What is Advanced Threat Protection (ATP)?

On this page:
- What is Advanced Threat Protection?
- Understanding Advanced Threats
- How ATP Works: A Multi-Layered Approach
- Essential ATP Tools and Technologies
- ATP Vendor Comparison Table
- Implementing Effective ATP: Best Practices
- Monitoring and Responding to Threats
- Measuring ATP Effectiveness
- Integrating ATP into Existing Infrastructure
- Key Points to Remember
What is Advanced Threat Protection?
Advanced Threat Protection (ATP) is an enterprise-grade cybersecurity solution.
These features are designed to help you counter the more complex threats that aim for your organization today. It protects important information from complex attacks.
These threats range from malware to phishing to ransomware and other nefarious methods used to exfiltrate, corrupt, or steal data.
By leveraging modern technologies, ATP equips businesses with the tools to anticipate, detect, and neutralize threats efficiently. This ensures their defenses remain robust against evolving cybercriminal strategies.
1. Define Advanced Threat Protection (ATP)
ATP refers to a comprehensive set of security technologies aimed at detecting and stopping advanced threats that bypass conventional protections.
Unlike these legacy solutions, ATP takes a modern approach using advanced technologies like behavioral analysis, machine learning, sandboxing, and threat intelligence.
These tools predict where attacks are most likely to come from, allowing organizations to shift their defenses before the attack occurs.
When businesses adopt ATP, they have the security advantage needed to keep crucial systems and data safer from evolving threats.
2. Contrast ATP with Traditional Security
Most legacy security solutions, like simple antivirus, are reactive by nature, focused on responding to events after they’ve happened.
ATP, on the other hand, focuses on the future, real-time detection and intelligence, always scanning to indicate any anomalies, risks, and weaknesses.
Legacy systems often miss the most stealthy and sophisticated malware.
ATP solutions, on the other hand, use sandboxing and machine learning to preemptively identify and stop these threats. ATP applies multiple detection methods, including signature-based detection and behavioral detection.
These approaches seamlessly blend to cover the shortcomings of traditional approaches and deliver complete protection against complex attacks.
3. Why is ATP Necessary?
The landscape of cyber threats has changed dramatically, as more than two-thirds of all data breaches are due to mistakes made by people.
As businesses continue to grow their digital presence, the vulnerabilities quickly stack up.
ATP meets these challenges with powerful analytics and always-on monitoring to help you quickly find, fix, and stop advanced ransomware and threats.
Without ATP, organizations face heightened risks of data breaches, financial loss, and reputational damage.
This makes its adoption a necessity in modern cybersecurity strategies.
4. Core Goals of Advanced Threat Protection
The ultimate goal of ATP is to protect against bad actors from gaining access to confidential data.
It does so by identifying malicious activities in their initial stages and responding with swift and targeted action, thus mitigating the impact.
By preventing unauthorized access and data breaches, ATP solutions assist organizations in adhering to data protection regulations.
This keeps them aligned with industry standards and protects their business.
5. Key Benefits of Advanced Threat Protection
Advanced threat protection solutions enhance threat detection rates, striving for at least 90% accuracy in identifying and neutralizing known threats.
By automating analysis, these solutions minimize response times, enabling organizations to swiftly address potential attacks before they escalate.
Combining signature and behavior-based detection with machine learning, ATP cybersecurity effectively delivers comprehensive protection against various attack vectors, from email phishing to advanced malware, thereby strengthening a company’s overall security posture.
Understanding Advanced Threats
Advanced threats are a major danger to today’s enterprises. With their advanced techniques, they are able to slip past the most well-equipped security defenses.
Unlike these so-called low-level threats, advanced threats are very much focused and agile. They adapt just to beat countermeasures and stick around in systems, waiting and wanting.
Knowing what they are is key to crafting smart security frameworks that meet their complexity and keep their risks at bay.
Defining Advanced Threats
Advanced threats are anything from targeted malware or very sophisticated attacks that exploit gaps in your setup and seek to steal valuable information or cripple your systems.
Threat actors—like cybercriminal groups and nation-state hackers—often deploy advanced methods to evade detection.
They depend on tactics such as social engineering and zero-day exploits to achieve their objectives.
These threats take a heavy toll on organizations, costing millions and undermining reputations. Regrettably, this reality underscores the stark need for effective risk management procedures to be in place.
Characteristics of Advanced Threats
The key characteristics of these advanced threats are their stealth, persistence and ability to adapt.
These threats are able to exploit unknown vulnerabilities, frequently referred to as zero-days, to gain entry into systems unnoticed.
They never stop changing, moving forward to find new strategies to stay ahead of security protection.
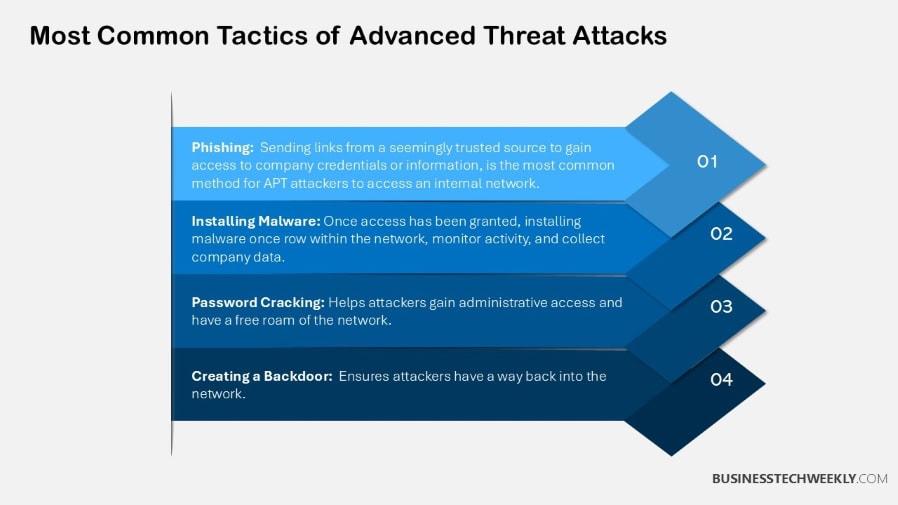
A ransomware attack typically begins with phishing emails. After that, it digs much deeper into the network to spread its negative impact as widely as possible.
Common Types of Advanced Threats
- Encrypts files, demanding payment for decryption. Mitigating their effects Regular backups and thorough incident response plans are indispensable.
- Manipulative emails that trick users into revealing credentials. With almost 90% of organizations experiencing this attack type, educating yourself and raising awareness is more important now than ever.
- Prolonged attacks targeting confidential data, often using zero-day exploits and social engineering techniques.
- Risks from employees or contractors driven by motivations like financial gain. Monitoring and access controls are crucial to mitigation.
- Intercepting communications to steal data. Encryption and secure protocols play important roles as integrated ongoing defenses.
- Targets vulnerabilities to create system downtime. DDoS mitigation strategies are available to help keep your services online and available.
- Putting companies on notice by exploiting flaws before they’ve had a chance to fix them. Threat intelligence is an important tool for building awareness and combating these dangers.
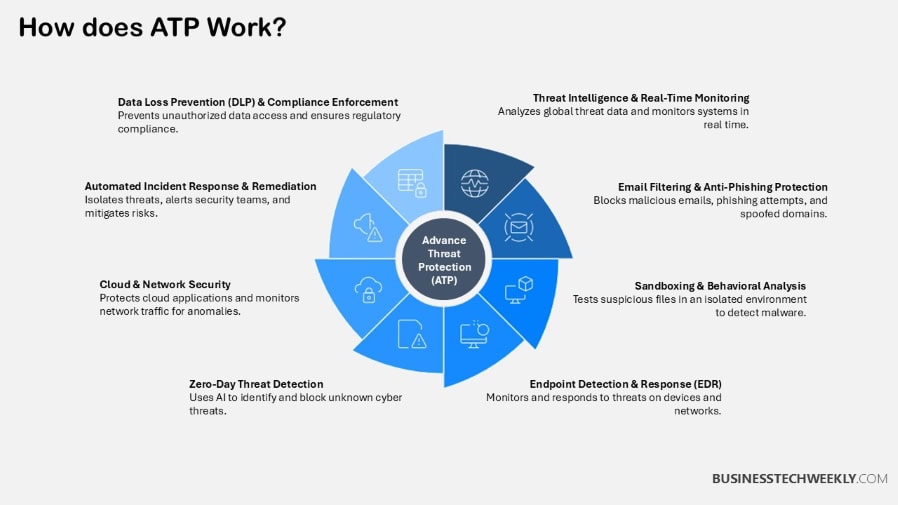
How ATP Works: A Multi-Layered Approach
ATP takes a systematic, multi-layered approach to protect organizations from advanced threats.
Through the strategic integration of multiple technologies and techniques ATP provides 360º security coverage, detecting and preventing potential threats. This multi-layered approach conveniently integrates with your legacy systems of security.
It enhances SIEM systems, IAM frameworks and vulnerability scanners to increase their overall resilience.
Behavioral Analysis Techniques
Behavioral analysis is another key technique for spotting anomalies in patterns of activity to users or systems.
By identifying anomalies from proven baselines, such methods can alert to potential intrusions and incidents before they happen. For instance, if a user suddenly accesses large volumes of sensitive files outside of regular working hours, it may signal a breach attempt.
At the heart of this process is machine learning.
It never stops learning from data, improving the behavioral analysis accuracy and significantly lowering the number of false positives to 5% or less. This reduces the opportunities for dislocation while continuing to hold strong defenses.
Machine Learning in Threat Detection
Machine learning algorithms are particularly good at sifting through massive data sets to identify patterns that can help reveal potential threats.
This ability allows ATP solutions to identify suspicious activity in real-time, like a massive influx of bogus traffic or a pattern of multiple failed logins.
Ongoing training allows these systems to adjust to threat behaviors that constantly change and adapt.
As such, they serve to neutralize zero-day exploits and advanced persistent threats.
Sandboxing Explained
Sandboxing is the practice of isolating suspicious files in a controlled environment, analyzing their behavior evaluated without risking the organization’s bigger network.
For instance, a suspicious email attachment that could be harmful is executed within the sandbox to see what it does.
This technique is key in spotting ransomware, which can stay inactive for a while before being set off.
Sandboxing is the most effective way to identify threats that static antivirus engines fail to catch.
Endpoint Detection and Response (EDR)
EDR is primarily about monitoring and responding to endpoint threats in place.
Through 24/7 monitoring and visibility into activities on the endpoint, EDR detects malicious behavior—like the unexpected modification of files—before they escalate into a breach.
It automates threat response – quarantining infected devices, for instance – serving to speed up remediation efforts and downtime.
Threat Intelligence Utilization
Threat intelligence informs and offers actionable insights related to emerging vulnerabilities and attack vectors.
Working with threat intelligence feeds, ATP solutions are able to constantly update IOCs and IOAs, which means defenses are consistently on the lookout for the latest threats.
Platforms that aggregate this data allow organizations to proactively identify and mitigate risks before they become a problem.
Cloud Security Integration
Building security measures into cloud environments helps tackle challenges such as data privacy and compliance.
ATP solutions prevent cloud-based applications from being misconfigured and provide attack detection capabilities.
They guard against bad actors, delivering robust security for cloud-native operations.
Email Security Measures
It’s no surprise that email is still one of the biggest attack vectors.
Strong filtering systems filter out threats such as phishing and malware attachments, and validators help stop domain spoofing.
These measures are good common sense. They protect sensitive communications and they reduce the likelihood of a data breach.
Identity and Access Management (IAM) Role
IAM frameworks protect the resources behind an access gate that IAM frameworks hold by managing user identities.
IAM protects against unauthorized activities and helps reduce insider threats by enforcing security policies and restricting access rights.
For instance, role-based access restricts employees to viewing only data that is necessary for their work duties.
Essential ATP Tools and Technologies
Advanced Threat Protection (ATP) solutions merge several technologies to protect your systems from advanced, evasive cyber attacks.
These solutions work through continuous monitoring, advanced analytics, and technologies like machine learning, behavioral analysis, and sandboxing to detect, analyze, and neutralize potential risks.
Make sure these tools are a part of your overall IT environment.
Doing so equips you to address both today’s and tomorrow’s threats with greater accuracy and speed. Here’s a look at the key elements that distinguish strong ATP frameworks.
Next-Generation Firewalls (NGFWs)
NGFWs take conventional firewalls a step further by using other sophisticated capabilities such as threat intelligence, application awareness, and deep packet inspection to identify and minimize evasive and sophisticated attacks.
Unlike traditional firewalls, NGFWs have the ability to detect and mitigate threats by inspecting more than just IP addresses and ports.
For instance, they’re able to identify malware hidden in encrypted traffic.
These next-gen firewalls use contextual awareness and intelligence to judge threats. These are invaluable tools in today’s complex and dangerous attacks.
For organizations that have increasingly adopted the workplace cloud, NGFWs play an essential role in delivering this multi-layered protection while not sacrificing network performance.
Intrusion Detection/Prevention Systems (IDPS)
IDPS serves to monitor network or system traffic for malicious activity.
Intrusion Detection Systems (IDS) detect and identify possible threats or attacks. At the same time, Intrusion Prevention Systems (IPS) act to prevent such threats in real time as they emerge.
One IPS can block a Distributed Denial of Service (DDoS) attack the moment it arrives, preventing the DDoS from impacting your business operations.
By minimizing the rate of false positives—under 1% in a properly tuned system—IDPS makes possible the rapid response to real threats.
Security Information and Event Management (SIEM)
SIEM solutions collect and correlate security information from various sources, offering centralized and real-time visibility into potential threats.
Using the power of advanced analytics and machine learning, SIEM finds and reports patterns that suggest the presence of a breach.
For example, it can prevent anomalous login attempts from anywhere on your network.
SIEM’s compliance reporting capabilities ensure all security incidents are documented, allowing you to maintain compliance with various regulatory requirements.
Threat Intelligence Platforms (TIPs)
TIPs gather and analyze data on new and developing threats, allowing the community to take a proactive approach to security.
These platforms improve situational awareness by putting complex geopolitically relevant data together from multiple global threat feeds.
For instance, TIPs can notify your operations team of an emerging ransomware campaign against organizations in your sector.
When TIPs are integrated into your security operations, you can proactively anticipate and neutralize threats before they cause damage.
Endpoint Detection and Response (EDR) Solutions
Second, EDR solutions in general are about detection and response to threats that are actively going after open endpoints such as laptops and mobile devices.
Through behavioral analytics, they track suspicious behavior like atypical access to confidential files.
This is especially true for automated response features, like quarantining infected devices, where threats are contained in seconds.
Especially for organizations supporting hybrid workforces, EDR has become an essential layer of protection against endpoint vulnerability exploitation.
ATP solutions provide organizations with real-time visibility into network traffic and potential threats. This panoramic insight enables accurate threat identification, reducing false positives and allowing security teams to focus on genuine threats.
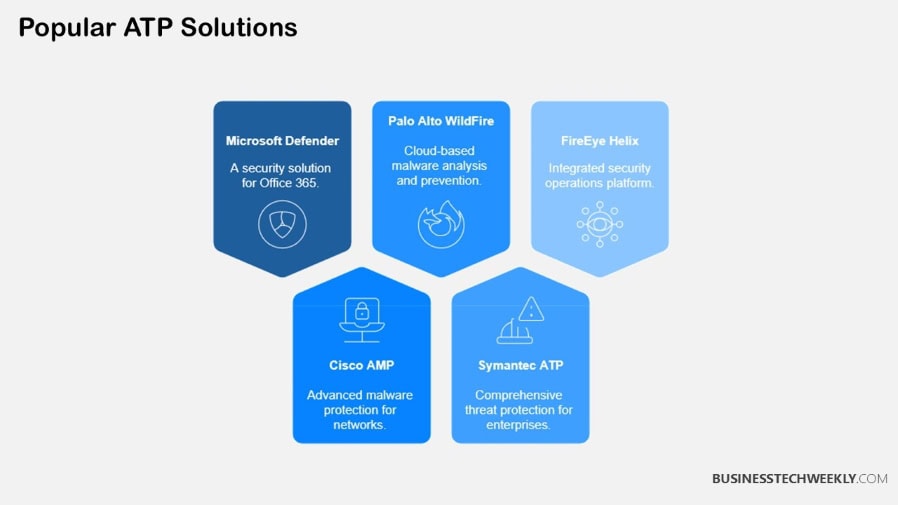
ATP Vendor Comparison Table
Here’s a comparison of top Advanced Threat Protection (ATP) solutions from leading vendors.
Feature |
Microsoft Defender ATP |
Cisco AMP (Advanced Malware Protection) |
Palo Alto Networks WildFire |
Symantec ATP |
FireEye Helix |
| Threat Intelligence | Microsoft Threat Intelligence | Cisco Talos Intelligence | Palo Alto Unit 42 | Broadcom/Symantec Threat Intel | FireEye Threat Intelligence |
| Email Security | Office 365 ATP integration | Cisco Secure Email | Phishing protection | Email ATP features | Advanced email security |
| Sandboxing | Deep file & URL analysis | File detonation in AMP Threat Grid | Inline & cloud-based sandboxing | Cloud sandboxing | Network & endpoint sandboxing |
| Endpoint Detection (EDR) | Defender for Endpoint | Cisco Secure Endpoint | Cortex XDR integration | Symantec EDR | Helix XDR |
| Zero-Day Threat Protection | AI & heuristic-based detection | Machine learning-based detection | Behavioral & signature analysis | Threat isolation & analysis | AI-powered detection |
| Cloud & Network Security | Microsoft 365 & Azure integration | SecureX cloud integration | Prisma Cloud support | Web & network ATP | Cloud-native security |
| Automated Threat Response | Auto-remediation & attack isolation | Automated playbooks | Automatic containment | Endpoint isolation & rollback | AI-driven threat response |
| Compliance & DLP | GDPR, HIPAA, PCI DSS support | DLP & compliance features | Security policy enforcement | DLP integration | Compliance monitoring |
Choosing the Right ATP Solution
Best for Microsoft 365 Users: Microsoft Defender ATP
- Seamlessly integrates with Microsoft 365 and Azure security tools.
- Provides deep email security, endpoint detection, and automated remediation.
- Leverages Microsoft’s vast threat intelligence network for proactive defense.
- Ideal for organizations already using Microsoft’s ecosystem.
Best for Enterprise Networks: Cisco AMP (Advanced Malware Protection)
- Strong network security with SecureX platform integration.
- Uses Cisco Talos Intelligence for global threat detection.
- Advanced email security and sandboxing for deep malware analysis.
- Suitable for large enterprises with complex IT infrastructures.
Best for Advanced Firewall Security: Palo Alto Networks WildFire
- Integrated with Palo Alto’s Next-Generation Firewalls (NGFW) for real-time protection.
- AI-driven threat detection and automated incident response.
- Cloud-based and on-premises sandboxing for malware analysis.
- Best for organizations requiring high-end perimeter security.
Best for Endpoint Security: Symantec ATP
- Comprehensive endpoint protection with deep forensic analysis.
- Strong threat isolation and rollback capabilities.
- Cloud-based and on-premises deployment options.
- A solid choice for businesses prioritizing endpoint security and compliance.
Best for Threat Intelligence & Incident Response: FireEye Helix
- Industry-leading threat intelligence from FireEye Mandiant.
- AI-driven detection and response to advanced persistent threats (APTs).
- Offers real-time visibility and automated security operations.
- Best suited for organizations needing proactive threat hunting and response.
Ransomware accounted for nearly 25% of all cyber incidents, with some larger organizations paying up to $75 million in ransom. This underscores the critical need for robust ATP solutions to combat sophisticated ransomware attacks.
Implementing Effective ATP: Best Practices
Advanced Threat Protection (ATP) is critical to protecting your organization from today’s sophisticated cybersecurity threats and targeted cyberattacks.
Implementing comprehensive advanced threat protection solutions effectively takes a systematic approach that meets your specific needs while still integrating with existing security solutions.
Here are best practices to help you maximize ATP’s potential.
Assess Security Requirements
Assessing security requirements begins with understanding your organization’s specific vulnerabilities and risk exposure.
This involves evaluating current security measures, organizational goals, and how much risk your business can tolerate.
Security assessments help pinpoint gaps, such as insufficient endpoint security or outdated protocols, ensuring the ATP solution directly addresses these weaknesses.
For example, if your business handles sensitive customer data, encryption and data loss prevention (DLP) should be prioritized.
Identify System Weaknesses
Recognizing system vulnerabilities allows you to prioritize improvements. Common oversights include misconfigured firewalls, unpatched software, and weak access controls.
Vulnerability assessments, often leveraging tools like penetration testing, reveal hidden risks such as backdoors in applications.
By identifying these issues, you can reinforce weak points before integrating ATP.
Evaluate Existing Infrastructure
Taking stock of your existing infrastructure will help you with smooth ATP integration.
Knowing how other tools, such as firewalls, SIEMs, antivirus solutions, will play with ATP is key.
Compatibility concerns, if overlooked, can result in operational inefficiencies or even system failures.
For example, combining ATP’s machine learning-based analytics with your network monitoring tools helps you identify threats in real-time and without delay.
Define Clear Security Objectives
By understanding what you are trying to accomplish, you can track the success of ATP.
Objectives such as reducing detection time to less than 15 minutes or reaching a 90% incident response effectiveness set clear, quantifiable standards.
Aligning these goals with business priorities, like protecting their intellectual property, keeps ATP implementation nimble while making the effort more meaningful.
Select the Right ATP Solution
Selecting an ATP solution means weighing features for scalability, ease of use and advanced features such as behavioral analysis or sandboxing.
Solutions that have false-positive rates on the order of 1-5% with maximal threat coverage are optimal.
Prototyping solutions in a controlled environment allows you to determine their effectiveness before risking disruption to your operations.
Develop Security Policies
Smart policies formalize how ATP is deployed and monitored.
Homegrown comprehensive policies help define incident response procedures and staff roles, minimizing mistakes and miscommunication during a major security incident.
Consistent and continuous changes to these policies make sure they are directing resources toward the latest emerging threats.
Conduct Staff Training
At the core of most breaches is human error.
Training staff to identify the signs of phishing emails or how to use ATP tools properly drastically reduces the chances.
Regular, ongoing training ensures that your team is always on their toes when faced with new threats while establishing a security-minded workplace culture.
Monitor and Review System Performance
Regularly reviewing ATP performance through metrics like time to detection and response or incident response effectiveness ensures the system adapts to new threats.
By continuously monitoring attack patterns with cutting-edge analytics, agencies can continuously improve configurations to provide maximum protection.
Address Compliance Mandates
Ensuring you meet compliance requirements like HIPAA or GDPR is made easier thanks to advanced threat protection solutions.
With ATP’s regular audit process and strong data protection features, you can confidently address potential security incidents.
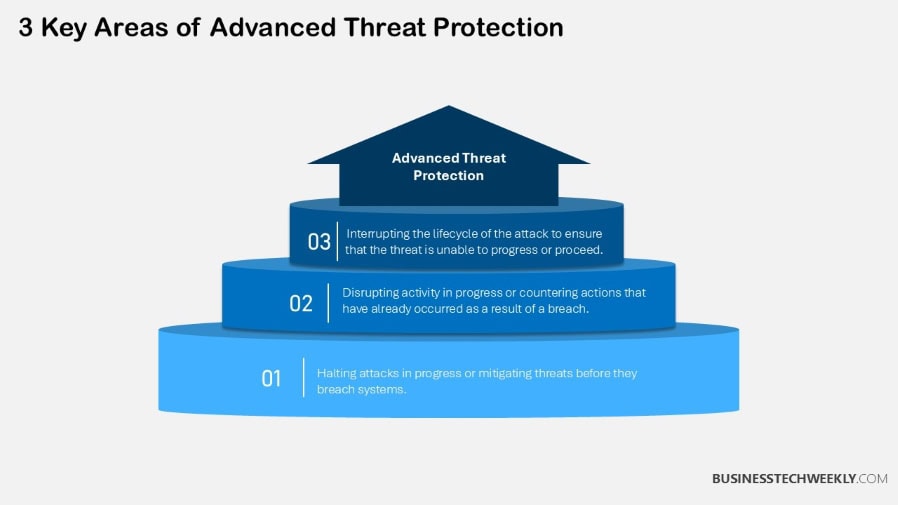
Monitoring and Responding to Threats
Monitoring and responding to threats are at the heart of Advanced Threat Protection (ATP).
This strategy emphasizes continuous monitoring and rapid response to protect your organization from changing cyber threats.
Combine ATP proactive monitoring with a well-defined response strategy, and you have a powerful combination that goes beyond reducing and helping eliminate costly, reputational risk disruptions.
Create an Incident Response Plan
An incident response plan is a course of action that’s documented, distinct, and designed to manage security incidents.
It provides clear guidance on actions needed to detect, prevent and respond to threats.
Such an arrangement enables your organization to provide a swift response in the event of a breach.
By taking swift action, you’ll reduce the likely impact to your systems, reputation, and capabilities.
From having clear incident response protocols—including for isolating impacted systems to avoid the spread of ransomware—entities can immediately respond quickly when needed.
Ongoing development, review, and testing of your plan is key to making sure your plan stays up to date and effective as threats change.
This may include red team testing to find your vulnerabilities and sharpen your response playbook.
Perform Proactive Threat Hunting
Proactive threat hunting means to actively look for threats that may already be lurking around your network.
Unlike traditional detection approaches that react to alerts, threat hunting proactively spots anomalies that automated systems can overlook.
This process is highly complex and intensive, requiring the expertise of highly qualified security analysts who implement behavioral analysis, threat intelligence, and more.
For example, by identifying suspicious login behavior, cybersecurity analysts can identify possible hacks before they become major incidents.
Proactive threat hunting has the added benefit of honing your detection capabilities. It reduces the false-positive rate, allowing your team to focus on real threats.
Use Security Orchestration, Automation, and Response (SOAR)
SOAR solutions help teams automate security operations and respond to incidents more quickly and efficiently.
These tools can easily plug into current systems, including intrusion detection and prevention systems (IDPSs) and security information and event management (SIEM) platforms.
Combined, they provide a coordinated front against threats we face.
By automating repetitive duties, SOAR contributes to lowering response times while incident response effectiveness significantly.
For instance, if a phishing attempt is detected, SOAR can automatically quarantine the impacted account and alert your security team.
SOAR’s flexibility makes it right even as new threats emerge, providing protection that’s always scalable, agile, and cost effective.
The global Advanced Threat Protection (ATP) market generated revenues of approximately USD 6.79 billion in 2023 and is projected to reach USD 24.51 billion by 2030, reflecting a Compound Annual Growth Rate (CAGR) of 20.2% from 2024 to 2030.
Measuring ATP Effectiveness
To ensure your organization is adequately protected against advanced cyber threats, measuring the effectiveness of Advanced Threat Protection (ATP) solutions is critical.
This includes measuring the level of your ATP solution against achieving your security objectives, reducing risk, and advancing your operational priorities.
Given how few (only 12%) organizations don’t even know what their ATP is doing, finding ways to measure accuracy becomes the order of the day.
Continuous monitoring and data analysis prove that the system is working. They help you understand specific areas to improve, so your security measures can stay proactive and efficient.
Key Performance Indicators (KPIs) for ATP
KPIs for ATP are specific, measurable, attainable, relevant, and time-bound values that indicate how successful your security initiatives are.
These measures give you a tangible, straightforward understanding of how your ATP solution is performing and what it is accomplishing.
These key performance indicators (KPIs) are detection rate, incident response time, and detection sum of threats.
This higher detection rate is a reflection of the solution’s ability to identify such highly evasive, advanced threats. A shorter time to detection and response underscores its maturity in reducing the damage caused by attacks.
So of course, aligning any KPIs that you choose to adopt with your specific organization’s security objectives is critical.
If your main goal is avoiding disruption, for instance, you’d want to measure things like the false-positive rate.
The greater the false alert rate, the more false positives your security team must investigate, leading to wasted effort and costly interruptions.
By consistently tracking these metrics, you guarantee that your ATP solution is continually and directly tied to your priority operational goals.
KPI Category |
KPI Metric |
Description |
| Threat Detection | Malware Detection Rate | Percentage of detected malware from total incoming threats. |
| Phishing Email Detection Rate | Percentage of phishing emails detected and blocked. | |
| Advanced Persistent Threat (APT) Identification | Number of identified and mitigated APTs. | |
| Zero-Day Threat Detection | Number of zero-day threats detected before exploitation. | |
| Threat Prevention | Blocked Malicious Emails | Count of malicious emails prevented from reaching users. |
| Endpoint Protection Success Rate | Percentage of endpoints protected against cyber threats. | |
| Web Threat Protection Effectiveness | Number of malicious URLs blocked vs. total accessed. | |
| Incident Response | Mean Time to Detect (MTTD) | Average time to detect a security threat. |
| Mean Time to Respond (MTTR) | Average time to respond and mitigate a detected threat. | |
| Incident Resolution Rate | Percentage of security incidents successfully resolved. | |
| False Positive Rate | Percentage of false alarms in threat detection. | |
| User Protection | User Awareness Training Completion | Percentage of users completing security training. |
| Phishing Simulation Click Rate | Percentage of employees clicking on simulated phishing links. | |
| System Performance | ATP System Uptime | Percentage of time ATP solution is available and functional. |
| Latency in Threat Analysis | Time taken to analyze and classify potential threats. | |
| Compliance & Reporting | Regulatory Compliance Adherence | Percentage of compliance with security regulations (e.g., GDPR, HIPAA). |
| Security Audit Score | Score based on periodic security audits. | |
| Threat Intelligence | Threat Intelligence Utilization | Number of new threats identified through threat intelligence. |
| Threat Feed Integration Rate | Percentage of threat feeds successfully integrated into ATP. |
Strategies for Evaluating ATP Solutions
Evaluating ATP solutions involves structured strategies such as pilot testing and vendor assessments.
Pilot tests simulate real-world scenarios to measure how effectively the system responds to threats.
Vendor assessments allow you to compare features, costs, and scalability.
Involving security teams and stakeholders during evaluations provides practical feedback, ensuring the chosen solution meets both technical and business requirements.
Thorough documentation of evaluation processes and outcomes ensures transparency and helps refine future assessments.
Reducing False Positives
Anti-surveillance systems are at risk of false positives, which happen when a system flags non-threatening activities as possible threats.
Such errors can lead to operational disruption and cost security teams significantly in unnecessary complexity and overload.
Preventing them requires improving detection algorithms and employing more sophisticated threat intelligence.
Reducing the false-positive rate lowers the burden on security teams and allows for a greater focus on finding genuine threats.
A recent survey revealed that 95% of organizations are utilizing Artificial Intelligence (AI) to bolster their cybersecurity measures. Key applications include threat detection and real-time monitoring (46%), endpoint protection (46%), and behavioral or sentiment insider threat analysis (43%).
Integrating ATP into Existing Infrastructure
Integrating Advanced Threat Protection (ATP) into your current security infrastructure is an important part of reinforcing your organization’s security posture.
ATP solutions offer highly sophisticated features, including real-time threat detection and response.
Beyond comprehensive visibility across your network, they integrate seamlessly with your current security infrastructure.
Yet to make this change as smooth and successful as possible, thoughtful planning and implementation will be key.
Scalability Considerations
Scalability is a measure of how well your ATP solution can flex, expand and scale as your organization grows and changes.
Therefore, businesses, and most critically, small and medium-sized businesses (SMBs) require consistent security systems that can adapt to growing workloads, broadening networks, and developing threats.
ATP products are engineered to fit your specific application.
They’re fully interoperable with [insert your favorite ICAP protocols], from Check Point, to FireEye, and scale easily as your needs expand.
The best ATP solutions come with a very low false-positive rate. In this manner, your organization is able to focus on the most pertinent threats and avoid being distracted by irrelevant noise.
Continually evaluate your entity’s risk tolerance and path of expansion.
This will give you a baseline understanding of how well your existing ATP configuration matches your desired outcomes moving forward. This helps you keep your security infrastructure secure and scalable, no matter how quickly your business grows.
Security Integration Strategies
To reap the benefits of ATP most effectively, integration should be strategic and collaborative with existing security infrastructure.
Begin with determining your organization’s risk profile and which assets are most vital to protect first.
This will help you figure out where the ATP solution should work on your infrastructure first. Collaboration among your security teams is key.
Strong cross-departmental communication will help ensure that ATP solutions like Kiteworks, which enable tools like OPSWAT, are implemented in the most comprehensive and beneficial way.
Keep integrating and improving so your organization stays one step ahead of ever-changing threats.
Security vulnerabilities have exploded, with a 180% increase in exploitation over the last year.
Cost-Effective Implementation
Smart ATP implementation protects you from costly false positives without sacrificing strong protection and maximizing your ROI.
Process Go further with less by maximizing your existing resources and prioritizing solutions that fit naturally into your existing workflows and capacities.
Budget optimization doesn’t have to come at the expense of security—it refers instead to choosing flexible solutions that fit your budgetary and operational demands.
Evaluating your security investments on a regular basis are key to making sure they remain cost-effective over the long haul.
Selecting ATP solutions that provide waterfall-style, end-to-end visibility reduces the need for many redundant solutions. It’s the most convenient way to maximize your budgets and save creative time.
Key Points to Remember
Keeping your organization protected against today’s advanced cyber threats requires more than a reactive solution.
With Advanced Threat Protection, you have the insights and intelligence to protect your data and systems from attackers before they strike.
It does so by implementing robust cyber defenses, continuous real-time monitoring, and rapid response to emerging threats.
- Advanced Threat Protection (ATP) is a powerful electronic security option. It does a great job protecting against advanced cyber threats including ransomware, phishing and zero-day exploits. Specifically, it aims to secure governmental sensitive data and to fortify organizational defenses.
- ATP takes a more proactive approach than conventional security. It requires a more proactive approach to detect and mitigate threats, using tools such as behavioral analysis, machine learning, and threat intelligence.
- Advanced threats, known for stealth, persistence, and complexity, can now be described as the new normal for those developing security focused on prevention versus protection. ATP meets these new threats head on with smart, evolving approaches.
- Implementing ATP means making a commitment to best practices. You need to evaluate your security requirements, fill gaps within your systems and leverage technologies such as endpoint detection and response (EDR) and next-generation firewalls (NGFWs).
- Reassess and actively monitor your ATP solutions to keep them effective. Provide thorough staff training and use advanced technologies in accordance with regulatory requirements to avoid contributing to risk.
- Furthermore, technologies like AI, blockchain, and quantum-resistant security solutions will play a major role in the future of ATP. These advancements will enable organizations to be one step ahead of cybercriminal techniques.

