PCI DSS compliance: The 6 main goals

As a small or medium business, you would have likely of PCI-DSS. However, do you understand what PCI-DSS is, why is it important, or whether you need it? To help you along, we’ve answered these questions for you and help you understand the six goals of PCI DSS compliance.
Understanding what PCI DSS is
PCI-DSS is a global standard and is an industry requirement for all merchants that handle payment cards for any transaction (online, offline, telephone, for example). The standards stipulate the minimum security measures which merchants need to implement to reduce the risks of a data breach.
Created by the PCI Security Standards Council, PCI DSS is short for Payment Card Industry Data Security Standard.
The PCI-DSS specifies the basic security features that organisations must have in place to minmize the likelihood of a cardholder’s data from being compromised. Merchants which adhere to the PCI DSS standard significantly reduce the chances of experiencing a data breach.
Any merchant which stores, processes or transmits cardholder data has to be PCI DSS compliant.
The six PCI DSS compliance goals
The requirements for PCI DSS compliance are summarised in six goals:

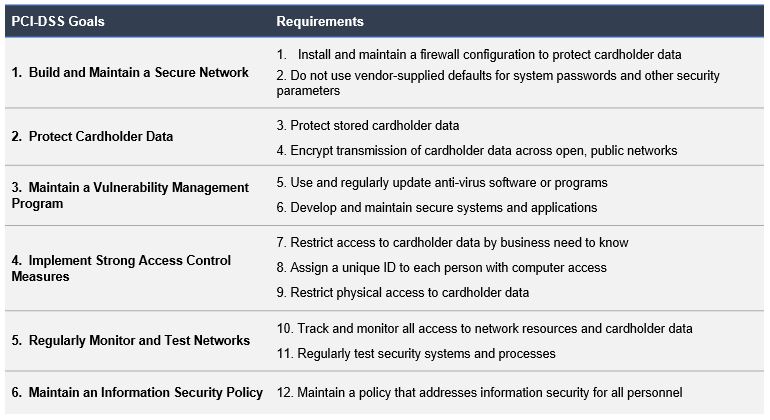
PCI DSS: Goals, Objectives and requirements
The PCI Data Security Standard (PCI DSS) seeks to ensure the protection of cardholder data as well as sensitive authentication data, regardless of where it is stored, processed or transmitted. The 6 PCI DSS compliance goals stipulate security requirements and processes to crucially protect all payment card account data.
Here, the PCI DSS compliance objectives and requirements are presented in more detail.
PCI DSS Goal 1: Build and maintain a secure network
Before the internet, e-commerce, and internet banking, criminals had to gain physical access to steal financial records. However, nowadays, in the digital age, PIN entry devices and computer networks are used to conduct many payment card transactions.
Consequently, the first of the PCI DSS compliance goals covers the need for a secure network. By employing robust network security protocols and controls, businesses can prevent and deter any criminal activity, particularly the theft of cardholder data and/or sensitive authentication, through any illegitimate virtual access of payment system networks.
The requirements for PCI DSS goal 1 are:
1. Install and maintain a firewall configuration to protect cardholder data:
A firewall inspects network traffic by assessing it against pre-configured rule sets. Through this process, firewalls can allow or deny traffic, thereby protecting internal networks. To ensure the firewalls perform optimally, businesses must, every six months, assess and where necessary, update firewall configuration rules.
To meet the PCI standards, firewall rules have to be configured to restrict traffic to services and ports which are documented and necessary for business operations. Essentially, any port and service left open must be able to be justified as required for business needs.
2. Do not use vendor supplied defaults for system passwords and other security parameters:
Malicious actors and cyber criminals can quickly obtain manufacturer-supplied default passwords. Failure by businesses to change and, if necessary, disable standard passwords and accounts, can result in internal networks being exploited and cardholder data being compromised thorugh these credentials.
Similarly, wireless networks are required to have all manufacturer settings changed, including passphrases, passwords, etc. Any unsecured, undocumented and unnecessary services need to be deleted to make sure that they can’t be used to gain access to internal networks.
PCI DSS Goal 2: Protect Cardholder Data
Cardholder data means any information on a payment card which is printed, processed, transmitted or stored in any form. To prevent its unauthorised use, Businesses accepting payment cards must protect cardholder data – regardless of whether the cardholder data is stored locally, or transmitted over an internal or public network to a remote server or service provider.
The requirements for PCI DSS goal 2 are:
3. Protect stored cardholder data:
Under all circumstances, businesses should strive to eliminate storage of cardholder data, unless where necessary for for business, legal, or regulatory needs. After authorisation, Sensitive Authentication Data (SAD), including data on the magnetic stripe and CVV, EMV chip, PIN/PIN Block, must never be stored.
When it is necessary to store cardholder data, information such as the Primary Account Number (PAN), cardholder name, and expiration date, must be rendered unreadable.
4. Encrypt transmission of cardholder data over open public networks:
To avoid compromise, encryption, using strong cryptography, must be used when using public networks for transmitting cardholder data. The selected encryption must feature a secure version and the appropriate level of encryption strength. Messaging applications such as, Chat, email and IM, must never be used to transmit PANs.
PCI DSS Goal 3: Maintain a vulnerability management program
Vulnerability management refers to the systematic and continuous process of identifying weaknesses in a business’ payment card system infrastructure. The payment card system infrastructure includes security procedures, system design, implementation, or internal controls which may be exploited to breach system security policy.
The requirements for PCI DSS goal 3 are:
5. Protect all systems against malware and regularly update anti-virus software or programs:
Businesses are required to install, maintain and regularly update Anti-virus software. Also, anti-virus software has to be scheduled to conduct periodic scans and generate appropropriate audit records. The ability to deactivate the Anti-virus must be limited to management authorised administrators only. In the event Anti-virus does need to be disabled, the period for which the antivirus is deactievated must for a limited time only.
6. Develop and maintain secure systems and applications:
Any newly identified vulnerabilities need to be classified in accordance to the risk posed to the cardholder data environment. Such weaknesses include buffer overflows, cross-site request forgery and cross-site scripting. Web applications which are public-facing, are required to be tested through application penetration testing, and application security tools or methods. In addition, Web Application Firewall is required to be used.
PCI DSS Goal 4: Implement strong access control measures
Physical access controls refer to the employment of locks or other means to physically manage, monitor and restrict access to storage media, paper records or system hardware. In comparison, logical access controls limit the use, to authorised users, of payment devices, computing devices, wireless networks, and also controls the access to any digital files which contain cardholder data.
Access-controls allow the effective management and control of sensitive data, by permitting or denying access PAN and other cardholder data. Any access is required to be granted on a business need-to-know basis.
The requirements for PCI DSS goal 4 are:
7. Restrict access to cardholder data by business need to know:
Role-based access operates on the notion of “need to know” – an individual can only access the minmimum data necessary to perform their role. All access to to the system should also be covered by the principle of “need to know”. This is achieved by setting the default access to “deny all” users which are not expressly granted authorisation.
8. Identify and authenticate access to system components:
Users confirming access using a unique ID, will ensure accountability for all actions taken on system components. Robust passwords have to be used containing at least seven alphanumeric characters.
Multi-Factor Authentication (MFA) is mandatory. MFA uses a secondary authentication method in conjunction with an alphanumeric password. The secondary authentication is attested by sending a code to a device, biometric scan, or key fob or smart card.
9. Restrict physical access to cardholder data:
Within the cardholder data environment, physical access to secure areas must be controlled and monitored by video and/or access control. Unless prohibited by law, all-access data is required to be retained for 90 days.
Cardholder data contained on any media has to be destroyed when the requirement is no longer valid. For instance, paper forms with cardholder data must be shredded once the retention period has expired. All point of interaction devices must be listed and maintained and protected from tampering or unauthorised replacement.
PCI DSS Goal 5: Regularly monitor and test networks
The payment infrastructure comprises of physical and wireless networks which interconnect all endpoints and servers. Any weaknesses present in the payment infrastructure provide opportunities for cybercriminals to gain illegitimate access to payment cardholder data.
To prevent the unauthorised use of cardholder data, businesses must regularly monitor and test networks, which form the components of the payment infrastructure, to find and fix vulnerabilities.
The requirements for PCI DSS goal 5 are:
10. Track and monitor all access to network resources and cardholder data:
Through the implementation of sytem logging, businesses will be able to relate actions to specific accounts and therefore, individuals. System logs are required to be kept for a minimum of 1 year, of which, three months worth of logs have to be readily available.
To avoid log information from being altered or deleted, logs are required to be backed up to a centralised server. By reviewing the logs daily, business can, and should, address any anomalies immediately.
11. Regularly test security systems and processes:
To defend the payment cardholder environment from any newly discovered network vulnerabilities, businesses must perform penetration testing and internal and external vulnerability scans. To identify any potential unauthorised access points, whether using manual or automated methods, businesses are required to ensure the payment cardholder environment is scanned.
Any unexpected changes occurring in the environment can be determined through file integrity monitoring and intrusion detection systems, which will provide an alert in case of any changes.
PCI DSS Goal 6: Maintain an Information Security Policy
The sixth of the PCI DSS compliance goals covers information security policies. All employees should be aware of the sensitive and confidential nature of cardholder data and their responsibilities for protecting it. A robust security policy sets the tone for security affecting an entire business, and it informs employees of their expected roles and duties related to the protection of cardholder data.

