VPN Encryption: How does VPN Encryption work, and why does it matter?

Virtual Private Networks (VPNs for short) use encryption to make your transmitted data completely unreadable by any person that intercepts it. VPN encryption is itself a complex and specialized topic. However, despite its complexity, VPN encryption benefits many people, and it’s not difficult to see why.
But did you ever consider how does VPN encryption work? Below, we seek to understand VPN encryption in more detail, covering the supporting protocols and ciphers and ultimately understanding how these components combine to form the foundation for a quality VPN service.
On this page:
What is a VPN?
A VPN is an internet-based service that establishes a secure connection to another network. It conceals your IP address and encrypts your traffic, preserving your privacy against your Internet Service Provider (ISP), government, and other prying eyes.
A typical VPN consists of a global network of servers maintained by a VPN service provider. Two significant events occur when a user subscribes to and connects a device to a VPN service:
- All traffic between the device and the network is encrypted
- This encrypted traffic passes through an intermediary server, the location of which is selected by the user
If all your traffic is encrypted, your online activity cannot be tracked, and all your data is safe. Nobody who intercepts your data will be able to decipher it.
Your ISP may see everything you do online without a VPN, including the websites you visit, the programs you use, and the files you download. However, this isn’t possible if you use a VPN.
Related: Is using a VPN Legal?
What is VPN Data Encryption?
The data from the device used with the VPN client is encrypted and transferred to the VPN server through a VPN tunnel. This tunneling procedure guarantees that your data is encapsulated, preventing anybody from intercepting, modifying, or monitoring your activities.
During VPN encryption, the data on your device is converted, through an algorithm, from a readable format to an encoded and unreadable format.
This encoded information can only be deciphered with the correct decryption key, which is contained within your VPN.
Types of Encryption
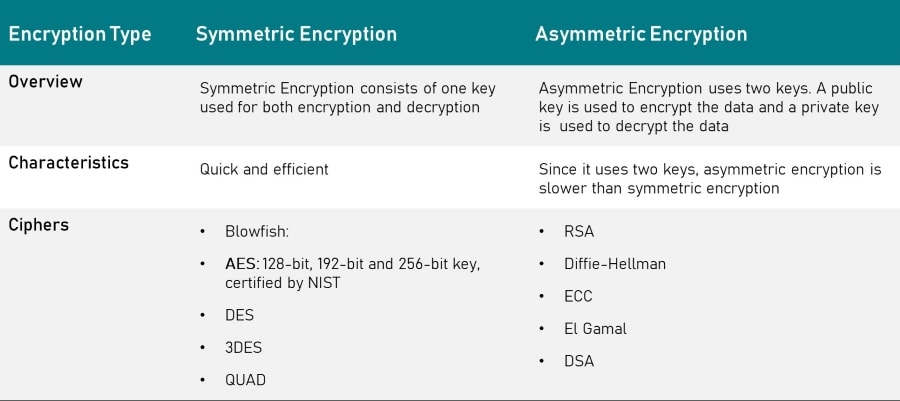
VPN encryption comprises of two types, namely, symmetric encryption and asymmetric encryption:
- Symmetric Encryption: A single key encrypts and decrypts the data. This means that you and the VPN server use the same shared key. Symmetric encryption is efficient and fast, resulting in lower processing power to encrypt and decrypt the data. Because of this, symmetric encryption is practical when quickly transmitting large amounts of data.
- Asymmetric Encryption: Uses 2 different keys, a public key (used to encrypt the data) and a private key (used to decrypt the data). Also known as Public-Key Cryptography, Asymmetric Encryption can be convenient. However, if a Private Key is lost, it can not typically be restored.
Both types of encryption are used in a VPN connection. Since asymmetric encryption is not very fast or efficient, it’s only used at the start of a session (during a process known as a handshake) to exchange the faster symmetric encryption keys.
Once the VPN connection is established, all data is encrypted and transmitted using symmetric encryption.
VPN Encryption Ciphers
The algorithms used for encryption and decryption are known as ciphers. Each of these ciphers falls into the above-mentioned types, either symmetric or asymmetric encryption.
What is a VPN Encryption Handshake?
A VPN encryption handshake is a communication between two devices that occur automatically following pre-defined steps.
It provides a mechanism for how the VPN client and VPN server generate the encryption keys needed for communication (encryption and decryption in this case).
During the handshake, the VPN client device and server do the following:
- Generate encryption keys
- Confirm the VPN protocol which will be used
- Choose appropriate cryptographic algorithms
- Authenticate one another using digital certificates
VPN Protocols
The security of your connection is determined by the VPN protocol, which provides authentication and encryption. These define the communication between your device and the VPN server, ensuring your device communicates with a trusted VPN server (authentication), and the connection is secured against outsiders (encryption).
VPN Providers typically use multiple protocols to ensure the connection is secure. Here are some of the prevailing VPN protocols:
- Point-to-Point Tunneling Protocol (PPTP): Although PPTP is fast, it has weak security
- IPsec: A secure suite of network protocols with high-security features. One of the benefits of IPsec is that the protocol does not notify the endpoint application that data is being encrypted
- Layer 2 Tunneling Protocol (L2TP): Since L2TP does not provide any encryption on its own, it is typically used in conjunction with IPsec, forming a highly secure pairing (referred to as L2TP/IPSec)
- Secure Socket Tunneling Protocol (SSTP): Is far more secure than PPTP or L2TP/IPsec, this protocol was developed by Microsoft to secure online data and traffic for Windows OS
- Internet Key Exchange Version 2 (IKEv2): Handles traffic by establishing the security association within an application suite
- SoftEther: A more recent VPN protocol recognized for its security, speed, and stability
- WireGuard: A newer VPN protocol with fewer security holes, WireGuard is open-source and only uses a single cryptographic suite
How Does VPN Encryption Work?
Once you press the “Connect” button to connect to a VPN service, the following steps are executed:
- Asymmetric Key Exchange (VPN Handshake): A secure connection is established between your VPN client device and the server (hosted by the VPN provider). This connection is governed by the VPN Protocol and is established via a VPN handshake. As such, secure communication is set over an open medium (the internet).
- Symmetric Key Exchange: The key used when transferring actual data generated by the encryption algorithm and exchanged. This allows your data to remain secure, even if your encrypted connection is compromised.
- Data Transmission: When you transmit data, the encryption algorithm uses the symmetric key generated in the step before to encrypt all your data.
- Integrity Algorithms: Integrity algorithms verify that no one has altered the data while in transit. A mathematical hash function is used to scramble a part of the data you’re sending. The receiving server can validate your data using the hash function and the private key. A match means the data hasn’t been interfered with.
Why VPN Encryption is Important
Primarily, VPN encryption protects confidential data (such as credit card numbers, bank account information, and login passwords) from cyber criminals.
In addition, VPN encryption prevents your government, ISP, and advertising from monitoring your Internet activities.
Why is this important? Well:
- Avoids putting your life at risk in regions where some internet behaviors are outlawed
- It safeguards you against unjust DMCA notices, hefty penalties, and even jail time if you download torrents
- Circumvents your ISP from restricting your bandwidth since they cannot monitor your online activities
- Reduces “tailored” spam adverts and lessens the risk that your ISP would sell your internet data to advertisers
Do all Providers offer VPN Data Encryption?
Not always. Free VPNs are somewhat risky since they may promise to provide encryption when they may not safeguard your data.
Moreover, even when free VPNs provide encryption, it is typically a poor cipher, dated encryption, and less secure VPN encryption protocols.
You should use a trustworthy premium VPN service if you want genuine Internet security.
Considerations when choosing a VPN Service
A wide range of VPN services are available. However, when choosing one, you should consider using one that fulfills the below criteria:
| Criterion | Ideal |
| Server coverage | Worldwide |
| Encryption | AES-256 |
| VPN protocol | OpenVPN, IKEv2, or WireGuard |
| VPN server obfuscation | Possible |
| Device support | Must be compatible with all your devices |
| RAM-only server | Must have if you want all your data to be wiped when you log off |
| Privacy policy | Must indicate the provider doesn’t log your sensitive information without a valid reason or your consent |
Which VPN should you get? VPNs that use the Best Encryption Methods
These are our top three VPN subscription service providers. They use the most effective encryption methods explored above.
In addition, they provide many other critical features, such as a global network of lightning-fast VPN servers. In addition to encryption methods, this is vital to have a valuable and secure VPN service.
NordVPN
This user-friendly VPN provider has developed some of the most stringent systems backed by robust security policies to ensure customer privacy. It uses many security protocols at once to further strengthen its individual protocols.
- Maintains a no logs policy: When seeking a VPN Service, ensuring that the VPN provider doesn’t keep logs of its users’ online activity means minimizes the risk of your data being sold or provided to authorities or prying eyes, either intentionally or inadvertently
- Double data encryption technology and kill switch: NordVPN’s kill switch feature allows the internet connection to drop in the event the VPN connection drops, thereby ensuring that user identity is always hidden. The use of double data encryption makes NordVPN even more secure than its contemporaries
- Multiple protocols: NordVPN allows the user to select from various protocols, including OpenVPN, IPSec, PPTP, and IPSec/IKEv2, allowing for both newer and legacy devices to be used with NordVPN’s services
Pricing:
- $11.95 per month
- 30-day money-back guarantee
Sign up with NordVPN
ExpressVPN
ExpressVPN provides a robust VPN service with reasonable subscription options. The level of high service, with unparalleled security features using some of the most effective encryption methods conceivable, justify the monthly fees.
- OpenVPN protocol: Recognised as one of the best protocols currently available
- 256-bit AES encryption: One of the most secure encryption methods sanctioned by the US Government
- 30-day refund, if you don’t like ExpressVPN
Pricing:
- One month: $12.95
- Six months: $9.99
- 15* months: $6.67 *Three months free
Sign up for ExpressVPN
CyberGhost
CyberGhost has an incredible variety of security features. Considering that it is quick and easy to use due to its broad feature set, CyberGhost is a highly competitive VPN secure VPN service.
- No logs policy to ensure that online user activity is never recorded.
- AES 256-BIT encryption: US government-backed encryption using a 2048-BIT RSA Key. Also uses the SHA256 authentication algorithm demonstrating the company’s dedication to customer privacy.
Pricing:
- $2.90 a month (based on a 2-year subscription)
- Monthly subscription – $10.99
- 6 months from $7.99 per month
- Every plan comes with a 60-day money-back guarantee
Sign up with CyberGhost

