Whitelist vs Blacklist: How Should You Choose?

On this page:
- Whitelist vs Blacklist: What are they?
- Whitelist vs Blacklist: Comparing Whitelisting and Blacklisting
- Whitelist vs Blacklist: Use Cases and Applications
- Whitelist vs Blacklist: Advanced Techniques and Innovations
- Whitelist vs Blacklist: Implementing Effective Strategies
- Language and Terminology Considerations
- Key Points to Note
Whitelist vs Blacklist: What are they?
Whitelisting is one of the most powerful security protections available, limiting access to only those who have been previously authorized.
This approach is like a pay-to-play exclusive club. Only those on the list are allowed in, which makes public and private digital environments safer.
By utilizing a relevant whitelist, organizations can significantly enhance their security measures.
Making a list of known good entities is the best way to increase security. In this manner, you ensure that only authorized users, devices, or applications can reach your systems.
Examples of whitelisted entities include trusted IP addresses and validated software applications, which are carefully reviewed and screened to obtain access.
Blacklisting provides an opposite approach, preventing access to identified harmful actors but allowing access to everyone else by default.
This approach is similar to a bouncer at a club, looking for and denying entry to patrons who are already on the list of problems.
The term blacklist carries exclusionary connotations that some organizations are now reconsidering.
For example, blacklists might be lists of known malware sources or IP addresses that have been identified as malicious, stopping them from breaking into your systems.
The effective blacklisting use cases often require constant updates to adapt to new threats.

Whitelisting uses a default deny methodology, which states that access is denied unless specifically permitted.
This approach offers a strong layer of security, but can be more burdensome to maintain as new parties need to be added.
Blacklisting takes a default allow approach.
It’s less restrictive but riskier because it only blocks threats they already know about – meaning, it could miss a new threat.
Origins and Historical Context
Tracing the origins of whitelisting and blacklisting in technology shows that these practices have long played roles in security and harm.
Originally, these terms were just the straightforward descriptors for inclusion and exclusion lists.
Today, the terms have different meanings, indicative of changes in cybersecurity policy.
Originally, whitelists referred to physical access lists in which authorized individuals were allowed entry, whereas blacklists were used to prevent undesirable forms of communication.
Yet today, these terms are inextricably linked to digital security.
Despite their practicality, the cultural connotations of “white” as good and “black” as bad have sparked discussions about the need for more inclusive terminology.
Finding modern replacements for these terms would help create a more inclusive and equitable default without sacrificing their utility.
Defining Whitelisting Practices
Creating a whitelist takes time and effort, starting with determining which resources are most vital and require protection.
Next, you’ll create a whitelist of approved applications, for example, or user accounts.
Entities in a whitelist can include everything from email addresses to IP addresses and domains.
Regular updates are essential to keeping any whitelist or blacklist secure, as new threats and trusted connections continue to develop.
Whitelisting is an important technology for protecting sensitive information, preventing unauthorized access to essential systems.
RELATED: Network Authentication Methods You Should Know
Defining Blacklisting Practices
Blacklisting means aggregating information about existing threats, usually pulled from third-party cybersecurity databases and threat intelligence feeds.
These are known bad actor lists, like lists of malicious IPs, domains, and software.
Incorporating blacklists into security technologies provides zero-day protection instantly, stopping threats in their tracks before they have the chance to do any damage.
Regular monitoring and updating of blacklists is a must, as cyber threats are always changing and evolving to bypass protections.
Utilizing smart blacklist tactics hardens your systems’ offense and defense, keeping your systems more secure from threats that have been identified.
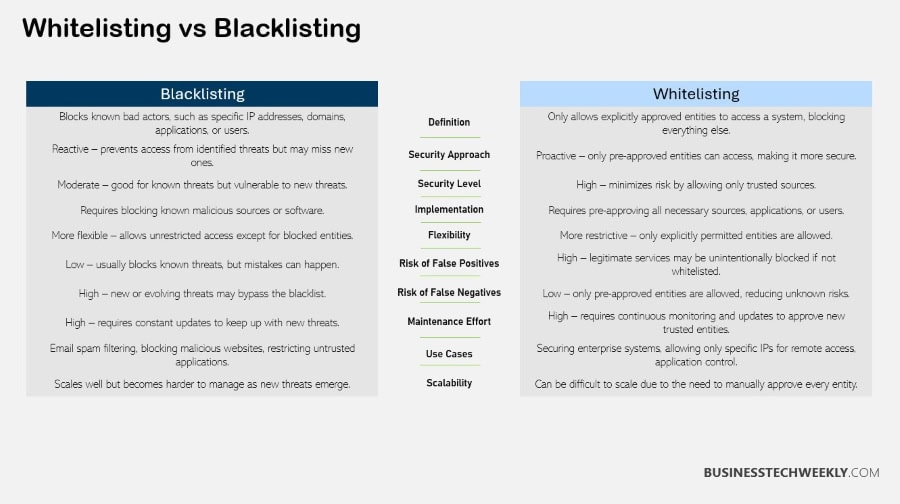
Whitelist vs Blacklist: Comparing Whitelisting and Blacklisting
To grasp the differences between whitelisting and blacklisting, start with the basic premise each approach operates from in cybersecurity.
Whitelisting is based on the premise of default denial.
This implies that only whitelisted entities are granted access, increasing security by reducing the risk of improper users obtaining access.
In contrast, blacklisting is about default block, allowing access to the majority of entities by default unless you have flagged them as dangerous.
This approach is preferred for its user-friendliness and adaptability, providing users with greater freedom while preventing established threats.
However, it can unintentionally allow for new threats to get through.
1. Differences in Purpose and Use
Whitelisting takes the approach of blocking all applications by default until they can be verified as safe.
This method is ideal for high-security environments such as financial institutions.
Blacklisting tends to be more common in environments where user mobility is a key concern, such as corporate networks.
Each method targets different audiences: whitelisting appeals to highly secure environments, while blacklisting suits more dynamic and user-driven contexts.
Which one is chosen makes a significant difference to the enterprise security posture, trading off strict control against operational agility.
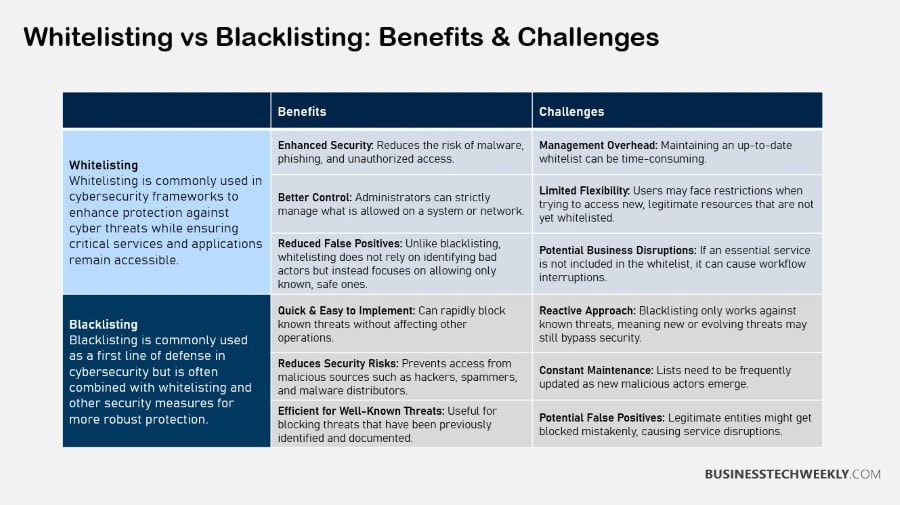
2. Advantages of Whitelisting
Whitelisting increases security overall by preventing any unknown threats by default.
It makes management easier in that you only need to maintain a list of trusted entities.
It mitigates risks of unauthorized access and is dependent on the trustworthiness of whitelisted entities.
When done correctly, this strategy can superbly prevent new, unknown threats from getting into systems, providing a powerful second line of defense.
3. Advantages of Blacklisting
Blacklisting is very simple to deploy, quickly responding to established threats and keeping pace with new ones.
At the same time, it gives users much more flexibility and productivity, reducing the negative impacts on legitimate activity.
By quickly integrating new threats, blacklisting provides a responsive approach to security challenges, maintaining user experience while keeping networks secure.
RELATED: Cyber Attack Vectors: Understanding Attack Vector Types & How to Defend against them
4. Disadvantages of Whitelisting
This is where the problem with implementing whitelisting across every system in government comes in—whitelisting is very inflexible and requires frequent updates.
Restricted access can harm user productivity, and even well-known, trusted entities can be a threat if compromised or coerced.
This approach requires constant diligence to keep it working and in tune with the times.
5. Disadvantages of Blacklisting
Blacklisting by its very nature cannot prevent access to new threats, leaving users exposed to serious security risks.
It depends on ongoing updates to keep working, playing catch-up with zero-day threats.
This is compounded by the lack of proactive filtering, which undermines its efficacy, requiring additional, complementary solutions to effectively address new and evolving security threats.
Inclusive Alternatives to Consider
- Allowlisting
- Denylisting
- Permitting
- Blocking
Moving towards more inclusive language in cybersecurity, such as replacing terms like ‘blacklist’ and ‘whitelist’ with alternatives, is an important step.
This minimizes confusion, combats exclusionary connotations, and encourages clear communication across diverse audiences.
Whitelist vs Blacklist: Use Cases and Applications
Approved and Blocked Lists in Practice
In many circumstances, whitelisting and blacklisting are essential.
For example, application whitelisting is key to defending special-purpose systems such as ATMs, kiosks, and POS systems.
These devices are completely restricted, allowing only specific functions while including robust security features.
Their default-deny approach prevents any unapproved software from running and guards systems against zero-day attacks.
At the same time, application blacklisting is still a crux of enterprise security, stopping known threats and malicious programs dead in their track.
The AV-TEST Institute catalogs more than 350,000 newly created malware and unwanted apps daily.
This latest activity highlights the need for a robust blacklist now more than ever.
Automated systems keep these lists up to date automatically, but routine audits are key to ensure they are accurate and providing security efficacy.
|
Category |
Examples |
|---|---|
|
Whitelisted |
Approved IPs, Trusted Applications, Authorized Users |
|
Blacklisted |
Malicious IPs, Harmful Websites, Suspicious Emails |
Email Security and Compliance Considerations
In email security, whitelisting and blacklisting are fundamental components.
These techniques are an effective safeguard against phishing and spam, providing confidence and assurance in alignment with industry best practices.
Companies sometimes set up email whitelists to let through only approved senders, and blacklists that prevent receipt from established spam sources.
Greylisting, a related practice, throws up temporary rejections on emails from unfamiliar sources, adding another layer of security.
In this context, protecting emails this way is especially important.
According to the Ponemon Institute, the average loss from a data breach is $3.86 million.
Use Cases for Whitelisting
- Securing financial databases
- Limiting access to sensitive applications
- Protecting against unauthorized access
- Defining clear access requirements
Whitelisting has tremendous value in high-security environments as they define clear parameters for access and effectively block any access that is not explicitly permitted.
This security measure protects applications from potential threats, including zero-day attacks, as ColorTokens Xprotect tool demonstrates.
Use Cases for Blacklisting
- Blocking malicious IP addresses
- Preventing access to harmful websites
- Protecting against known vulnerabilities
- Targeting specific threats
In the rapidly evolving threat landscape seen today, blacklisting provides more flexibility to quickly address and adapt to emerging threats.
This approach is key in protecting against vulnerabilities, helping make security measures more targeted and timely.
Whitelist vs Blacklist: Advanced Techniques and Innovations
Emerging technologies are changing the way you approach whitelisting and blacklisting.
Automation is important here too, by helping to cut down on time and improve the effectiveness of listing strategies.
For instance, automated systems can readily react in real time to emerging threats, providing a proactive layer of security.
At the same time, machine learning is transforming the process of identifying threats, especially for blacklists.
By utilizing patterns and behavioral analytics, machine learning algorithms are able to predict and identify threats more accurately.
This proactive approach is key with the AV-TEST Institute currently recording more than 350,000 new malicious programs every single day.
Exploring Greylisting Techniques
Greylisting is a middle ground between whitelisting and blacklisting, and it works best at stopping spam and unwanted bad traffic.
By automatically denying the initial request from unfamiliar sources and making them try again, greylisting silently removes the bad stuff with no cost.
It’s particularly powerful in applications such as email security, where the costs of false positives are high due to spam.
Knowing how greylisting plays a part can help make it an effective component of your overall security strategy.
RELATED: What is Threat Hunting: Proactively Defending against Cyber Threats
Whitelisting and Blacklisting with AI and ML
AI improves listing processes by automating threat detection and helping to improve listing strategies. Machine learning analyzes vast amounts of data to identify new threats, an important component of increasingly dynamic and adaptive security measures.
These technologies help keep listing strategies one step ahead of developing threats while offering the most effective access control.
Blockchain Applications in Listing Strategies
Blockchain does provide a highly secure infrastructure for developing these types of whitelists and blacklists.
Decentralized lists improve transparency and security, reducing the ability to play fast and loose with who does and doesn’t get listed.
This innovation points to a bigger long-term trend of reinvented cybersecurity approaches, keeping these lists safe and sound from tampering.
Whitelist vs Blacklist: Implementing Effective Strategies
When developing strategies to implement whitelisting or blacklisting, understanding terms like greylist and blocklist can enhance security measures.
Best Practices for Whitelisting
- Keep a current list of approved facilities or services so that new developments in your area are quickly added to the list.
- Be explicit about what constitutes an approved entity to prevent misinterpretation.
- If your organization plans to whitelist, keep detailed records of whitelisting processes to ensure consistency and accountability.
- Solicit user feedback to continuously improve practices, making processes easier and more intuitive.
- Conduct thorough testing to identify potential vulnerabilities before implementation.
Best Practices for Blacklisting
- Plan for regular reviews of blacklists to ensure they remain relevant and effective.
- Use threat intelligence to better identify, prioritize, and integrate high-risk entities.
- Implement automated systems to manage blacklists and streamline processes.
- Clearly communicate blacklisting policies to all stakeholders to ensure understanding and compliance.
Email Practices for Listings
- Validate sender domains and IP addresses to stop phishing in its tracks.
- Replace or supplement lists with filtering tools to keep email audiences engaged.
- Use mutual authentication, such as digital certificates, to protect communications.
- Watch for unusual patterns in email usage.
- Prioritize email security to protect against phishing scams and other threats that can cause a data breach.
Language and Terminology Considerations
Language is a powerful tool that can either promote or erode inclusivity.
The language we use has the ability to establish an inclusive space, or by default, continue to foster bias.
For example, terms like “blacklist” and “whitelist” imply racial associations, connecting the color “black” with negative outcomes and the color “white” with positive outcomes.
That language has in the past shut out people of color from the tech industry.
We challenge organizations to review their language, to make sure it uplifts a variety of viewpoints, and to advocate for an equitable way of doing things.
Allowlist and blocklist in place of whitelist and blacklist:
- Denylist in place of Blacklist
- Use blocklist as a neutral term
Inclusive language helps us create a more equitable place to work.
This tactic draws a wider and deeper talent pool, which is critical when competing for applications and infrastructure.
Issues with Non-Inclusive Language
The reactions to non-inclusive language in cybersecurity only serve to alienate communities and misinform the majority.
Even language we may think is benign can be damaging.
Consider these examples:
- “Blacklist” and “Whitelist” imply racial associations
- “Master” and “Slave” in tech settings
Awareness and sensitivity in language are very important to avoid causing harm without meaning to.
Alternative Terminology Options
- Alternative Terms:
- Allowlist replaces Whitelist
- Denylist replaces Blacklist
Inclusive language improves communication, making writing clearer and more precise, resulting in a greater impact for change.
Embracing alternatives to exclusionary connotations in terminology will make the security industry more diverse and effective.
Key Points to Note
- Whitelisting means allowing only the entities you approve on access. As whitelisting allows only known good, blacklisting prevents known bad. It’s important to understand these approaches in cybersecurity so we can apply the right kinds of security controls to mitigate risks.
- The terms “whitelist” and “blacklist” have historical and cultural connotations. Changing them to “allowlist” and “denylist” is a simple way to be more inclusive while still being clear.
- This method offers enhanced security by blocking unknown threats by default, simplifying management and reducing unauthorized access risks. It needs a constant flow of new entries to stay strong.
- Blacklisting facilitates greater user flexibility and can swiftly adapt to emerging threats. It greatly reduces the amount of disruption for legitimate users, but it needs constant, ongoing updates as new vulnerabilities are found.
- Each method has distinct strengths. Whitelisting works best in high-security environments, and blacklisting works best with known threats. Together, a combined approach provides the greatest protection.
- Using more inclusive language, like “allowlisting” and “denylisting,” matters. It demonstrates a focus on equity and helps to make sure you are communicating clearly and in a culturally appropriate manner.

