What is Cyber Security Analytics? Tools, Techniques, and Benefits

On this page:
- What is Cyber Security Analytics
- Techniques in Cyber Security Analytics
- Tools for Cyber Security Analytics
- Common Cyber Security Threats
- Proactive Security Strategies
- Benefits of Cyber Security Analytics
- Future Trends in Cyber Security Analytics
- Role of Data Analytics in Cybersecurity
- Use Cases for Security Analytics
- Key Points to Remember
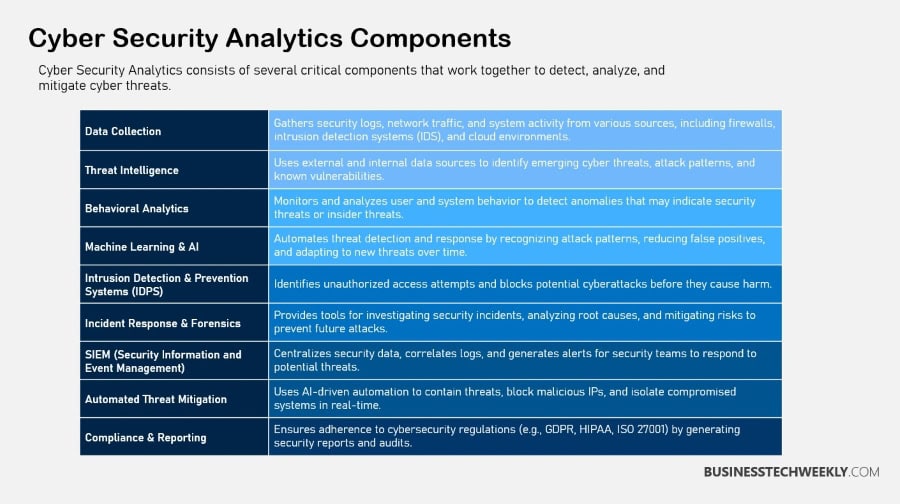
What is Cyber Security Analytics
Cyber Security analytics is an emerging, more proactive, and risk-focused approach to cybersecurity.
Instead of sticking to tried-and-true yardsticks, it uses more advanced tools and methods to combat ever-changing threats.
Security Information and Event Management (SIEM) systems enable organizations to form a powerful first line of defense with real-time monitoring. This lets them pinpoint threats in real time as events unfold.
Additionally, the use of machine learning increases the ability to proactively predict and prevent future security threats.
This method proactively examines behavioral trends. It uses user and organizational behavior data to detect anomalies that can signal security threats.
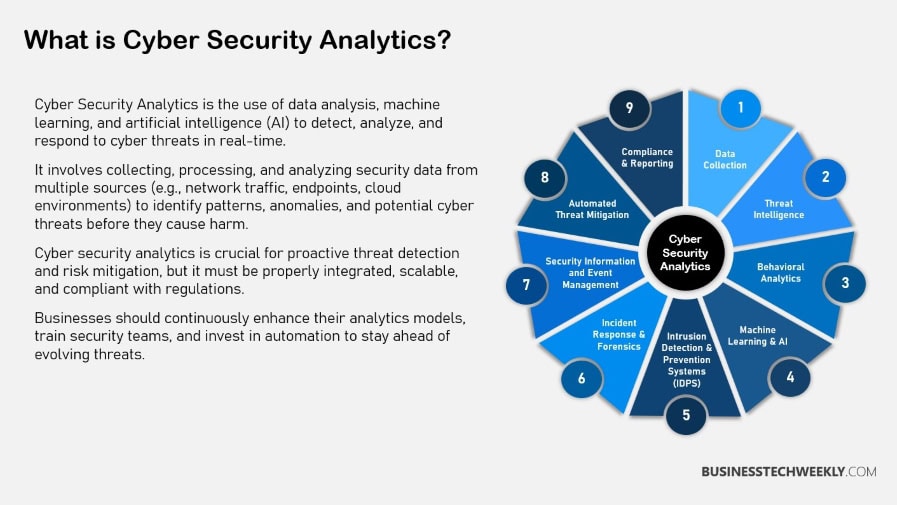
Definition and Key Concepts
At its most fundamental level, cyber security analytics means a lot of buzzwords including threat detection and incident response.
Clarity on these terms will go a long way in helping you understand how cyber security analytics can play a role in improving your organization’s security posture.
Smart solutions include all facets from data collection at the endpoint, network routers, and virus scanners.
Continuous improvement is key. Cyber threats are becoming more complex, so it’s important to continuously adapt and improve your cybersecurity practices.
Importance in Digital Protection
Together, cyber security analytics goes a long way toward improving an organization’s ability to detect and respond to threats.
Predictive analytics is the key to stopping incidents before they have a chance to occur.
It’s a proactive approach that leverages data-driven insights to improve security posture. Blend these analytics into your overall approach.
It’s important for your organization to remain vigilant, because 99% of breaches start with a phishing email.
You can leverage frameworks such as the cyber kill chain and the MITRE ATT&CK Framework to improve your security posture.
This makes proactive measures, like threat hunting, exponentially more possible.
Techniques in Cyber Security Analytics
1. Unsupervised Anomaly Detection
Unsupervised anomaly detection is particularly important in cyber security analytics, as it is used to identify unknown threats without requiring pre-labeled data.
This approach uses advanced algorithms to identify trends and anomalies in data. Consequently, it can identify threats that other approaches cannot, including zero-day exploits.
For instance, it might be able to identify abnormal network behavior that shows a company has been hacked.
The real-time threat identification capability gives you an advantage in rapidly changing cyber environments. Applying unsupervised methods is difficult.
The massive scale of data leads to the need for powerful algorithms to accurately reduce false positives.
2. Supervised Detection Approaches
Supervised detection is dependent upon having quality labeled datasets to train models on various types of threats to classify them correctly.
This technique greatly improves the accuracy of threat detection, which you may have already experienced in applications such as heuristic analysis for zero-day exploits.
Regularly updating training data is key to staying one step ahead of constantly changing threats.
Cyber security data analysts are critical in helping to fine-tune these models. Their human-powered models are constantly trained against new, advanced cyber threats like those mapped out in the ATT&CK framework.
3. Predictive Analysis Methods
Predictive analysis techniques predict future hazards by studying past data and recognizing trends.
These techniques enable organizations to take a more targeted approach to security, focusing resources on the areas that will yield the greatest impact.
Historical data is essential to improving these predictive capabilities, as it gives context to the data helping to identify upcoming threats.
Pairing predictive analysis with advanced technologies such as machine learning enhances these outcomes, providing a more proactive approach to cybersecurity.
For example, using historical breaches such as the Target data breach to develop better tactics to prevent future threats.
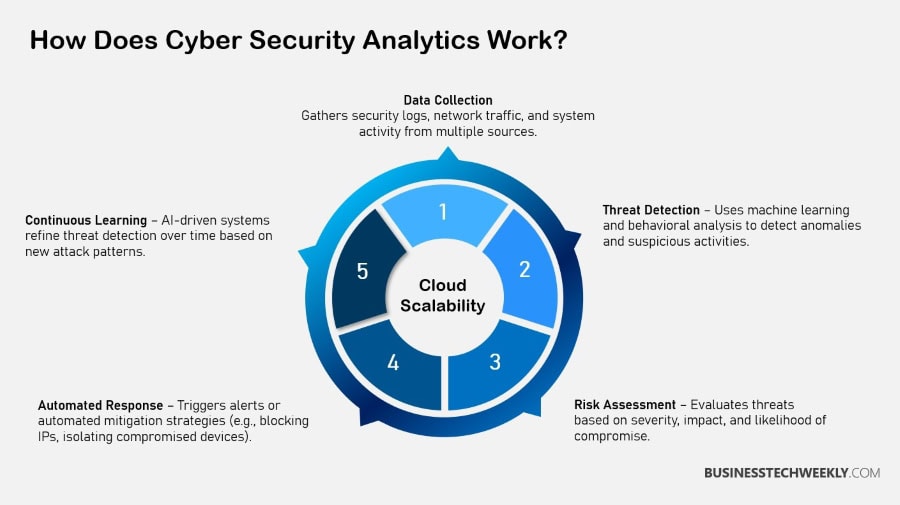
Tools for Cyber Security Analytics
In today’s cybersecurity landscape, using the best tools available to them is imperative to protecting their data and infrastructure.
Cybersecurity analytics tools leverage the full might of data science techniques and AI algorithms. They analyze petabytes of data, finding patterns and predictions that manual methods can’t find.
These tools continuously collect information from multiple sources, including the ways users interact with content and reports from virus scanners.
They offer an advanced, proactive approach to security.
Security Analytics Software
When it comes to popular software on the market, one of the most popular choices is solutions like Splunk.
These tools break down the barriers between data and action, enabling security teams to act quickly and confidently to keep their organizations secure.
Each tool’s strengths and weaknesses vary, ranging from real-time monitoring capabilities to ease of use in the user interface.
Real-time monitoring and incident detection are key features, allowing for immediate action to be taken in response to threats.
An intuitive interface is of the essence.
This ensures that even software novices can quickly and easily find their way around the software, greatly increasing accessibility and improving efficiency.
Unified Security Platforms
Unified security platforms bring together security analytics on a single system to create a centralized system for collecting, storing and managing security data.
This centralization creates stronger team collaboration, making it easier for teams to communicate and share insights.
The true power of these platforms is their scalability – the ability for an organization to grow with their security needs as they expand.
Unified platforms pull together disparate analytics tools to give you a more complete picture.
This change takes cybersecurity strategies from reactive to proactive, something that is critical in today’s ever-evolving threat landscape.
Common Cyber Security Threats
Whether cyberattack, breach, or physical theft, knowing what the most common security threats are will help protect your organization’s continuity and your data.
Cybercriminals target these vulnerabilities by using techniques such as phishing, which is when users are deceived into providing sensitive information.
The consequences are often catastrophic, crippling business operations and integrity of data.
Phishing is one of the top threats to any security posture.
Social Engineering Tactics
Social engineering tricks people into granting access they shouldn’t have.
Cybercriminals use tactics like spear phishing, blasting out messages pre-written to look trustworthy and official.
Awareness and training are key to preventing these threats.
Organizations see a huge advantage in establishing security policies that expressly cover all social engineering tactics.
RELATED: Common Social Engineering Red Flags your staff must learn to recognize
Insider Threats and Risks
Insider threats come from threats that are already inside your organization that can cause serious, unique security threats.
Given their internal nature, detecting these threats is difficult.
Having a way to monitor user behavior is essential to spotting risks before they can be exploited.
Creating a culture of security awareness with employees makes your entire organization more secure.
Advanced Malware and APTs
Advanced persistent threats (APTs) are notorious for their stealth and persistence.
As malware has evolved, it has become much more sophisticated, requiring proactive detection methods.
Organizations that invest in sophisticated threat detection capabilities are more prepared to combat these threats.
RELATED: Unveiling the Advanced Persistent Threat Landscape
Denial of Service Challenges
Denial of Service (DoS) attacks deny service availability, often with multiple attack vectors resulting in varying levels of impact.
Strong, proactive defenses are key to preventing these attacks.
By creating incident response plans, organizations can be better equipped to handle DoS situations when they arise.
Vulnerabilities in Systems
Common vulnerabilities, such as SQL injection, compromise web applications.
Regular vulnerability assessments and scans are indispensable.
Effective patch management plays a vital role in addressing these vulnerabilities.
A proactive approach to vulnerability management strengthens organizational security.
RELATED: Web Application Penetration Testing: What You Need to Know
IoT Security Concerns
IoT devices create a distinct set of security threats that further increase the risk inside organizational networks.
With continued proliferation of these devices comes blessings of unintended consequences which leave them vulnerable to unauthorized access.
Customized security measures specific to IoT environments are critical to stopping a security breach before it occurs.
Proactive Security Strategies
Proactive security strategies are all about getting ahead of the threats.
By shifting from a reactive strategy to a more proactive approach, organizations can effectively utilize security analytics solutions to prevent cyber incidents rather than just responding after they occur.
This proactive strategy is crucial — it focuses on prevention and includes essential elements like 24/7 monitoring and threat intelligence, which are vital for detecting threats before they escalate into serious risks.
The proactive security market is projected to achieve a CAGR of 14.23%, reaching USD 20.81 million in 2020 and USD 45.67 million in 2026.
Investing in good cybersecurity analytics today will yield significant benefits in the future.
These proactive strategies encompass system updates, threat hunting, and leveraging sophisticated cybersecurity analytics platforms.
Such tools enhance detection and prevention capabilities, enabling organizations to confidently address emerging threats and drastically reduce breach response times from 100 days to less than 12 hours.
Utilizing Cyber Kill Chains
The cyber kill chain is a popular model that reflects the various stages of a cyberattack. It gives you a better understanding of many attack vectors.
Organizations can implement this model to strengthen their defenses by aligning security controls to each stage in the pipeline, resulting in layered protection.
Map previous events onto this framework. You’ll learn what makes your environment vulnerable so you can develop better defenses and improve your response capabilities to minimize impact.
Implementing MITRE ATT&CK Framework
The MITRE ATT&CK framework is an extensive matrix outlining adversary tactics and techniques and is frequently used in threat modeling.
Organizations can use this framework to improve threat detection by focusing their security efforts on the framework’s recommendations.
Training security teams on this framework ensures effective use, optimizing your cybersecurity posture and enabling quick identification and response to threats.
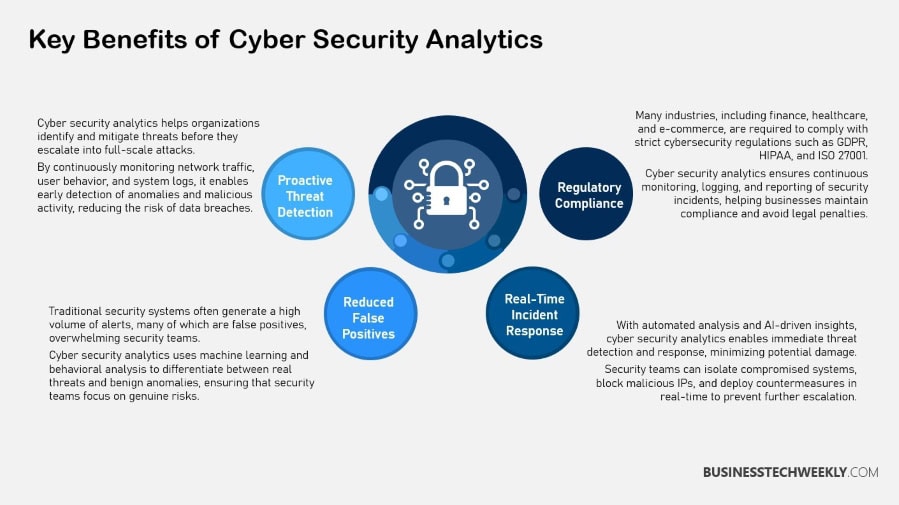
Benefits of Cyber Security Analytics
Cyber Security analytics provides powerful benefits to organizations that are seeking to strengthen their cyber defense.
Organizations use analytics to rapidly filter through terabytes of data. This iterative process reveals deep insights that inform and guide strategic decision-making.
This capability makes possible proactive threat detection, including unusual activities like log-ins at strange times of the day or access to sensitive databases.
Cyber security analytics provides a holistic view of security. It far exceeds conventional, siloed solutions that often focus on only a corner of IT security.
Enhancing Security Measures
Cyber security analytics makes our overall security much stronger by shedding light on cracks in our current protocols.
By leveraging data-driven insights, organizations can prioritize and make informed decisions to strengthen their defenses.
By identifying gaps in existing protections, analytics leads to a process of ongoing review and enhancement.
Using this technology, organizations can move more efficiently, effectively securing all entry points. They use Autonomous Endpoint Management so they can focus on health and safety.
Improving Decision-Making Processes
Analytics allows for data-driven, strategic decision-making by providing actionable intelligence.
Security teams are provided with all of this valuable information, allowing them to build analytics into their strategy planning to best prioritize investments.
By concentrating analytic efforts on reducing false positives, organizations can increase their detection and response capabilities.
This makes prevention efforts more effective by over 90%.
Future Trends in Cyber Security Analytics
Here’s a look at some of the key trends that are increasingly shaping the modern cybersecurity analytics landscape.
Another important trend is the adoption of generative AI to cybersecurity analytics. This technology provides proactive zero-day vulnerability detection through code analysis and behavioral analysis.
It uses machine-learning to predict future vulnerabilities based on past data. AI enhances the ability to detect threats and provides the ability to predict risks in the future.
This allows organizations to establish a proactive defense mechanism.
Emerging Technologies and Innovations
Emerging technologies are playing a key role in the development of cybersecurity analytics.
Innovations such as machine learning and AI enhance threat detection and response capabilities significantly. These technologies allow systems to proactively predict threats and mitigate them before they occur.
For instance, AI will enable threat actors to create more advanced phishing attacks, past just the basic “reset your password” phishing campaigns.
Keeping on top of these technological breakthroughs is imperative. Organizations are encouraged to explore and integrate such technologies to bolster their cybersecurity framework, ensuring they remain resilient against evolving threats.
Evolving Threat Landscape Adaptations
To keep pace with a rapidly evolving threat landscape, organizations need to be more agile than ever.
The capacity to predict and react to emerging threats relies on superior analytics.
When it comes to cybersecurity, data science provides a powerful advantage, equipping organizations to better defend their most critical digital assets.
Just like our threat landscape, the smartest strategies are always changing with the times.
Continual monitoring and testing of security postures is key, giving organizations the ability to match their defenses with new, sophisticated threats. The ransomware trend, for example, is not likely to abate any time soon, needing ongoing awareness and evolution.
As a result, 93% of organizations are preparing to outsource more of cyber risk mitigation. In fact, they have plans to integrate with security service providers in the next two years.
Role of Data Analytics in Cybersecurity
Data analytics is the key to establishing a more proactive cybersecurity posture, particularly through effective cybersecurity analytics solutions.
It offers robust technologies that analyze massive datasets to spot patterns, anomalies, and trends, enabling the detection of potential threats.
Learn how to leverage the power of a good cybersecurity analytics platform to sharpen your threat detection capabilities.
Respond to incidents more effectively! For instance, these security analytics tools identify suspicious login hours and prevent invalid database queries.
This proactive approach plays a key role in helping security teams stay one step ahead of malicious insiders.
Correlating data from multiple sources can help reveal hidden patterns.
For example, user behavior analytics (UBA) and virus scanning software can provide the first indicators of an attack. That proactive approach is very important, but it’s not enough by itself.
The demand for cybersecurity analytics will increase by 15% from 2022 to 2032.
By investing in data analytics training, organizations can equip their security teams with the necessary skills for real-time threat visibility, allowing for swift and effective responses to potential attacks.
RELATED: Cyber Attack Vectors: Understanding Attack Vector Types & How to Defend against them
Use Cases for Security Analytics
Security analytics is fundamental to protecting our ever-expanding digital environments, which requires turning massive amounts of data into meaningful insights.
Financial institutions have excelled in implementing security analytics solutions.
They monitor endpoint data, user behavior, routers, virus scanners, and more to enhance their security posture.
These four use cases showcase how custom solutions can meet specific security needs in innovative ways.
Organizations need to integrate contextual data to build a more complete data set. This integration allows security professionals to identify early signs of an attack, making it a crucial part of their cybersecurity strategy.
With millions of event and log data generated daily, flagging the Indicators of Compromise (IoC) can be challenging.
To improve their chances of detecting new threats, organizations are increasingly adopting cybersecurity data analytics tools like user and entity behavior analytics (UEBA).
To bolster their defenses further, they deploy automated network traffic analysis.
The market for security analytics is estimated to be $10.6 billion in 2021 and is expected to grow to $25.4 billion by 2026, highlighting the increasing significance of effective cybersecurity analytics solutions.
Sharing success stories fosters an environment of best practices and cross-sector collaboration.
Key Points to Remember
Cyber security analytics is leading the way in securing our tomorrow’s digital landscapes. It relies on innovative tools and techniques to fight constantly changing threats.
With its emphasis on real-time analysis and rapid response, it’s become a cornerstone of today’s security approaches.
- Cyber security analytics is a proactive approach that utilizes tools like SIEM for real-time monitoring, machine learning, and behavioral analysis to predict and prevent security incidents, enhancing an organization’s overall security posture.
- To truly succeed in cybersecurity analytics, you need a firm understanding of concepts such as threat detection and incident response. This field requires constant evolution to stay ahead of emerging threats and maintain a robust security infrastructure.
- Predictive analytics and data-driven insights play a vital role in preventing cyber incidents, allowing organizations to prioritize security efforts and integrate analytics into their overall strategy for enhanced protection.
- Unsupervised anomaly detection and supervised detection techniques are key to revealing the unknown threats. With ongoing version updates and the input of talented cybersecurity data analysts, we’re learning how to do a better job at making threat detection more precise.
- Investing in fundamental cyber security analytics tools increases the effectiveness of analyzing security data. Industry-leading security analytics software and unified security platforms bring teams together and help them work together more efficiently at scale.
- Being aware of common security threats like social engineering, insider threats, and advanced malware is critical. Organizations should implement proactive security strategies, maintain regular security assessments, and adapt to emerging trends to mitigate risks effectively.

