VPN Security Best Practices: Choosing & Maintaining Your Service

On this page:
Why Choose a VPN?
Protect Online Privacy
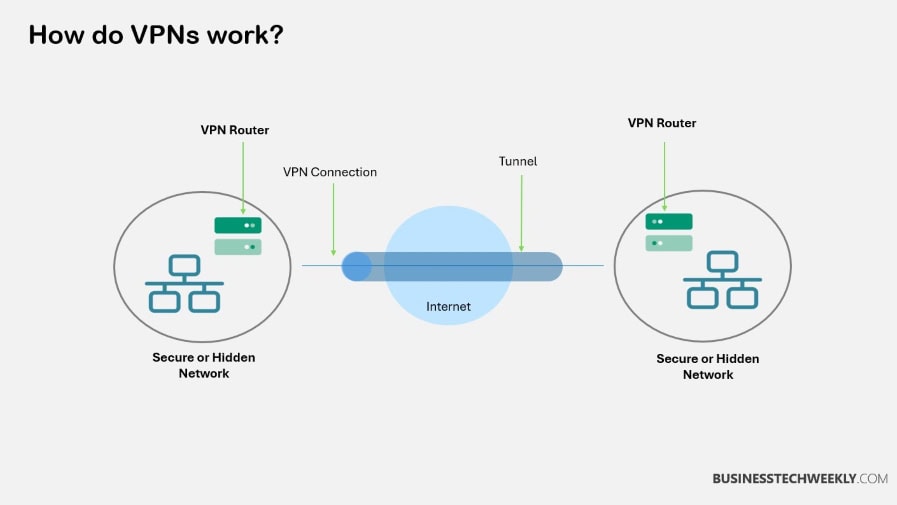
By using a VPN, all of your internet traffic is encrypted and your real IP address is hidden.
This military grade encryption keeps everything you do online, including your browsing history, private. Consider what type of data you’re working with and make your security requirements accordingly.
Beyond the convenience, if you’re dealing with sensitive information, a VPN is non-negotiable.
Know how you use the internet to determine when VPNs are most important. VPNs perform optimally for high-stakes activities such as banking, where privacy is essential.
Make sure your VPN works across all your devices, from laptops to mobile. This ensures continuous protection across all devices.
Secure Data Transmission
VPNs are essential to keeping data transfers on unsecured networks safe. As a result, they stand guard against unwanted access as well as MitM attacks.
Weigh built-in VPN clients against external ones to find out what works best for your circumstances. The distinction between mandatory and optional protocols is an important one to know when following required security standards.
VPNs such as NordVPN and Surfshark One provide powerful phishing protection, preventing phishing attacks from intercepting your data.
Access Restricted Content
Getting around restricted content becomes a piece of cake when you’re connected to a VPN. Full-device or app-specific configurations for tailored protection.
Split tunneling options allow you to balance performance and security. Effective control of VPN tunnels is the key to performance.
For instance, you can view shows not offered in your country without sacrificing security.
Assessing the Need for a VPN
Recognize and Handle Captive Portals
On public networks, your VPN should be able to instantly detect captive portals.
These are walled-garden web pages that load before you have access to the whole internet.
By making access more convenient for users, you’ll help your team get connected quickly and without frustrating wait times.
With captive portal handling especially, you want to ensure that you’re always delivering seamless connectivity without compromising security.
That could mean setting your VPN up to manage traffic through these interruptions smoothly, so security protocols are never put in jeopardy.
Determine Your Security Requirements
Frequent deployments for both client and back end are necessary. Each patch defends against CVEs that a bad actor could use to gain access to your site.
When you encrypt tethering with a VPN, you ensure security on every connected device.
This becomes essential for teams operating under a hybrid model and requiring secure remote access to company resources.
Evaluate Internet Usage Patterns
Using strong encryption and authentication methods, when configuring your VPN will further improve security.
Frequent software updates are needed to patch vulnerabilities, so your VPN can be a strong line of defense.
By continuously checking for and managing vulnerabilities, you can protect your network and the sensitive data in it from costly breaches.
Limiting VPN traffic to only authorized users greatly limits the risk.
Consider Device Compatibility
Educating users about safe data handling practices further reinforces their knowledge of VPN security.
Quick response to security incidents will ensure you limit the damage as much as possible.
This will also help you hone your tactics in the long run.
Understanding VPN Protocols
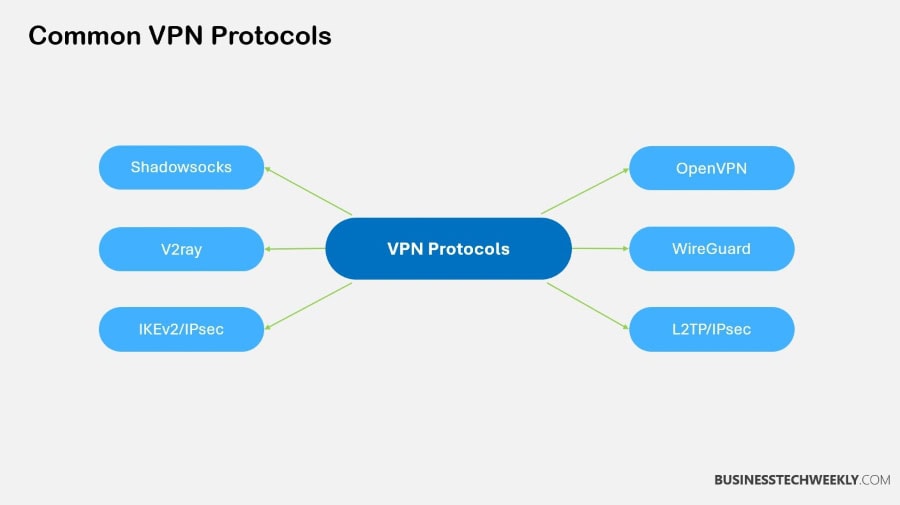
So, when you’re getting into VPN security best practices, knowing the difference between VPN protocols is a must.
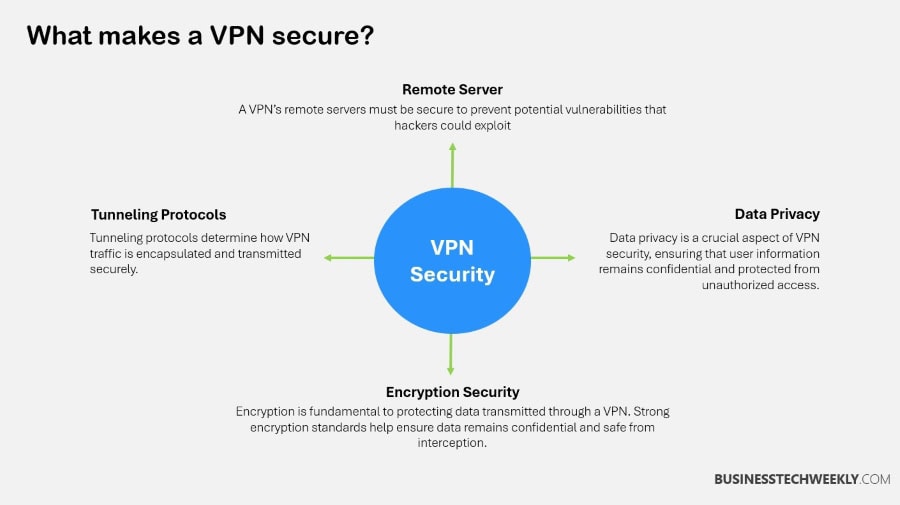
A VPN protocol is a set of detailed guidelines that dictate how your internet traffic moves. It travels from your device, through the VPN server, and then out onto the internet.
However, as technology has advanced, many different protocols have been created, all offering different strengths.
For example, OpenVPN uses both UDP and TCP, providing a flexible approach to data transmission.
WireGuard is a young technology that is still figuring itself out. It provides ease of audit and has a smaller attack surface due to its minimalistic code.
On the other hand, IKEv2 is preferred for connecting on the go, keeping connections active while switching between networks.
Encryption Methods
Encryption methods are a key part of protecting VPN connections. WireGuard uses ChaCha20, a newer cryptographic approach, while OpenVPN generally defaults to AES encryption.
While ChaCha20 is simpler, it’s still extremely secure, representing the effective innovations in practice today within VPN technology.
Finding the right encryption balance between your security requirements, compatibility, and performance is key.
Built-in vs External VPN Clients
Choosing between built-in and external VPN clients has an impact on performance and security.
Built-in clients provide convenience and out-of-the-box integration with your current systems, while external clients may offer more advanced features and flexibility.
Evaluating your business requirements and long-term IT strategy will help determine the right decision, striking the perfect balance between security and usability.
Mandatory vs Optional Protocols
Protocols such as PPTP are now considered mostly defunct, with just 1% of users using PPTP because of its weaker encryption.
Focusing on mandatory protocols with a focus on security, like OpenVPN, is really the only way to keep your data safe.
While such optional protocols may provide added benefits, the primary goal should be to improve secure communication first and foremost.
Configuring a VPN Connection
1. Choose Between Full-device and App-specific VPN
When configuring a VPN connection, it’s important to choose a full-device VPN versus an app-specific VPN.
Full-device VPNs, which encrypt all internet traffic on your device, are the best choice if you want all-around protection.
For example, this option is best suited for remote working scenarios where overall network security is most important.
Conversely, app-specific VPNs only encrypt data from specific apps. This is perhaps the most cost-effective choice for businesses who need to protect their sensitive applications such as online banking or proprietary communication applications.
Ultimately, your choice depends on your unique requirements, weighing increased security against resource expenditure.
2. Decide on Split Tunneling Options
Split tunneling is the next key factor. This feature allows you to send only part of your internet traffic through the VPN.
You can transmit the remainder via your normal internet connection.
This configuration can save a lot of bandwidth, making access to the local network much faster while important data remains encrypted.
A company can secure their online transactions with VPN split tunneling.
This strategy allows your employees to visit non-sensitive websites without the added overhead of encryption.
It’s just a smart, pragmatic way to deliver more efficiency without sacrificing security.
3. Manage VPN Tunnels Efficiently
That’s why proper VPN tunnel management is critical to ensure a secure and stable connection.
This includes keeping an eye on active tunnels for any suspicious behavior, as well as making sure they’re tweaked for top performance.
Keeping VPN software up to date and re-evaluating protocols on a regular basis can help keep potential threats at bay.
Taking this proactive approach will go a long way in protecting your business from cyber threats.
Captive Portal Detection
Recognize Captive Portals Automatically
Automatically detecting captive portals helps keep your network safe and secure. When configured properly, a Wi-Fi captive portal removes the majority of frequent onboarding pain points.
When you set your GlobalProtect app to alert users that a captive portal has been detected, you improve user experience by connecting the dots.
If the network returns anything else, not just an HTTP 302, it is a captive portal.
This knowledge is what enables users to connect to the internet safely and securely.
For network security, enforcing GlobalProtect for Network Access is important.
This reduces risk by limiting access to authenticated users, which is the case majority of the time.
Collectively, these steps make for a solid strategy to recognize captive portals accurately.
Handle Captive Portals Effectively
Taking the right approach to manage captive portals can be a win-win.
Once a captive portal log in succeeds, subsequent GlobalProtect app connections will succeed, ensuring uninterrupted internet connectivity.
Settings such as Disable Captive Portal Detection or User Controllable can be controlled by administrators via profile editors.
Test methods like simulation and auditing can evaluate your ACL effectiveness.
Years of work perfecting and piecing together proven reliable ACLs have shown just how crucial deep industry knowledge can be.
By making these practices a priority, you can take proactive steps to protect your network from unwanted access and security threats.
Not only do these measures protect your network, they ensure the best experience for users.
Broader VPN Considerations
Regular Client and Server Updates
Ensuring that your VPN client and server software is regularly updated is another key step to ensuring strong security practices.
Each update has a slew of bug fixes, many of which address vulnerabilities that hackers could use against you. Keeping these updated makes sure you’re reaping the rewards of the most current security practices and performance improvements.
Indeed, a leading VPN provider just had to issue an emergency update to address a publicly disclosed vulnerability.
Businesses that answered the call early avoided their own data breaches. When you take the initiative to prioritize updates, you’re lowering the risk of cyber threats and creating a more secure network environment.
Secure Tethering with VPNs
Protecting yourself with VPNs while tethering is crucial. As mentioned, tethering VPNs help protect your devices and identity, especially when connecting to public Wi-Fi networks.
This is especially important when it comes to protecting sensitive business information from eavesdroppers.
As an illustration, when workers are remote, tethering via a VPN secures every packet of information being transmitted, protecting against cybercriminals.
This practice protects sensitive information and helps organizations comply with data protection regulations.
Advise your workers to protect their online activities through VPNs.
By taking this approach, you position your organization to ensure transparency and trust in our ever-more interconnected global economy.
Best Practices for VPN Security
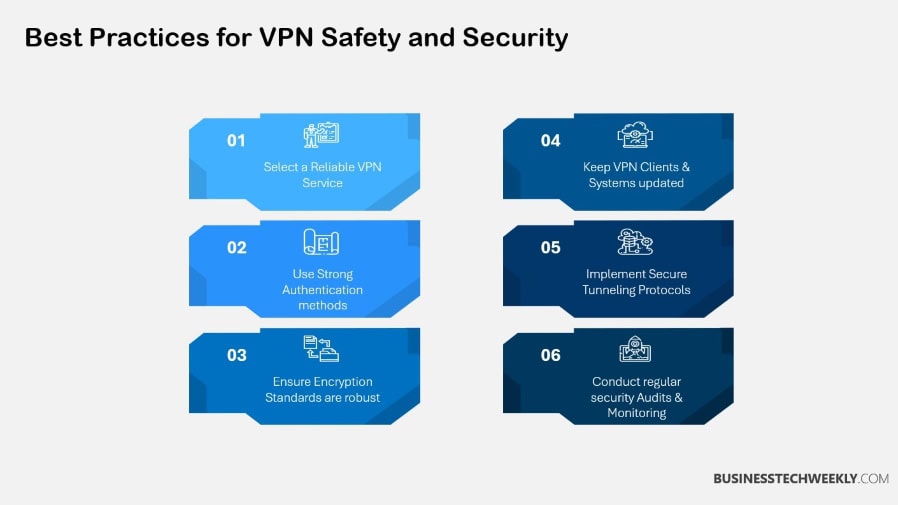
Configure for Optimal Security Settings
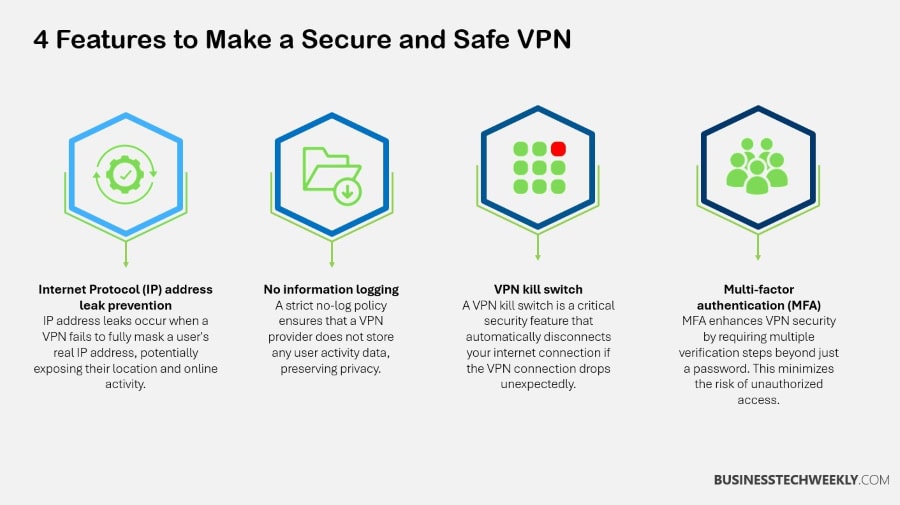
When choosing and configuring a VPN, security should always come first. You need to make sure that strong encryption protocols are being used, such as AES-256, which offers highly secure protection for data.
By requiring more than just a password, enabling multi-factor authentication ensures that even if an account’s credentials are compromised, unauthorized access is prevented.
Customizing default firewall rules to allow only authorized traffic and establishing secure remote access are best practices that can add additional layers of protection to your network.
For enterprises, these settings are more than technical requirements, they’re proactive investments in protecting your business.
Regularly Update VPN Software
It’s important to keep your VPN software up-to-date in order to protect against vulnerabilities.
Vulnerabilities in outdated software are often an open door to cyber attackers.
Frequent updates guarantee that you’ll be equipped with the most up-to-date security patches and features.
Automating updates makes this process easier and more efficient, limiting the chance of human error.
This practice truly hardens your network against the bad guys. It’s even more advantageous for small businesses that don’t have the IT bandwidth to spare.
Manage and Mitigate Vulnerabilities
Finding and fixing vulnerabilities before they can be exploited ensures that future breaches don’t happen.
Perform regular security audits and penetration testing to identify vulnerabilities.
Putting a vulnerability management plan in place allows you to methodically start attacking these weaknesses.
When you encourage an organization-wide culture of cybersecurity awareness, you give your employees the tools to identify threats and act quickly.
Secure VPN Traffic and Limit Access
Securing VPN traffic means encrypting data and implementing secure tunneling protocols.
Limiting the availability of the VPN solely to approved users minimizes the chance of outside access.
Enforcing network segmentation reduces the potential impact of any threats that may infiltrate the network.
These strategies offer a dual approach to user accessibility and protect your business operations from costly data breaches.
Educating Users on VPN Use
Train Users on Safe Practices
User training will always be a key component to any strong cybersecurity posture.
Identifying the downsides of VPN use is the first step in a more thoughtful understanding of how to use them strategically to improve security.
Educating users makes them more aware of which encryption protocols they need to be using to ensure data in transit is protected (IPsec, for example).
It’s a guide to what you may be overlooking, like weak passwords and expired software.
Through better education, training, and technology, you give your employees the tools they need to become your first line of defense against a costly breach.
Unfortunately, studies have found that as much as 80% of security breaches result from human error.
By educating users, we lower this risk and make all of our digital spaces more secure by default.
Monitor and Respond to Security Incidents
Smart monitoring and incident response security is essential. IT teams frequently have to customize user permissions, a daunting and time-consuming task.
Enforce Role-Based Access Control (RBAC) so users are given access solely to the resources they need.
This method reduces the risk of unauthorized access and mitigates the effects of any breaches that may occur.
By constantly monitoring VPN use and quickly responding to anomalies, you can keep your security posture strong.
This proactive approach ensures that your organization is always one step ahead.
Every day you stay one step ahead of new threats and protect your valuable digital assets.
Administering VPN Effectively
Implement Best Practices for Administration
When administering a VPN, you might think the main concern is protecting the data sent through the tunnel and keeping everything running.
In short, a VPN establishes an encrypted communication tunnel between two points, which is essential to protect data in transit.
Adopting phishing-resistant multi-factor authentication (MFA) and passwordless solutions improves security by leaps and bounds.
This method removes shared secrets, a key vulnerability that cyber adversaries often exploit. Authentication uses digital certificates and credentials exchange, while MFA adds another layer of security.
Remote-access VPNs protect the connection between an end-user’s device and the VPN endpoint with encryption.
On the other hand, site-to-site VPNs securely connect two endpoints over the internet. Regular updates are essential. The WannaCry attack reminded everyone just how dangerous it is to run legacy systems.
Ensure Continuous Security Monitoring
Monitoring is an imperative when administering a solid VPN.
Just the rise in VPN vulnerabilities—875% between 2020 and 2024—highlights that need. Ongoing 24/7/365 monitoring ensures that emerging threats can be discovered and remedied quickly.
While the majority of software bugs are found in closed-source systems, open-source solutions provide the transparency needed to identify vulnerabilities and patch them quickly.
MFA makes for a great deterrent, preventing unauthorized access from even occurring and boosting your organization’s security posture.
When these security measures are employed, your VPN is resilient to emerging threats.
What’s more, they provide the robust, secure and seamless global connectivity your business requires.
Key Points to Consider
VPN security is an essential element of securing your network. With the right practices, you increase both safety and efficiency.
By understanding protocols and properly configuring connections, you add layers to your defense.
Implement these VPN security best practices to fortify your security.
- When selecting a VPN, assess your security needs to ensure the service aligns with the sensitivity of your data and connectivity requirements. Consider factors such as device compatibility and usage patterns for optimal protection.
- To ensure data transmission remains secure, look into different encryption protocols and choose between integrated or third-party VPN clients. Knowing the difference between mandatory and optional protocols can make a big difference in your ability to meet security benchmarks.
- For accessing geo-blocked content, select full-device or app-based VPN setup. Consider split tunneling capabilities to ensure user performance needs and security requirements are met.
- Routine updates to VPN clients and servers are important to patch vulnerabilities that can weaken defenses and compromise security. Secure tethering becomes critical when multiple devices are sent to the same network.
- Prioritize VPN security—follow VPN best practices by ensuring strong encryption and authentication mechanisms are configured. Ensure timely updates of your VPN software, and proactively handle vulnerabilities by monitoring them continuously.
- Make sure users are trained on how to use a VPN safely, as well as how to report potential security incidents so you can respond quickly. Real-time threat detection and response Continuous security monitoring is key to real-time threat detection and response.
VPN Security Best Practices: FAQs
What are the benefits of using a VPN?
A virtual private network (VPN) hides your IP address, ensuring a seamless VPN experience while keeping you anonymous online.
It encrypts all of your data, enhancing your security posture against prying eyes and hackers, and allows access to geo-restricted content.
How do I choose the right VPN protocol?
Select according to your security requirements. OpenVPN offers the best security available for a comprehensive VPN experience.
WireGuard is extremely light and fast, while PPTP isn’t very secure, making it fine for low-stakes activities.
Why should I assess the need for a VPN?
Understanding what you need will help you decide whether a virtual private network is right for you and your security and privacy objectives, ensuring a seamless VPN experience while protecting against wasteful spending.
What are the best practices for VPN security?
Employ strong password policies and multi-factor authentication to enhance your security posture.
Keep your VPN software updated to ensure a seamless VPN experience and review logs regularly for signs of abuse.
How can I educate users on VPN use?
Hold hands-on training sessions on the importance of using virtual private networks for secure connections, and give staff simple guides to follow.
Post security tips and answers to frequently asked questions regarding VPN services to foster an understanding of who might be looking to attack you and why secure practices are essential.
What is captive portal detection in VPNs?
Captive portal detection automatically recognizes networks that need authentication, such as some public Wi-Fi.
Virtual private networks (VPNs) can tunnel through these obstacles, ensuring a seamless VPN experience with consistent, secure connectivity without interruption.
How do I effectively administer a VPN?
Establish strong usage policies and access controls for your virtual private networks.
Conduct a quarterly audit of VPN services to ensure compliance.
Software should be updated and patched quickly to maintain a secure connection.

