization might assess risks tied to phishing attacks targeting employee emails.
Once risks have been identified, the severity of risk is evaluated so that the most severe risks are addressed first.
High-severity risks, including ransomware dangers, take priority action to security measures like endpoint detection mechanisms.
Mitigation efforts include the deployment of firewalls, intrusion detection systems, and frequent security awareness training to employees.
Continual monitoring is key to getting ahead of a constantly changing threat landscape.
Automating the process with automated tools can monitor system performance and identify anomalies, allowing organizations to quickly address new risks.
A strong GRC Cyber Security framework enhances this approach by integrating continuous risk assessments and compliance tracking, ensuring ongoing protection against cyber threats.
Define Compliance
Compliance makes sure that an organization adheres to external regulatory requirements as well as internal guidelines and protocols.
External regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) mandate organizations have certain cybersecurity standards in place.
These measures are all critical for protecting individuals’ data privacy.
The GDPR, for example, mandates that companies must get explicit consent for any processing of personal data. Internal compliance protocols reinforce organizational integrity by aligning practices with business goals.
This entails crafting policies specific to the organization’s workflows, such as data retention practices or employee access responsibilities.
To stay compliant, organizations must continuously monitor, re-evaluate and revise their standards and procedures.
An example of such an audit is a retail business, concerned about fraud, that audits its payment systems every year. This dramatically increases their chances of meeting Payment Card Industry Data Security Standards (PCI DSS).
Regular reviews ensure these initiatives remain compliant with changing regulatory requirements, and they allow organizations to build credibility and confidence with stakeholders.
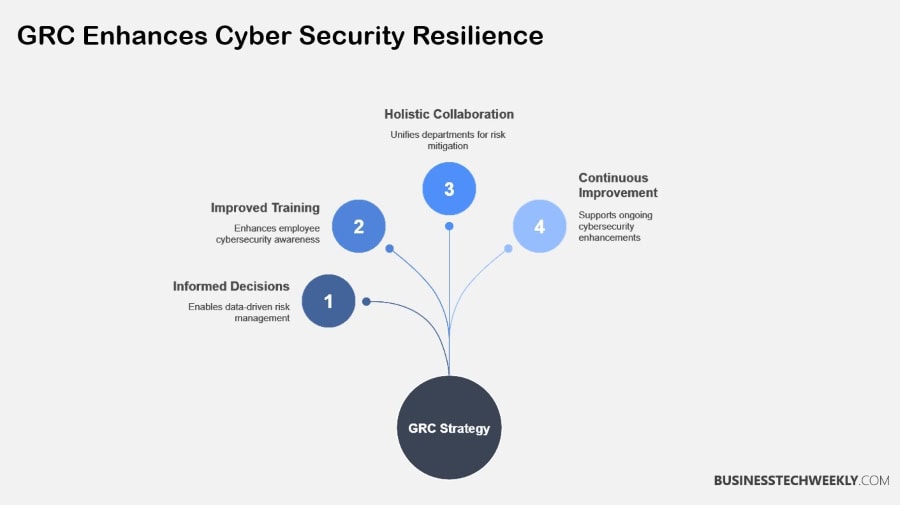
Why GRC in Cyber Security Matters
Governance, Risk, and Compliance (GRC) is not simply a regulatory checkbox—it’s a strategic imperative in the current cyber security landscape. It is more than avoiding fines and stopping breaches from occurring.
GRC provides a more systematic and holistic way of aligning cyber security to business objectives, fostering a culture of ethics, and preparing for emerging threats and regulations.
A well-structured GRC Cyber Security framework enables organizations to maintain compliance while proactively mitigating risks associated with evolving digital threats.
Data-Driven Cybersecurity Decisions
Mature and effective GRC capabilities give organizations the ability to make more informed, data-backed decisions to support their mission.
By leveraging quantitative measures like incidents per month, time to resolution, and compliance index, your risk management strategy effectiveness can be evaluated.
This strategy enables you to measure the value and adequacy of your security investments, allowing for better allocation of limited resources.
By analyzing historical data, organizations can identify patterns in threat vectors and be better positioned to predict and preempt recurring vulnerabilities.
For instance, an organization that notices an increase in phishing attempts around financial reporting time can ramp up email security efforts during those intervals, enhancing their overall security posture.
Technologies such as machine learning-powered analytics take cyber risk management capabilities a step further by rapidly prioritizing and remediating security threats.
These AI-driven systems analyze vast amounts of network data to find anomalies in real-time, significantly decreasing response times and improving risk management processes.
A data-driven culture contributes to higher levels of transparency, ensuring that decision-making isn’t siloed—it permeates every level, from executives to IT teams.
This approach not only increases cybersecurity maturity but fosters greater confidence among all stakeholders involved in compliance activities.
Ransomware now accounts for 35% of all cyberattacks, an 84% increase from the previous year. This surge highlights the critical role of GRC frameworks in preparing for and responding to such pervasive threats.
brightdefense.com
Promote Responsible Cyber Operations
GRC excels at encouraging a culture of security throughout the organization.
Human behavior is still the weakest link in our cybersecurity posture, and human error is responsible for nearly a third of all breaches.
Customized training programs can arm your team with relevant, actionable knowledge that they can directly apply within your industry.
They’ll become better equipped to identify phishing emails and protect sensitive data.
Transparent reporting structures for security issues promote responsibility, avoiding delays in response when a vulnerability is discovered.
For instance, creating a dedicated reporting platform will help employees communicate issues faster to IT, preventing time lost with slow response times.
When employees believe they have a hand in creating cybersecurity policy, it improves the organization’s complete defensive stance against cyber threats.
Strengthen Overall Cybersecurity Posture
Holistic security practices are the foundation of an effective GRC initiative.
Maintaining regularly updated mechanisms, whether that’s establishing a patch management policy or preset endpoint security configurations, fortifies the organization’s posture against new threats that develop.
Real risk mitigation collaboration between departments—legal, finance, and IT—creates a unified front, addressing the risks holistically.
Integrated platforms such as Drata make these processes easier, automating compliance-related processes and tracking the impact of initiatives on compliance metrics.
By measuring outcomes, we can create a continuous improvement process that allows cybersecurity to better support overall business objectives.
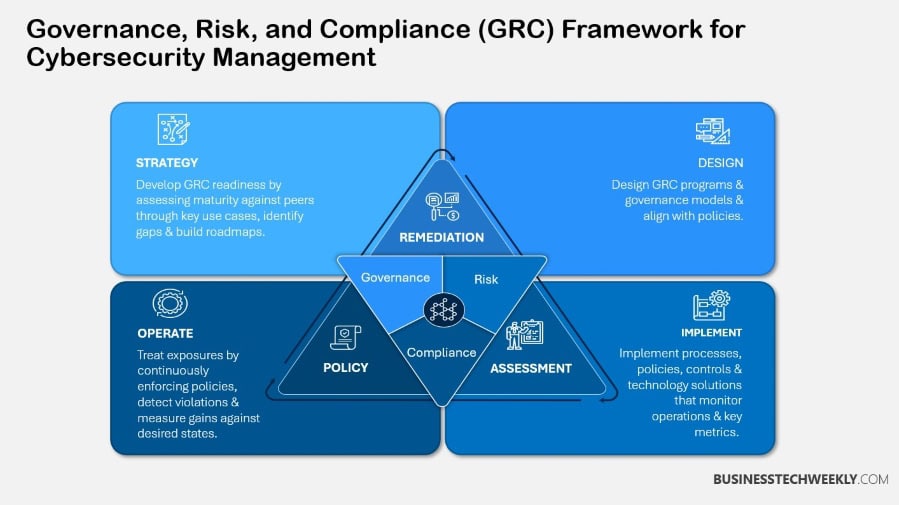
Drivers Behind GRC Implementation
Implementing Governance, Risk Management, and Compliance (GRC) practices has become a vital strategy for organizations navigating today’s complex cyber security environment.
The necessity for GRC stems from a combination of regulatory pressures, an evolving threat landscape, alignment with business goals, and the engagement of key stakeholders.
Together, these drivers help ensure each corner of the puzzle positively contributes to a GRC framework that is inclusive, comprehensive, and effective.
Regulatory Pressures
The increasing complexity of regulatory demands is a major driver pushing enterprises to implement GRC.
Mandates such as GDPR, HIPAA, and industry-specific standards require organizations to manage data responsibly, secure sensitive information, and demonstrate compliance.
Failing to do so typically leads to heavy financial and brand-related consequences that can diminish stakeholder trust.
For example, the General Data Protection Regulation (GDPR) allows up to 4% of your company’s global annual turnover in penalties for violations.
Organizations stand to gain from being on the front foot with their compliance efforts by regularly monitoring regulatory developments and repositioning their efforts to stay compliant as guidelines evolve.
This strategy not only mitigates risks, but cultivates a robust culture of accountability.
For instance, in the financial sector, firms increasingly adopt automated compliance monitoring systems to maintain real-time compliance with regulatory requirements.
This measure protects both against possible future penalties and builds market credibility.
Evolving Threat Landscape
Cyber threats are changing every day, with attackers using more complex techniques like AI-enabled malware and social engineering.
This shifting terrain requires a proactive, adaptable GRC framework focused on future threats and vulnerabilities not yet realized.
Threat intelligence solutions, as an example, enable organizations to take proactive measures by leveraging actionable insights to better understand and address potential risks before they escalate.
Collaboration is the third key ingredient. Organizations that share threat intelligence through industry information-sharing and analysis centers, or ISACs, are able to identify and mitigate attacks more effectively.
Healthcare companies that deploy and administer IoT-enabled devices face distinct threats. They receive massive benefit in exchange for returning information on vulnerabilities unique to medical technologies.
Business Needs and Objectives
Aligning GRC with core business objectives ensures that cybersecurity efforts support broader organizational goals. Similarly, e-commerce supply chain tools that optimize for a secure payment process lead to more progressive customer trust and continued revenue generation.
It takes partnership between cybersecurity teams and lines of business to embed risk management into the day-to-day operations of the organization.
Equally important as implementation is the ongoing review and update of any GRC strategies.
This allows for future-proofing against changing priorities, like adopting new technologies or expanding operations.
They are seeking to ensure they are prepared for future technology investments.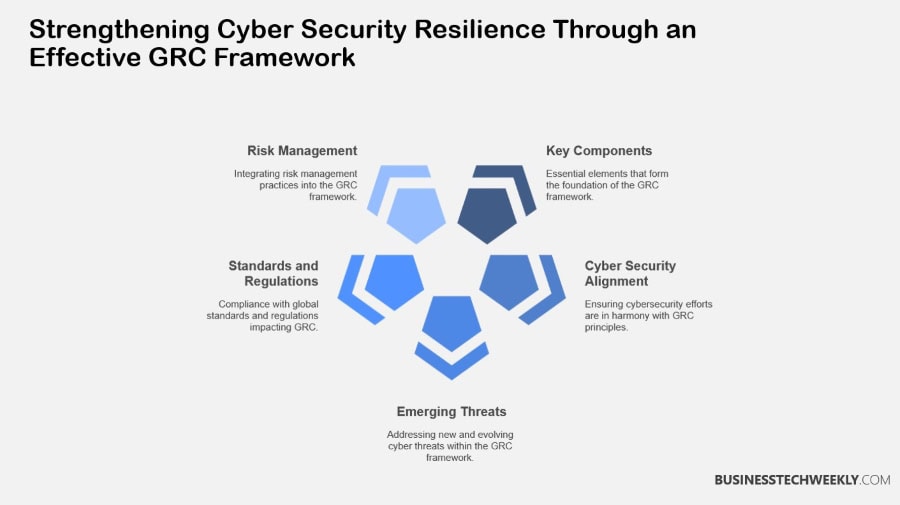
How Does GRC Work?
A Governance, Risk Management, and Compliance (GRC) framework is more than just policies and tools.
It is a strategic approach that interlaces governance, risk management, and compliance into an overarching fabric, integrating cybersecurity initiatives with overarching business goals and objectives.
Through the promotion of cooperation between departments and a key focus on regulatory compliance, GRC allows organizations to maintain cybersecurity risk while operating with greater confidence.
The process for rolling out an integrated GRC framework is well organized with clear action items creating systematic procedures and definable return on investment metrics.
Identify Key Stakeholders
Smart GRC starts with mapping stakeholders who are key players in establishing and managing the organization’s cyber terrain.
By incorporating GRC Cyber Security principles, organizations ensure that cybersecurity policies, risk assessments, and compliance measures are seamlessly integrated across all stakeholders.
These are executives on down through IT leaders, department heads, and compliance officers.
Regularly engaging these stakeholders in discussions about cybersecurity priorities helps ensure alignment on goals and fosters shared accountability.
For example, executives can provide funding and strategic direction, while IT leaders focus on implementing technical controls like data protection and incident response mechanisms.
In reality, collaboration across departments is key. When all the various stakeholders work together, they help connect the dots between technical and non-technical teams.
This collaborative approach helps make sure governance requirements, such as access controls and incident response protocols, are applied uniformly.
When you make it meaningful by communicating why GRC is valuable and important to everyone in the organization, it creates a deep cultural well.
With GRC, cybersecurity is a collective obligation rather than simply a standalone role.
Nearly 60% of executives rank cybersecurity as one of their organization’s top five risks.
Marsh & McLennan Agency
Establish a GRC Framework
A comprehensive GRC framework provides the groundwork for weaving governance, risk management, and compliance into the fabric of everyday business.
This means having a clear line of documentation around roles, responsibilities, and processes, all while remaining agile to rapidly changing business demands and regulatory pressures.
For instance, defining processes for regulatory compliance in areas like GDPR or HIPAA helps maintain data protection regulations.
Regular reviews and updates to the framework maintain its relevance and effectiveness.
GRC software can support this effort by providing centralized tools that align compliance with organizational objectives, simplifying incident response, risk assessments, and monitoring.
The framework enforces cybersecurity policies consistently across systems, reducing vulnerabilities and ensuring robust governance.
Assess GRC Maturity Level
Evaluating the maturity of existing GRC practices helps identify areas for improvement. Organizations should assess gaps in processes, such as inconsistent risk assessments or outdated compliance measures.
Developing a roadmap for improving GRC maturity offers a structured way to enhance capabilities over time.
Stakeholder involvement in these assessments ensures that improvement initiatives align with business priorities and cybersecurity goals.
Centralized data provided by GRC tools simplifies this process, offering transparency and actionable insights.
The GRC Capability Model
The GRC Capability Model gives organizations an unambiguous baseline standard.
Most importantly, it assists them in measuring their capabilities and developing their skills in the areas of governance, risk management, and compliance. This model was created after countless hours and days of collaboration with thousands of GRC professionals.
It demystifies intricate processes by providing a flexible roadmap.
It provides a framework for organizations to use as a baseline and build upon that foundation to grow their GRC initiatives. Organizations can now take advantage of tools like the OCEG’s Red Book and new 3.5 update.
These resources are a treasure trove of actionable insights that improve decision making and accountability.
Learn and Understand
The real first step—whether you’re a veteran or new to GRC—in applying the GRC Capability Model is understanding the importance of cyber risk management.
At the heart of the “Learn” component is a call for organizations to take stock of their internal and external environments.
This means getting up to speed on stakeholders’ roles, expectations, and the prevailing organizational culture that drives decision-making, which is essential for effective corporate governance.
Accessing other resources such as the Red Book further illustrates important foundational ideas regarding governance, risk, and compliance.
This gives employees the opportunity to develop a strong depth of knowledge on important underlying concepts, particularly those related to compliance management.
Training programs focused on the various roles will improve the GRC understanding among all teams, enhancing their overall GRC capabilities.
For example, Sprinto’s GRC automation capabilities support this discovery stage by simplifying the centralization of compliance materials.
Promoting collaboration and networking between teams increases the visibility of learnings and the flow of best practices, which is vital for maintaining a secure organization.
By keeping yourself up to date with shifting industry developments, you can further help to ensure your risk management strategies stay cutting-edge and effective, ultimately contributing to a successful GRC strategy.
Align Strategy and Actions
Alignment between long-term strategic goals and short-term, day-to-day actions are key to a successful GRC program.
This starts by aligning GRC goals with wider business objectives, making sure that compliance and risk management drive growth rather than holding it back.
For example, organizations can create action plans translating these strategies into specific initiatives, such as adopting automated compliance solutions or implementing ethics-focused training.
Continual review against clear performance-based metrics sharpens these strategies.
Making sure all departments—from IT to legal to operations—are on the same page leads to a successful, unified rollout.
By closing the disconnect between planning and implementation, for-profit and nonprofit organizations alike can cultivate tangible results without compromising ethical principles or industry regulations.
Perform and Execute
Execution transforms strategy into tangible results.
Effective implementation of GRC initiatives requires clear accountability, with teams monitoring progress against defined benchmarks. Real-time feedback allows organizations to adapt execution plans, ensuring they remain aligned with both goals and compliance requirements.
For instance, automating audit processes can improve efficiency while reducing human error.
Regular evaluations of performance ensure that GRC efforts not only meet but exceed expectations.
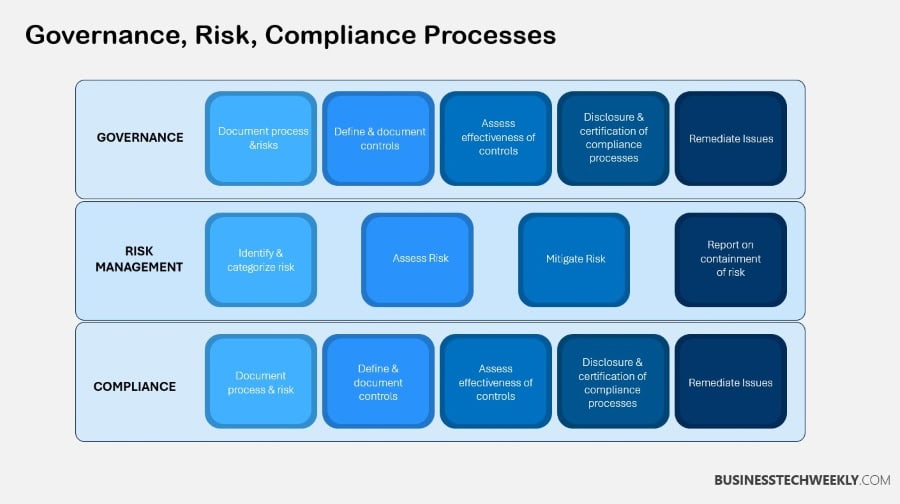
Importance of GRC in Cyber Security
Governance, Risk, and Compliance (GRC) is at the heart of all well thought-out organization’s cyber security strategies.
Implementing a GRC Cyber Security strategy ensures that organizations remain compliant while proactively safeguarding digital assets from emerging cyber threats.
It provides a crystal-clear roadmap for how to combat risks. Simultaneously, it allows for all cybersecurity activities to be in regulatory compliance while furthering organizational objectives.
The growing complexity of cyber threats, coupled with evolving global regulations like GDPR, makes GRC indispensable for achieving resilience and operational efficiency.
1. Key Components of Effective Framework
A robust GRC framework starts with well-defined governance structures, where leadership sets clear policies and accountability measures.
Risk assessments are vital, identifying vulnerabilities and evaluating their potential impact on business operations.
Compliance requirements should seamlessly integrate into the framework, avoiding redundancies and ensuring smooth implementation.
Regular evaluations of each component keep the framework dynamic and responsive, while collaboration across departments strengthens its overall effectiveness.
For instance, aligning IT, legal, and HR teams can foster a unified security approach.
2. Align Cyber Security with GRC
Cybersecurity goals must align with broader organizational objectives to create a cohesive protection strategy.
Integrating cybersecurity into GRC practices unifies efforts across compliance and threat defense.
Collaboration between cybersecurity and compliance teams enables efficient resource allocation, reducing overlaps.
Continuous reviews based on GRC assessments ensure strategies remain relevant and effective.
For example, businesses can use GRC data to prioritize areas requiring immediate attention, such as critical infrastructure protection.
3. Consider Emerging Cyber Threats
The dynamic nature of cyber threats demands proactive risk management.
Regular threat assessments identify new vulnerabilities, while strategies informed by GRC insights anticipate potential attacks.
Sharing updates on emerging threats with stakeholders enhances collective awareness and preparedness. For example, monitoring phishing trends allows organizations to tailor employee training programs, reducing susceptibility.
Only 13% of organizations consistently use key risk indicators (KRIs) to understand and manage IT risk.
4. Influence of Standards and Regulations
Adherence to relevant industry standards and regulations enhances overall business trustworthiness and operational continuity.
GRC frameworks provide the tools that organizations need to fulfill these requirements, like ensuring alignment with GDPR for data protection.
Frequent adjustments to policies help guarantee they stay in line with emerging regulations.
Engaging with regulatory bodies helps organizations to understand where the landscape is heading, encouraging a proactive culture of compliance.
5. Integrate Risk Management
Embedding risk management into GRC ensures a comprehensive approach to handling uncertainties.
Developing strategies covering financial, operational, and reputational risks supports organizational resilience.
Routine assessments refine processes, while encouraging employee participation nurtures a risk-aware culture.
6. Enhance GRC with Automation and AI
Automation simplifies many complacent GRC tasks, allowing teams to focus their energies on activities that add more value.
AI improves threat detection by quickly analyzing enormous datasets to identify patterns or anomalies.
Regularly evaluating these technologies protects against plateauing efficiencies, and remaining open to new innovations places GRC practices at the forefront of rapidly evolving challenges.
Similarly, AI-driven tools enable organizations to rapidly analyze network traffic across all vectors to detect threats in real time.
7. Metrics and Reporting Strategies
Establishing quantifiable metrics produces a basis for understanding GRC’s contribution to maximizing cybersecurity and compliance initiatives in the future. Goal #4 — Practice transparent reporting.
Transparent reporting communicates your performance to all of your stakeholders, which fosters trust and accountability.
Establishing metrics tied to organizational priorities helps maintain focus on them, even when day-to-day pressures distract from long-term goals.
For instance, having a method to track the improvement in incident response times helps highlight the real-world, tangible benefits of GRC.
8. Balance Threat Defense and Compliance
Balancing compliance with active threat defense prevents resource overextension.
Regular evaluations of both areas ensure neither is neglected.
Collaboration between teams ensures shared objectives are met efficiently.
Feedback loops from assessments refine strategies, maintaining equilibrium.
9. Common Implementation Challenges
Organizations go through issues such as technology sprawl and compliance overload while adopting GRC.
Tackling these takes nimble approaches and interdisciplinary dialogue.
Establishing these review cycles will go a long way towards better understanding where implementation is painful and fixing it.
For example, cybersecurity tools sprawl across the organization and under a single GRC, they can be simpler.
10. Improve Stakeholder Collaboration
Collaborative stakeholder engagement in GRC processes cultivates organizational alignment and buy-in, essential for effective governance and risk management.
Having open communication channels, like reviewing progress quarterly, allows for an open dialogue at all times.
Building an open and trusting culture fosters cross-cutting collaboration, bringing together security teams under common objectives to achieve better security results.
Approximately 69% of companies identify regulatory compliance as the primary driver for security spending, highlighting the role of GRC in shaping cybersecurity investments.
Select Common GRC Tools
Navigating governance, risk management, and compliance (GRC) requires equipping your organization with effective GRC capabilities that streamline processes, reduce operational silos, and enhance data management.
Selecting the right tools starts with knowing their purpose and matching them to your risk management strategy.
GRC Software Solutions
Today’s GRC software solutions provide powerful features that enable organizations to better manage risk, enforce enterprise-wide policy, and monitor compliance.
Some key functionalities are audit management, risk scoring, compliance database, and reporting dashboards.
Tools that integrate AI, ML, or predictive analytics offer these sophisticated capabilities, like proactively identifying potential risks and automatically resolving issues before they arise.
Platforms like IBM OpenPages and MetricStream fit like a glove with the technology you already have. Common functionality includes policy mapping, workflow automation, and mobile accessibility.
Evaluating these solutions means looking at your unique needs, whether IT risk management, third-party risk management, or document control.
Account for deployment options and professional service support from vendors to help facilitate a successful implementation.
Unfortunately, too many organizations ignore these key points.
This lack of oversight leads to an overall 80% failure rate for GRC implementations due to inadequate planning or improper tooling.
By proactively reviewing the software’s performance, you can continually refine processes and stay aligned with changing regulatory requirements.
User Access Management
Sensitive information needs to be backed by rigorous user access management protocols.
Adopting measures such as multi-factor authentication (MFA) adds another level of protection, significantly reducing the risk of unauthorized access.
Regularly updating user roles and access levels is an effective way to strengthen your control.
By integrating identity governance tools such as SailPoint or Okta, an organization can govern permissions centrally. This method of presenting information promotes ownership and accountability of all users.
Security Information and Event Management (SIEM)
SIEM solutions form key pillars of today’s cybersecurity architectures, empowering security teams with real-time visibility and threat detection.
Tools like Splunk or ArcSight crunch through massive streams of security data, flagging unusual patterns and anomalies to help predict and prevent incidents before they happen.
Unified collaboration and data sharing between security teams and these tools ensures more effective and sustainable response strategies.
To continue to be effective, periodic reconfiguration of SIEM application is required to defend against new threats that are constantly emerging.
Auditing and Reporting Tools
Auditing tools play a crucial role in effective cyber risk management by measuring progress against internal and external standards.
Strong reporting mechanisms, supported by platforms like AuditBoard and LogicGate, help convey this progress in understandable language, enhancing overall security posture through transparency and accountability among stakeholders, fostering trust within the organisation.
Distributing audit findings to relevant stakeholders not only encourages accountability but also aligns with compliance management practices.
By utilizing customizable dashboards and visualization tools, organisations can ensure that their risk management strategies are effectively communicated, contributing to a successful GRC strategy that addresses compliance issues and strengthens governance.
57% of senior-level executives rank “risk and compliance” as one of the top two risk categories they feel least prepared to address, indicating a significant gap in organizational readiness for GRC challenges.
quantivate.com
Overcome GRC Implementation Challenges
Implementing Governance, Risk, and Compliance (GRC) systems ain’t no stroll in the park either.
From aligning organizational culture to navigating data deluge, the path toward a comprehensive GRC framework demands careful planning.
Organisations that adopt effective GRC capabilities and proactive risk management practices can achieve long-term success in navigating complex regulatory environments.
Manage Organizational Change
Often the greatest challenge in GRC implementation is not even technology-related, but rather organizational change.
Creating formal, planned change management approaches makes for less tumultuous transitions. For instance, implement gradual adoption plans that work with your organization’s current workflows to lessen the pushback.
This was necessary because clear and consistent communication about the importance of GRC at all levels—governments, agencies, etc.—is critical.
Emphasize the importance of GRC to enhancing operational efficiency and improving cybersecurity so that employees are motivated to comply with their requirements.
Involving staff from the start using workshops or collaboration sessions helps to build a level of support and trust.
Measuring the impact of these continuing efforts on a regular basis helps make sure the change process stays on track with GRC objectives.
Improve Data Management Practices
Proper data management is the bedrock of GRC success.
Implementing strong data governance practices, such as centralized data repositories and access controls, can help organizations meet regulatory and risk management obligations.
Performing ongoing policy reviews keeps your organization in sync with constantly changing regulations, preventing regulatory compliance gaps that 80% of organizations find hard to close.
Establishing data stewardship programs fosters a culture of accountability among employees, ultimately leading to improved data quality.
Using analytics tools makes it easier to identify risk and improve decision-making, fostering a more proactive approach to data management.
Develop a Comprehensive GRC Framework
Smart move—an effective, holistic GRC framework brings these three elements of governance, risk and compliance together into a larger strategic framework.
Doing so enables your organization to proactively identify and respond to vulnerabilities while enhancing operational agility.
Frequent public comments and updates to the framework help ensure it remains relevant to states’ ever-changing regulatory landscapes.
Collaboration across departments strengthens processes by ensuring accountability is never overlooked. Effective communication of the framework’s purpose clarifies to everyone involved what is expected of whom, helping to build together strong and effective implementation.
Foster an Ethical Culture
Embedding ethical behavior within your organizational values and priorities strengthens GRC compliance.
Training programs framed around principles of ethical practice in cybersecurity foster greater awareness and prompt personal accountability.
While open discussions on ethical dilemmas promote trust among teams, having clear and transparent policies can help create a culture of integrity.
Ensure Clear Communication
Establishing transparent communication channels across the organization, including compliance and risk teams, is key to GRC success.
Frequent communication and reports on progress allow for ongoing alignment and greater confidence from stakeholders.
Asking for input from the outset encourages democratic engagement and helps make sure initiatives are addressing real-life needs.
62% of organizations have experienced a critical risk event in the past three years, underscoring the prevalence of significant threats and the importance of effective GRC frameworks.
quantivate.com
Implement an Effective GRC Cyber Security Strategy
An effective Governance, Risk, and Compliance (GRC) strategy sets the context for standardized procedures.
These processes continuously and proactively scrutinize governance, risk, and compliance data. It helps you stay compliant with regulatory obligations.
At once, it strengthens compliance, mitigates risks, fosters innovation, and the most important thing – it furthers your larger business objectives.
To make your GRC framework effective, focus on the following key areas:
Define Clear Cybersecurity Goals
Begin by establishing quantifiable cyber security objectives, then map those to your enterprise’s GRC goals. You can set yourself a goal to cut your organization’s data breaches by x percent.
Optimizing response times to incidents can provide a concrete goal. Track accomplishments against these goals, with measurable metrics such as incident response time or compliance audits completed, to keep them purposeful.
Accountability is essential—assign ownership of these short-term goals to groups or people, and sell the importance of these goals to every level of the organization.
Most importantly, transparency makes it clear for everyone who is responsible for what when it comes to realizing these objectives, creating a culture of shared responsibility.
Evaluate Existing Cybersecurity Procedures
Conduct a detailed review of your current cybersecurity practices to identify vulnerabilities. This might involve analyzing recent incidents or conducting penetration tests to uncover gaps.
For example, if outdated software is a recurring issue, prioritize upgrades and patch management.
Collaboration among IT, compliance, and operational teams can lead to streamlined processes and improved procedures.
Regular evaluations ensure your cybersecurity measures adapt to emerging threats and changing compliance requirements.
Secure Leadership Buy-In
GRC must have leadership support to be successful. Show tangible evidence of how GRC initiatives have reduced risks, improved compliance, and avoided expensive fines.
Statistics show that executives agree—87% put reputational risk at the top of their minds. This further underscores the importance of sustained and visible leadership engagement.
Keep executives informed—Consistently brief executives on progress and challenges as well as emerging risks to foster a collaborative and effective relationship between leadership and cybersecurity teams.
Leverage GRC Solutions
Determine which GRC technologies would best benefit your organization’s requirements, such as automated compliance implication uploads or risk management dashboard implementations.
To measure their effectiveness, track metrics like the number of reduced audit findings or increased accuracy of risk reporting, for example.
Maintaining your visibility into new GRC innovations helps keep your framework updated, continuing to save you time and improve collaboration among departments and teams.
Test and Refine the GRC Framework
Continuous improvement strengthens your GRC framework. Regular testing, like simulated compliance audits or risk assessments, can reveal areas for improvement.
Gather feedback from all stakeholders, from department heads to frontline employees, ensuring refinements are practical and effective.
By embedding a culture of improvement, your organization can adapt to evolving challenges without compromising compliance or governance.
Define Cybersecurity Roles and Responsibilities
Define and communicate clear accountability across every layer of cybersecurity from threat monitoring to incident management.
For example, having a full-time compliance officer makes sure that regulations are being followed even as IT staff focus on their technical defenses.
These roles should be reviewed regularly to ensure they are aligned with shifting business priorities.
Good communication reinforces a culture where every employee knows their role in protecting organizational assets, reinforcing accountability at all levels.
Key Points to Consider
- GRC, short for governance, risk management, and compliance, is an all-in-one methodology that is key to successful cyber security management. It fosters accountability, improves risk management overall, and keeps the organization in line with regulatory and internal requirements.
- Governance entails defining and implementing unambiguous roles, responsibilities, and policies that govern cybersecurity practices. It is implementing access controls and standard operating procedures to safeguard sensitive data.
- Risk management focuses on identifying, assessing, and mitigating cyber threats. It requires continuous monitoring and adaptation to address the ever-changing threat landscape.
- Compliance ensures organizations meet external regulations such as GDPR or HIPAA and their internal protocols. As compliance standards rapidly evolve and change, regular reviews are crucial to ensure compliance strategies remain in lockstep.
- Adopting a GRC framework further integrates cyber security efforts with overarching business objectives, promotes employee awareness, and builds organizational resilience against potential cyber threats.
- Take advantage of tools including GRC technology, data analytics and automation. They can help you automate work, maximize operational efficiencies, and improve your security environment across the board.

