Your Guide to Chain of Custody in Digital Forensics

On this page:
- What is Chain of Custody?
- Key Principles of Chain of Custody
- Chain of Custody Process: A Step-by-Step Guide
- Best Practices for Digital Evidence Preservation
- Common Pitfalls to Avoid
- Chain of Custody for Different Digital Sources
- Legal Standards and Chain of Custody
- Tools and Technologies for Chain Management
- Challenges in Maintaining an Unbroken Chain
- Key Points to Remember
- Frequently Asked Questions
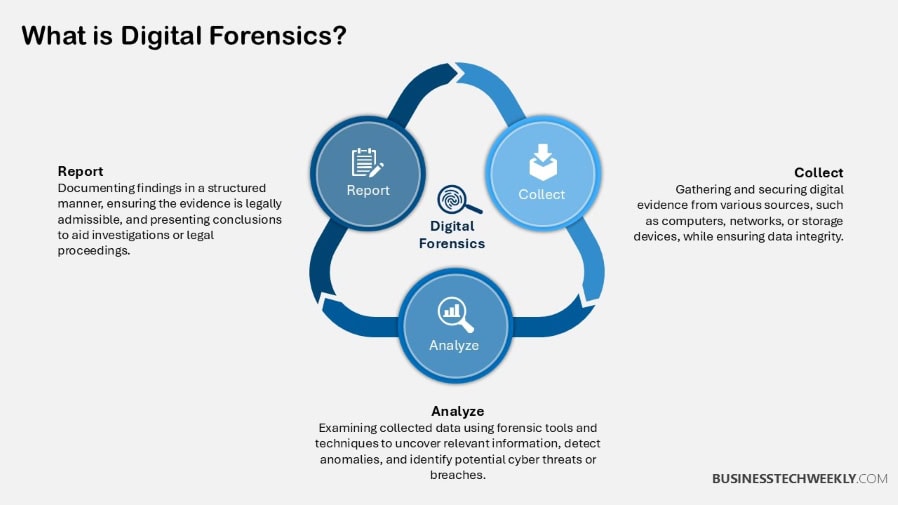
What is Chain of Custody?
Chain of custody is focused on rigorously tracking evidence. It begins with the very first collection of evidence and extends all the way through presentation of that evidence in court.
This process documents each step taken with the evidence.
It provides a consistent chain that maintains the integrity and authenticity requirement of the evidence.
For investigators and legal professionals, maintaining this documented trail is vital to ensuring that the evidence remains untampered and credible throughout an investigation.
1. Define Chain of Custody
The chain of custody serves as a touchstone, ensuring that evidence has not been altered, destroyed, or otherwise compromised. B
y ensuring that there is an obvious, strong and documented chain of custody forensic professionals are working to protect the integrity of the evidence.
This is particularly acute for the credibility of climate investigations and the administration of justice more broadly.
As an illustrative example, in matters involving digital forensics, a definitive chain of custody is often determinative in the legal proceedings.
Digital evidence, including things like email logs or encrypted files, need to be changed in order to not be admissible in court.
A properly maintained chain of custody helps protect legal teams by ensuring the evidence they are presenting has not been altered or tampered with.
2. Why Chain of Custody Matters
Digital evidence presents distinct challenges, as its intangible nature adds complexities not present with physical evidence.
Digital evidence, unlike physical evidence, can be easily copied or tampered with.
This creates deep potential for mistakes if we aren’t willing to innovate our old ways. This is where digital forensics professionals come in to make a difference.
Their duties require documenting every step from data collection to analysis, handling witness testimony all the way through court proceedings, and keeping evidence safe.
For instance, during a cybersecurity breach investigation, tracking how digital logs are handled, stored, and analyzed is critical to proving their authenticity.
3. Chain of Custody in Digital Forensics
In digital forensics, a thorough, well-documented chain of custody helps ensure that the evidence is admissible in court.
Without it, evidence runs the threat of being deemed inadmissible, due to previous cases in which evidence is considered tainted by mishandling.
In a network fraud investigation, neglecting to track who logged into a suspect’s server might make the investigative conclusions inadmissible.
Compliance with best practices helps to ensure that any digital evidence will stand up to legal scrutiny.
4. Impact on Legal Admissibility
Control measures and accountability are foundational to chain of custody.
Keeping track of who’s had access to evidence and when protects against any unauthorized access.
This principle encompasses all personnel being accountable, resulting in a repeatable, transparent process that best ensures legal admissibility.
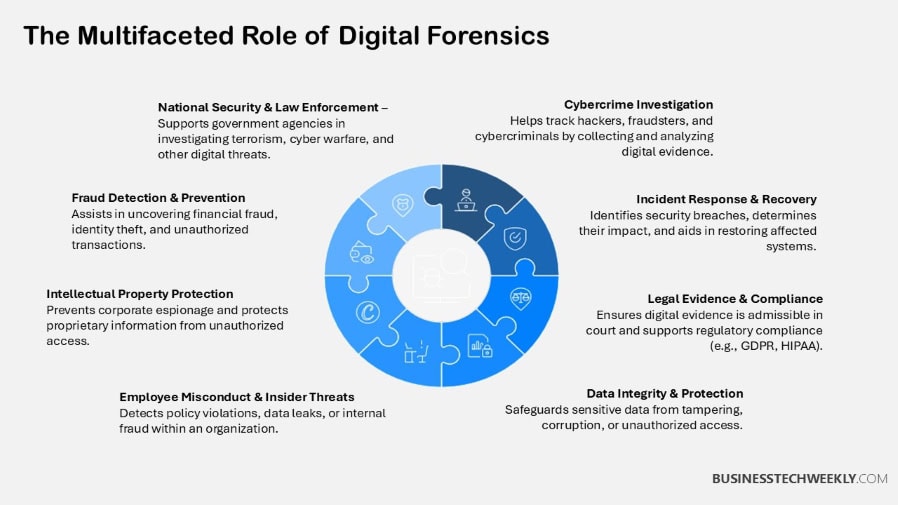
Key Principles of Chain of Custody
When handling digital evidence, the chain of custody (CoC) plays a critical role in ensuring its reliability in legal proceedings.
This structured process safeguards the evidence’s integrity from the point of collection to its eventual presentation in court, minimizing the risk of tampering or loss.
By following the three key principles—control, continuity, and documentation—the integrity of the evidence is maintained, keeping it admissible in court.
1. Control and Accountability
Ongoing, unbroken control of the chain of custody is key to preventing gaps that would otherwise disrupt the credibility of evidence.
The role of authorized personnel is critical in this process. If a forensic investigator turns over evidence to an analyst, they need to go through an established procedure on record.
This chain ensures transparency and integrity at all levels.
Each transfer should have a clear chronological record of that transfer showing date and time of transfer, individuals in chain of custody, and physical condition of evidence.
A simple application scenario includes employing access-controlled environments.
In secure labs, only trained evidence handlers can have access to evidence. This further strengthens accountability and minimizes opportunities for tampering or unwanted access.
2. Maintaining Data Integrity
Building confidence in data integrity starts with documentation plus secure and monitored handling practices.
Record of Custody Records should have specific timestamps, signatures, and detailed descriptions of the evidence.
Standardized chain of custody forms can help streamline this process, minimizing gaps and discrepancies and improving transparency.
Hashing techniques, like MD5 or SHA-256, are frequently used and invaluable tools to ensure data integrity.
These methods produce one-of-a-kind digital fingerprints, allowing investigators to ensure that no tampering has taken place in its chain of custody.
For example, recalculating a hash value when evidence is transferred makes certain the authenticity of that piece of evidence has not been compromised.
3. Ensuring Continuity
The first identification and collection of evidence is crucial. Evidence requires rigorous documentation and collection procedures to avoid the introduction of contamination.
For instance, putting a suspect’s computer in an electromagnetic shielded bag protects it from external signals.
Providing consent, where possible, improves the credibility of the entire process as well.
4. Comprehensive Documentation
Tamper-evident seals should be used whenever feasible, giving visual confirmation of any unauthorized access.
A drive that ends up improperly labeled in a case of financial fraud, for example, could put the entire investigation’s credibility at risk.
Transparent, secure practices build public trust while making tracking through each step of the CoC process effortless.
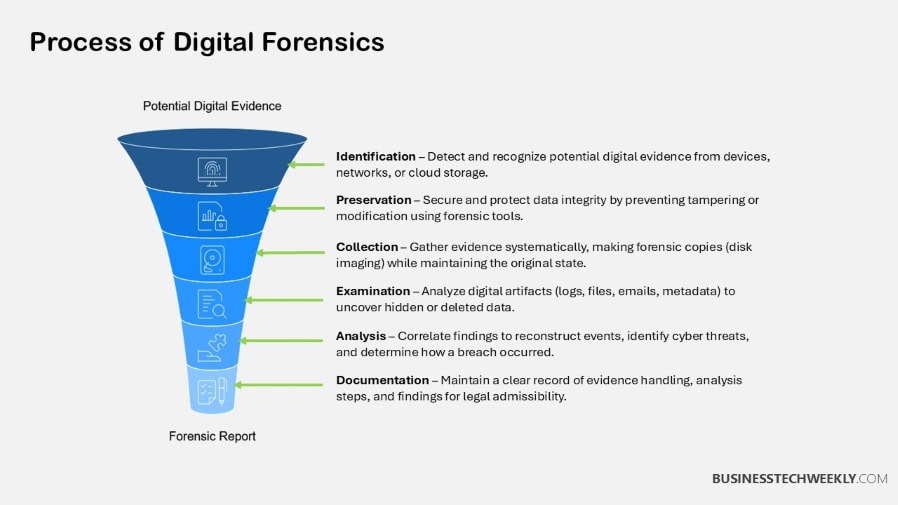
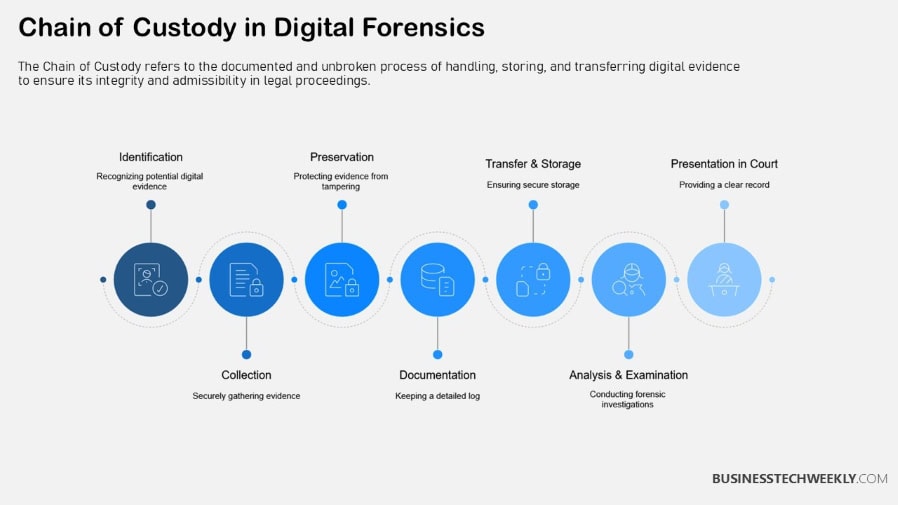
Chain of Custody Process: A Step-by-Step Guide
It protects that electronic evidence from being tampered with from the second it’s discovered to its ultimate display before a judge or jury.
By adhering to established custody cyber security protocols, organizations significantly shield themselves from the dangers of data tampering, loss, or mismanagement.
This protection is especially important today, as criminal investigations and prosecutions rely heavily on digital forensics expertise.
1. Identification and Collection of Evidence
The collection and preservation of digital evidence is crucial in establishing its chain of custody.
This starts with understanding devices or data sources through a forensic lens while maintaining a chain of custody and originals. Forensic analysts that work for law enforcement usually employ validated tools such as EnCase or FTK.
Such tools eliminate the risk of modifying data before extraction, which can potentially violate prescriptive standards from NIST and the NIST Cybersecurity Framework.
For example, in the case of faulty malicious server data retrieval, they stop the server from modifying the hard drive when reading data back.
Each and every step, from photographing devices to creating timestamps, needs to be recorded meticulously.
This detailed process creates a clear chain of step by step occurrences, which is often required for court admissibility.
2. Secure Packaging and Labeling
Packaging and labeling are much more than cosmetic touches. Seal each item of evidence in tamper proof containers such as anti-static bags for hard drives.
Label them with a unique identifier to help prevent any mix-ups.
These labels need to identify a sample with information such as case number, date of collection, and handler name.
Clear delineation not only avoids confusion, but enhances trustworthiness in the face of legal challenge.
Visual documentation, including images of the evidence in situ, helps provide context for non-technical stakeholders—especially juries.
3. Transportation and Storage Protocols
Evidence requires that it be transported and stored in controlled environments that provide for physical safeguarding as well as limited access to those without consent.
Logs documenting each interaction—be it passing a USB stick or opening a milk crate storage compartment—are critical.
If, for instance, a digital evidence locker has 24/7 access control, limited access, environmental controls which manage humidity and temperature for long-term preservation.
Providing documentation at every step encourages accountability and transparency, creating a strong foundation for subsequent investigations.
4. Examination and Analysis Procedures
Forensic analysts use write blockers to ensure that forensic copies of original data retain the integrity of that data.
These hardware or software tools serve as additional safeguards, ensuring no write operations can occur on accident while your analysis is ongoing.
Ensuring compatibility between forensic tools and write blockers is non-negotiable, as any incompatibility can jeopardize the integrity of evidence.
To avoid discussion about possible loss of original data, analysts always work with forensic images rather than original data.
They maintain authenticity through hash verification methods like SHA-256.
5. Reporting and Presentation of Findings
The fifth and last step is to convey discoveries by way of an in-depth forensic report.
With NIST’s focus on clarity, objectivity, and accuracy in mind, this report should provide that evidence in a clear and concise manner.
Teasers like this show how visual aids, like timelines or animated screenshots, can increase understanding, especially when it comes to legal matters.
Confirming these results, hash values and metadata comparisons ensure fidelity.
This narrative, framed presentation connects the technical and legal spaces in a meaningful way, helping to inform a court’s deliberation.
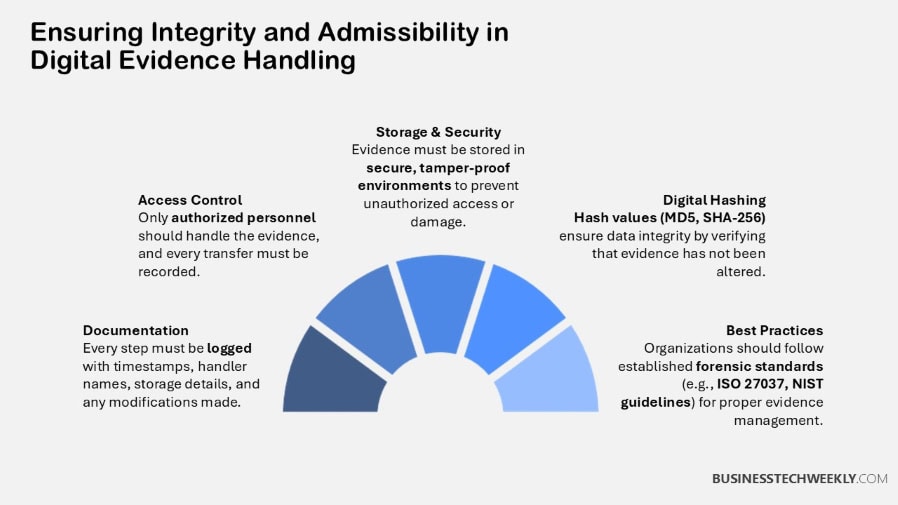
Best Practices for Digital Evidence Preservation
Comprehensive digital evidence preservation is crucial for ensuring impartiality and integrity throughout the digital forensics investigation process.
From the initial data collection to its presentation in court, maintaining a systematic approach is essential for safeguarding the entire case.
Adhering to these best practices enhances compliance and reliability, reinforcing the importance of custody cyber security in the management of digital evidence.
1. Document Every Action Taken
Keeping a complete log of each transaction is really important. Document every step, from collection through transfer.
Specifically, include the names of personnel, applicable timestamps, and the nature of the interaction with personnel.
This careful method does more than just keep out prying eyes — it creates a chain of custody.
For instance, if evidence collected from IoT devices or flash drives is accessed without proper documentation, its admissibility may be compromised.
The National Institute of Standards and Technology (NIST) stresses that the chain of custody must justify why and under what conditions evidence is transferred, ensuring transparency at every stage.
2. Use Write Blockers
Write blockers are proven best practices tools for maintaining the integrity of evidence.
These devices protect evidence from unwanted or unauthorized changes during analysis by limiting the contents to read-only modes.
To ensure chain of custody and data integrity, well-known hashing algorithms such as MD5 or SHA-256 must be used.
Digital fingerprints hash values, or checksums, are critical components of any evidence file, verifying that the contents have not been changed or tampered with.
Creating evidence documentation that captures these hash values at each step makes it easy to establish the chain of custody and strengthens your case’s credibility during court proceedings.
3. Create Forensic Images
Capturing forensic images and forensically sound duplicates enables investigators to work on duplicates while preserving the original data in a reliable manner.
This practice is consistent with the best practice of never manipulating the original evidence.
Lack of transfer documentation for evidence can result in major holes in the chain of custody, inviting challenges to the authenticity.
Creating and following standardized protocols for documenting chain of custody transfers limits those risks.
4. Secure Storage Environment
The final piece of preservation puzzle is appropriate storage of digital evidence. Controlled temperature and humidity secure environments protect items from physical damage.
Implementing secure, tamper-proof storage solutions will help keep out prying eyes.
Regular audits of facilities help ensure compliance with established protocols while mitigating the risk of losing the 80% of evidence often mishandled due to improper conditions.
5. Limit Access to Evidence
Limiting exposure to certified personnel reduces dangers associated with evidence mismanagement.
Evidence maintained in environments with rapid temperature or moisture changes can be impacted, leading to a loss of integrity and reliability.
Proper environmental controls and limiting access to authorized individuals help to maintain the integrity of the data.
6. Verify Integrity with Hashing
Last but not least, maybe the most important, precisely placing evidence into the hands of trained professionals is critical.
Wrong handling by personnel without adequate training can lead to permanent harm.
Ongoing training and certification for forensics teams ensure adherence to best practices and bolster the credibility of the chain of custody process.
A compromised chain of custody can lead to the dismissal of evidence in court, underscoring the necessity of meticulous documentation and handling of digital evidence.
Common Pitfalls to Avoid
Digital forensics relies heavily on the successful preservation of the chain of custody. This guarantees that items of evidence, including electronic evidence, remain unaltered from their initial collection through the digital forensics investigation process.
Many pitfalls can undermine this custody cyber security process, particularly in today’s dynamic digital ecosystems. Understanding these pitfalls can help you safeguard the integrity of your evidence and maintain compliance with legal and ethical standards.
Handling Cloud Storage Data
Cloud environments present unique and significant challenges for the handling of digital evidence.
Unlike physical storage, data in the cloud is subject to the service provider’s policies, including retention periods and access permissions. Without this in-depth knowledge of these policies, you put yourself at risk for losing out on key evidence.
For example, if evidence is not downloaded within a set period, it may be automatically deleted.
To avoid against this, set definite procedures to obtain and record cloud-based evidence. Make sure timestamps, access logs, and metadata are retained when collected.
Working with providers that have established forensic-grade/forensic-compatible access tools in their milieu can make this step seamless.
Solutions such as chain-of-custody software using cloud-based technology can allow for a more seamless experience, providing easier tracking and lowering the chance of operator error.
Failure to Document Transfers
Mobile devices are treasure troves of key evidence, but their advanced encryption and data protection features can present challenges to officers.
Missing to thoroughly record each piece of data being transferred opens the possibility for charges of tampering. Use forensic tools.
Only use specialized forensic tools that allow you to extract the data without modifying the device in question.
Tools such as evidence baggies can shield devices or external signals during transport and storage, safeguarding the integrity of the gathered data.
Having a strong tracking system, like barcodes or RFID, is necessary to record and indicate where and how transfers occurred.
Each time evidence passes between analysts, we need to document with a clear audit trail. This helps us to provide an ironclad chain of custody and have the evidence be admissible in court.
Working on Original Evidence
First, original evidence such as network logs is irreplaceable. Editing these logs in place via the OS will corrupt the data on the media.
Instead, make certified duplicates for forensic examination.
Thorough documentation is just as important. Critical context like timestamps, IP addresses, and what the system was configured to do should all be documented without fail.
Improper Storage Conditions
These complexities IoT devices bring to the digital forensics world include the inconsistent data formats, protocols, and the data-rich environments that they create.
Evidence from these devices requires storage conditions that safeguard the devices if environmental factors, for example temperature or humidity, can compromise the evidence.
As much as 90% of digital evidence is lost through mishandling and failure to store it properly, so facilities that securely store digital evidence are essential.
Thorough documentation throughout the collection process protects the integrity of your data.
Lack of Qualified Personnel
Legal standards for use of digital evidence demand an unbroken chain of custody.
Breaks in this chain of custody can make evidence inadmissible, resulting in a drastic legal fallout.
Collaborating with an experienced digital forensics team helps avoid improper handling, minimizing risks and strengthening admissibility at trial.
Chain of Custody for Different Digital Sources
Controlling a strict chain of custody is imperative when handling digital evidence.
It provides assurance that the data is not altered from the time it is collected to when it is presented in the courtroom. Digital evidence can originate from many different sources.
This starts with detailed forensic descriptions, including filenames, MD5 hashes, device serial numbers, and media such as hard drives, IoT devices, or cloud storage.
The process involves four main stages: collection, preservation, transportation, and analysis.
This oversight can threaten the forensics of as much as 90% of the evidence thereby making it inadmissible in a court of law. Following rigorous chain of custody requirements is crucial to maintain evidentiary value and protect against contamination.
1. Handling Cloud Storage Data
When it comes to cloud storage, there are additional complications with the chain of custody.
Expert witnesses are invaluable to validating this process during legal proceedings. Their testimony can provide transparency by clarifying how evidence from cloud systems was collected, preserved, and analyzed.
For example, they would need to show how the metadata has been extracted, including the timestamps and access logs, to prove authenticity.
That’s why it’s incredibly important to choose experienced professionals with deeper knowledge of cloud environments. Their resulting insights can go a long way to connect technical complexities with legal standards.
Doing this protects the evidence from appearing compromised and losing its credibility in a court of law.
2. Managing Mobile Device Evidence
Forensic software suites play a crucial role in the digital forensics investigation process, helping investigators effectively process and manage evidence obtained from mobile devices.
Tools such as Cellebrite and Magnet AXIOM enhance capabilities for documenting the chain of custody and tracking evidence.
They meticulously record each step in the procedure with a detailed chain of custody, creating an easy-to-follow audit trail that is essential for safeguarding the integrity of electronic evidence.
Using reputable software is critically important to protect the integrity of the evidence and avoid legal headaches.
These tools can identify, parse, and extract data such as filenames, call logs, and text messages while preserving MD5 hashes for later verification.
This level of precision is vital for ensuring the trustworthiness of the digital evidence collection process.
Ultimately, employing such advanced forensic tools eliminates doubt and guarantees the reliability of the chain of custody, which is essential for impactful investigations in the realm of electronic crimes.
By maintaining a proper custody protocol, investigators can ensure that all collected evidence remains intact and credible throughout the entire case.
3. Dealing with Network Logs
Write-blocking hardware is essential in forensic investigations where network logs are implicated.
Input capture Write-blockers, including Tableau and CRU devices, are designed to safeguard against unintentional data changes while obtaining digital evidence. They provide read-only access, making a bit-for-bit copy of the original state of evidence.
Hardware-based blockers are often used for hard drives, whereas software-based blockers are more appropriate for virtual environments.
Putting these tools into use protects digital evidence, empowering investigators to protect continuity and prevent tampering or contamination during analysis.
4. Securing IoT Device Data
IoT devices usually store sensitive information that needs to be stored in a safe and secure manner.
Encrypted drives and access-controlled systems are useful for preserving digital evidence. These drives or systems are inherently encrypted with access controls.
Encryption protects against unauthorized access, and access controls protect by limiting who can even handle this evidence to authorized personnel.
For example, IoT data storage on encrypted USB drives secures not only the filenames but the device IDs and configuration files.
These steps are particularly important because they help ensure a strong chain of custody.
More importantly, they help to make sure that the evidence remains admissible in investigations and court proceedings.
The chain of custody process in digital forensics involves four key stages: data collection, examination, analysis, and reporting, each requiring thorough documentation to maintain evidence integrity.
Legal Standards and Chain of Custody
The chain of custody forms the backbone of digital forensics, maintaining the integrity and reliability of digital evidence from collection to courtroom presentation.
Its stringent record-keeping prevents any tampering with evidence, retaining its integrity and trustworthiness, which protects its value as admissible evidence in court.
The process from ‘cradle to grave’ including sample collection, analysis, reporting, and monthly submission to the county covers every step to avoid any chance for contamination or tampering.
1. Admissibility in Court
Hashing Algorithms and Digital Integrity
Hashing algorithms are part of the foundation of digital evidence, and an essential tool in proving that evidence is authentic. These algorithms produce special digital fingerprints for data that make even the smallest change in data obvious.
Some algorithms frequently used in forensic investigations are MD5, SHA-1, and SHA-256.
For instance, when examining data retrieved from an IoT device, generating and documenting hash values at each stage, collection, transfer, and storage, provides a robust verification mechanism.
This practice serves to protect the integrity of the evidence and therefore is most defensible in court.
Remote Data Acquisition Issues
Collecting data from such remote and sometimes hazardous environments can be imposing from a logistical and security perspective.
Creating protected, encrypted channels through which remote evidence collection is transmitted is essential for protecting both the evidence and the people involved from interception.
A forensic team, for example, handling evidence from a cloud server must follow strict protocols to document every step, from initiating the connection to finalizing the data transfer.
Having clear procedures in place for maintaining and monitoring a chain of custody is key to maintaining that chain, especially when dealing with remote sources.
2. Impact of Tampering
Managing Evidence in Distributed Environments
Distributed data environments, like multi-location server farms further complicate evidence handling.
Maintaining the integrity of the chain of custody through all these sites needs uniform protocols and collaboration between teams.
A centralized and secure documentation system, for instance, can easily log each piece of evidence’s movement and handling, lowering the chances of mismanagement.
Coordination Across Teams
Strong lines of communication from forensic analysts, IT staff, and legal teams are essential.
This coordination with law enforcement, prosecution, and defense guarantees that all parties work to the same standards, protecting the integrity of evidence.
A unified digital platform can simplify the documentation of any evidence-related activity. It produces a single, comprehensive record that stands up to courtroom challenges.
3. Expert Witness Testimony
Long-Term Integrity Maintenance
Over long timeframes, ensuring evidence integrity requires continual audits and oversight.
Documentation, such as chain of custody forms, establishes a reliable timeline for handling, ensuring that evidence withstands scrutiny during expert testimony.
Keeping thorough chain of custody logs for any digital evidence extracted from a video recording substantiates the video’s authenticity.
This is the case even many years after the evidence was collected.
Implementing blockchain technology in digital forensics can enhance the integrity of the chain of custody by providing an immutable and decentralized record of evidence handling.
Tools and Technologies for Chain Management
Digital forensics requires the utmost integrity of evidence throughout its digital forensics chain and lifecycle.
Tools that ensure the custody cyber security process are critical. While encryption serves as a vital tool for data protection, it can complicate the collection and use of digital evidence.
Understanding these challenges and the technologies that address them is essential for businesses and professionals managing sensitive information.
Forensic Software Suites
Forensic software suites are still the cornerstone of digital investigations, particularly in the realm of custody cyber security.
Platforms such as EnCase and CAINE offer powerful tools to examine digital evidence while preserving the evidentiary chain of custody.
EnCase, recognized as the industry standard for creating forensic images of drives, enables low-risk and in-depth analytic investigations on media copies, thus mitigating the dangers associated with conducting live analysis
CAINE, a Linux-based distribution, integrates several tools for forensic purposes, providing the flexibility necessary to handle various circumstances.
Open-source alternatives, such as Wireshark and HashKeeper, complement the ecosystem by addressing niche needs that commercial platforms often overlook.
Wireshark is particularly powerful for packet sniffing, making it indispensable for understanding and analyzing network traffic, which is crucial for any digital forensics investigation.
At the same time, HashKeeper removes duplication to speed database file hash investigations.
Tools for live memory forensics, such as WindowsSCOPE, are becoming increasingly popular. They address the increasing need to review volatile data, particularly as mobile operating systems become more prevalent in investigations.
Write-Blocking Hardware
The use of write-blocking hardware is to prevent digital evidence from being modified during the process of acquisition.
For example, Tableau forensic bridges ensure no unintentional changes are made to source data, keeping its admissibility in court intact.
In this light, interrogating unallocated disk space or salvaging corrupted and obliterated data files takes on a new importance.
Even small alterations can strip the evidence of its credibility.
Secure Storage Solutions
Secure storage solutions — whether physical, digital, or both — are vital for maintaining the chain of custody after acquisition.
Encrypted drives and tamper-eviding seals keep data safe from both facility breaches and internal tampering. Cloud-based forensic storage options, compliant with data protection legislation, provide secure, scalable, and auditable evidence storage for long-term retention.
Beyond the above, these solutions make it easier for auditors, legal teams, and enforcement agencies to collaborate in the event of cyberattacks or lawsuits.
Hashing Algorithms
Hashing algorithms such as MD5 and SHA2 (SHA-256 or SHA-512) are used to ensure the integrity of digital evidence.
Using the hash-generating algorithms, which allow creating multi-dimensional unique hash values, guarantees that the data stays unaltered during any data analysis process.
FTK (Forensic Toolkit) uses hashing as a way to authenticate evidence. This practice has been a core tenet of digital forensics since the late 1990s.
Proper chain of custody procedures ensure that digital evidence remains in its original state, preventing tampering or contamination that could compromise investigations.
Challenges in Maintaining an Unbroken Chain
To maintain an unbroken chain of custody in digital forensics is an important yet difficult endeavor, particularly due to the challenges posed by electronic evidence.
The digital forensics investigation process requires a clear understanding of custody cyber security principles to safeguard digital evidence, given its intangibility and mutability across various platforms.
Remote Data Acquisition Issues
Remote data acquisition is now more feasible than ever with cloud services, mobile devices, and IoT systems readily available as they help extend the reach of research.
Collecting this data remotely creates new challenges. There are numerous challenges that stem from the complexity and scope of data required, including guaranteeing a full set of data.
Smartphone data, cloud platform data, IoT sensor data—they don’t always come neatly packaged with a bow on top.
Dates and details will be updated or moved before they can be documented. Tampering risks are further increased in remote operating conditions. Digital artifacts, like log files, can be created, deleted, or altered, often without any indication, creating doubt on the authenticity of the evidence.
With them, detailed metadata can be captured including timestamps, IP addresses, and URLs.
Perhaps the most significant operational consideration in using these tools is taking steps to maintain evidentiary value and traceability.
Distributed Data Environments
With digital data now often held across various jurisdictions and third-party platforms, this web complicates an already complex tapestry.
Indeed, cloud storage providers might operate under entirely different legal frameworks, adding another layer of complexity to access and admissibility.
In such highly distributed environments, maintaining an unbroken chain of documentation for all data transfers is extremely important.
The National Institute of Standards and Technology (NIST) strongly recommends providing explanations for every transfer in an unbroken chain.
Each transfer needs to explain how and why it occurred and in what context.
Without guidelines, evidence could be thrown out during litigation. Establishing protocols for cross-jurisdictional digital evidence handling can stave off these problems and more.
Proving Integrity Over Time
Establishing the chain of integrity of digital evidence over long periods of time relies heavily on proper documentation and security in storage.
Data can degrade or become corrupted, and lack of appropriate documentation can call its legitimacy into question.
The Federal Rules of Evidence make clear that the authentication of evidence is a condition precedent to admissibility.
Implementing digital tools to log every interaction with evidence, including timestamps and user actions, helps establish a credible timeline and ensures long-term integrity.
Addressing Data Encryption
Encryption, a vital tool for protecting today’s data, creates a situation that is very difficult for the forensic investigation.
Securely decrypting sensitive data while upholding rights to privacy and expression is a complicated feat that necessitates both technical skill and legal charge.
Meeting these competing demands will require a partnership of forensic teams and data owners to responsibly decrypt sensitive information.
Incorporating tools developed specifically for these encrypted environments, such as crypto wallets, can help maintain an unbroken chain of custody without sacrificing security.
Key Points to Remember
- The chain of custody is of particular importance in respect to digital forensics. It creates a fool-proof system of tracking and documenting evidence from the start of collection through the court proceedings. Adhering to this process is vital in ensuring the integrity and authenticity of digital evidence.
- A well established chain of custody protects evidence from any potential tampering, contamination, or outside access. It is hugely important, as it underpins the credibility of investigations and the admissibility of evidence in court.
- Digital evidence comes with additional challenges due to its intangible nature. Above all, to maintain a legitimate chain of custody, investigators must adopt specialized tools, techniques, and protocols. Shifting what’s long been done on paper, for example, to accommodate new types of electronic data is essential.
- Thorough documentation is the basis of the chain of custody. Timestamps, signatures, and a digital, chronological log of all evidence transfers provide accountability and transparency in the custodianship of evidence.
- Techniques such as hashing and the use of write-blockers ensure integrity of digital evidence during analysis. These methodical processes prevent fraud by proving data has not been changed and holding up under scrutiny in a court of law.
- Robust secure storage solutions and controlled access measures are necessary to ensure digital evidence is protected from unauthorized access, alteration or destruction. Routine audits and compliance with rigorous chain of custody protocols help ensure the integrity of the chain of custody.
Frequently Asked Questions
What is chain of custody in digital forensics?
In a nutshell, the custody cyber security process is essential for maintaining and documenting physical or electronic evidence.
It ensures evidence integrity by tracking its collection, storage, and transfer, which is crucial for admissibility in court.
Why is the chain of custody important in digital forensics?
Establishing a proper chain of custody is crucial in safeguarding electronic evidence, as it prevents destruction or tampering while maintaining the reliability of the evidence.
Documenting this digital forensics chain at all times is essential for certainty in a court of law, ensuring the authenticity and integrity of the collected evidence.
What are the key principles of chain of custody?
The key principles include evidence identification, proper documentation, and custody cyber security, ensuring secure storage and maintaining an unbroken digital forensics chain from collection to presentation in court.
How can you maintain an unbroken chain of custody?
Implement strict adherence to documentation and evidence storage within the custody cyber security process, ensuring limited access to evidence by appropriate parties only.
Always use timestamps to track and document each transfer or examination of the digital evidence.
What are common mistakes in chain of custody management?
Mistakes such as lack of documentation, improper handling of evidence, inadequate storage security, or allowing unauthorized personnel access can severely compromise the integrity of electronic evidence and undermine the entire custody cyber security process.
What tools are available for managing the chain of custody?
Digital forensics tools, including forensic software and evidence tracking systems, are vital for developing, preserving, and examining evidence while ensuring the integrity of the custody cyber security process.
How does chain of custody vary for different digital sources?
Each digital source, like computers, smartphones, or cloud data, necessitates adherence to custody cyber security principles.
This ensures proper digital evidence collection, storage, and chain of custody documentation, making them admissible in court.

