EDR vs Antivirus: What You Need to Know About the Differences

On this page:
What is Antivirus?
Antivirus software acts as a proactive measure that detects and neutralizes active malicious threats like viruses, worms, Trojans and ransomware.
That’s why it’s purpose-built to eliminate such threats from your devices.
Its most important feature is detecting established malware by scanning files and programs, checking them against a log of malware signatures. These signatures wash over your code like a fingerprint, identifying malicious code before it can run rampant. They allow antivirus solutions to quickly and accurately focus on threats.
Frequent updates to these signature databases are critical for the software to be effective, as they need to keep pace with the development of new malware variants.
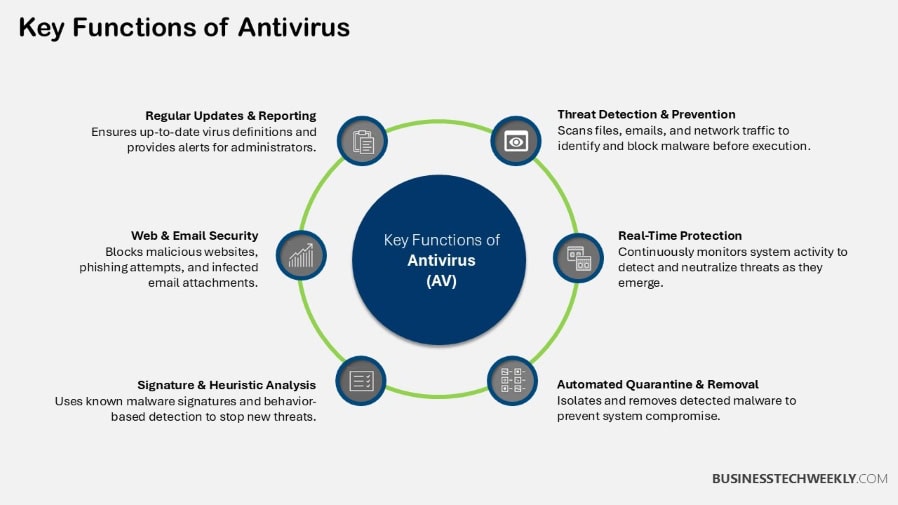
Core Functions of Antivirus
First, antivirus software fills a few key roles when it comes to the protection systems.
With comprehensive static and dynamic analysis, it scans files and programs to detect and remove malware, identifying threats before they even reach your system.
Real-time protection is another near-universal key feature that actively guards your system from falling victim to malware infections before they start.
Scheduled scans add an additional layer of security by ensuring that the device is automatically scanned at specific intervals, providing continuous protection against emerging threats.
Antivirus programs proactively warn people away from dangerous sites or downloads.
This goes a long way towards greatly lowering the risk of accidentally opening up systems to malware.
Antivirus Role in Security
Antivirus can be the first line of defense, blocking known threats and acting as the base layer of security.
It works well when integrated with other solutions, like firewall systems or endpoint detection and response (EDR) tools, for comprehensive protection.
Antivirus software is certainly helpful, but prevention through user education is the first line of defense.
Simple habits, like staying away from unknown links or downloads, may double the antivirus’ effectiveness.
Focusing only on AV for your cybersecurity needs can still expose your systems to more advanced threats.
Limitations of Antivirus Software
For starters, legacy antivirus can’t track what we call zero-day malware — new or unknown strains of malware that make up almost 90% of all variants.
Sophisticated threats, such as advanced persistent threats (APTs) that are commonly used in targeted attacks, frequently bypass signature-based detection.
Performance concerns, like system slowdowns during scans, are consistently cited as a major downside too.
Endpoint Detection and Response (EDR) Explained
Endpoint Detection and Response (EDR) is one of the newest cybersecurity panaceas.
This allows it to more proactively detect and respond to threats that are actively targeting the organization’s endpoints (laptops, desktops, and servers).
Aside from that, EDR is a step beyond antivirus. While legacy solutions simply detect and prevent known malware, EDR provides real-time monitoring and more sophisticated detection capabilities that analyze endpoint behavior.
For example, it can help organizations detect both known threats and new, emerging threats. This is especially effective against fileless attacks and zero-day exploits, resulting in greater overall protection.
More than that, EDR is a key component to improving an organization’s cybersecurity defense.
Using 24/7 monitoring and behavioral AI, it identifies and stops activities that go undetected by traditional antivirus software.
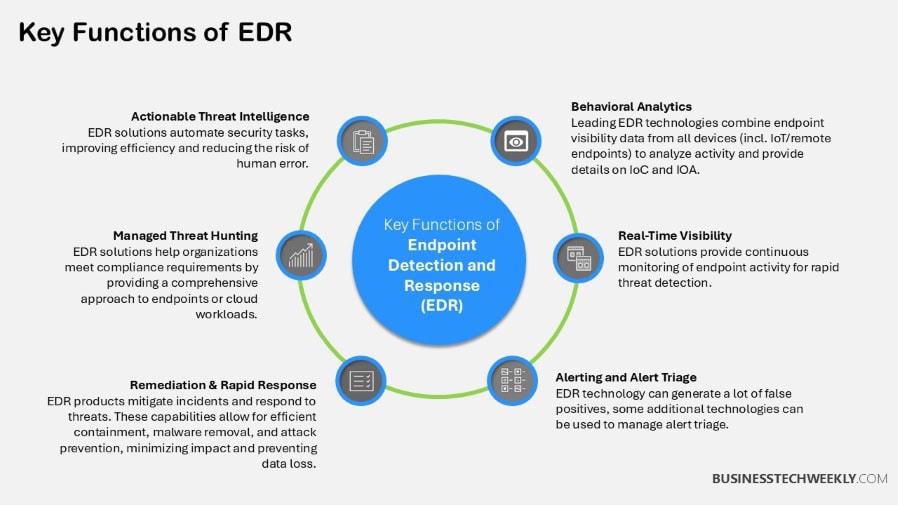
Consider that nearly 80% of data breaches result from either compromised credentials or remote code execution vulnerabilities.
These threats quickly evade traditional signature-based detection approaches. EDR addresses advanced persistent threats (APTs) and other complex attacks by honing in on unusual behaviors.
It doesn’t only look for known threat signatures. This is what makes it such an important part of any modern cybersecurity strategy, especially for organizations that are all chasing down more sophisticated threats.
Unlike traditional detection-focused antivirus solutions, EDR focuses on response. It can automatically isolate compromised systems, quarantine suspicious files and even terminate malicious processes without human intervention.
Its forensic tools give organizations the means to investigate any breach down to the last detail. They look at user behavior, network activity, and system changes to find what started it all.
Integration with existing security tools, such as SIEM systems and firewalls, further strengthens the overall security framework, supporting compliance requirements through detailed reporting.
For the small-to medium-sized business, EDR delivers solutions at scale and on a budget, solutions that meet growing resource constraints.
These automated features minimize the need for human intervention, a key benefit considering the continued cybersecurity talent shortage.
EDR helps organizations leverage more powerful capabilities, such as threat hunting or machine learning-based prevention.
This helps them respond faster and reduce the business impact of incidents, delivering comprehensive, advanced protection against the threats of today and tomorrow.
Approximately 68% of organizations have experienced at least one endpoint attack that compromised their data or IT infrastructure.
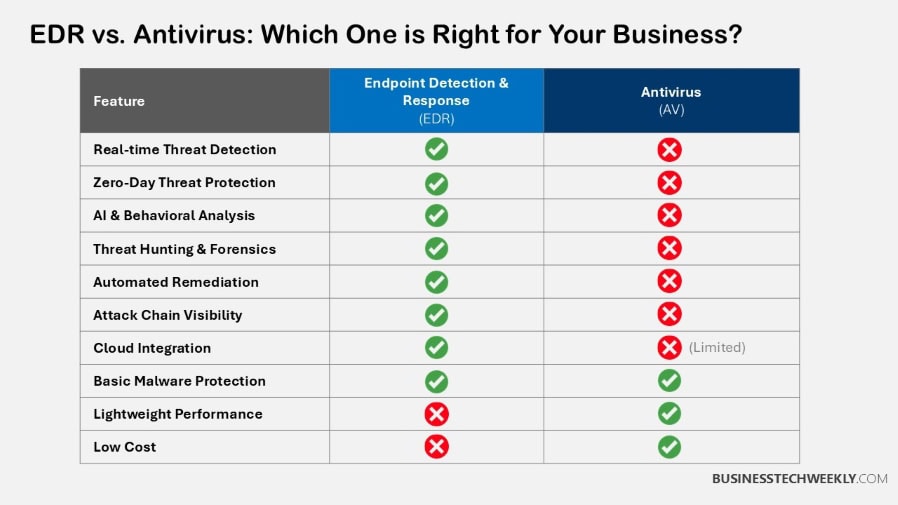
EDR vs Antivirus: Key Differences
As cyber attacks continue to become more advanced and complex, organizations of all sizes need to reassess the state of their endpoint security programs.
EDR (Endpoint Detection and Response) and traditional antivirus are two very different IT security solutions that providers rely on to protect their environments.
Antivirus software is designed to remove threats you already know about. EDR provides comprehensive capabilities to detect and respond to both known and new threats.
Detection Focus Comparison
Antivirus often still works mostly on signature-based detection, where it uses previously known malware patterns to identify threats.
This approach is powerful against known dangers. However, it has failed miserably to stay on top of the increasing onslaught of emergent malware, with over 450,000 new types detected daily.
This is because EDR leverages behavioral analysis to rapidly detect significant anomalies.
This unique ability helps it detect advanced attacks, such as in-memory and fileless malware.
Yet these attacks easily evade antivirus detection. By focusing on suspicious activity rather than predefined signatures, EDR enhances endpoint security with real-time monitoring and rapid detection of unknown threats.
Scope of Security Coverage
Traditional antivirus solutions focus on protecting individual devices from viruses and malware.
They do that part beautifully. However, they are incapable of adapting to today’s environments, which are adopting bring-your-own-device (BYOD) policies.
EDR, in contrast, protects a wider variety of endpoints, extending protection from desktops to IoT devices.
This end-to-end coverage is what makes EDR such a critical solution for organizations that require full-spectrum, proactive security in complex, varied environments.
Incident Response Abilities
Traditional antivirus solutions typically leave users in the dark, relying on manual intervention to mitigate threats flagged.
EDR, on the other hand, automates these response actions, whether that be isolating compromised endpoints or neutralizing threats.
This ability greatly reduces the scope of damage and accelerates response time.
This way, security teams can prioritize strategic initiatives rather than constantly reacting to threats.
EDR vs. Antivirus
|
Feature |
Endpoint Detection and Response (EDR) |
Traditional Antivirus (AV) |
|
Primary Function |
Detects, investigates, and responds to threats in real-time |
Scans for and removes known malware threats |
|
Threat Detection |
Identifies both known and unknown (zero-day) threats using behavioral analysis and AI |
Relies on signature-based detection of known threats |
|
Response Capabilities |
Allows active threat hunting, containment, and forensic analysis |
Limited to malware removal and quarantine |
|
Real-Time Monitoring |
Continuously monitors endpoints for suspicious activity |
Periodic scans but lacks real-time deep monitoring |
|
Attack Visibility |
Provides full visibility into attack chains and lateral movements |
Limited visibility; mostly focuses on individual file threats |
|
Machine Learning & AI |
Uses advanced analytics and AI to detect sophisticated threats |
Limited AI capabilities; mostly rule-based detection |
|
Zero-Day Threat Protection |
Detects and mitigates unknown threats based on behavior |
Limited or no protection against zero-day attacks |
|
Incident Investigation & Forensics |
Offers in-depth forensic tools to analyze past incidents |
No forensic tools; only basic threat reports |
|
Remediation Actions |
Can isolate infected systems, rollback changes, and remove threats |
Basic remediation such as file deletion and quarantine |
|
Cloud Integration |
Fully integrated with cloud-based security platforms |
Mostly standalone, though some newer AVs offer cloud-based updates |
|
System Performance Impact |
Can be resource-intensive but optimized for enterprises |
Lighter on system resources, making it more suitable for older systems |
|
Ideal For |
Businesses with a proactive security approach requiring advanced threat detection |
Small businesses or individuals needing basic protection |
|
Compliance Requirements |
Helps meet compliance requirements for data security (e.g., GDPR, HIPAA) |
May not be sufficient for compliance in regulated industries |
|
Cost |
Higher cost due to advanced capabilities and AI-driven security |
Lower cost, suitable for small businesses with basic security needs |
EDR Extends Antivirus Capabilities
Endpoint Detection and Response (EDR) supercharges the traditional antivirus model. It addresses its shortcomings and introduces new, more effective threat detection techniques.
Antivirus software is incredibly efficient at stopping established threats through signature-based detection.
Unlike AV’s posture of protecting against known malware, EDR detects the unknown, advanced attacks that slip through traditional defenses.
This mutualistic connection fortifies cybersecurity by merging reactive and proactive approaches for a comprehensive, adaptive, and resilient defense strategy.
Beyond Signature-Based Detection
The problem with traditional antivirus products is that they only work if they recognize a malware signature, which means they can’t defend against new or altered threats.
Next generation antivirus solutions break out of these limitations by utilizing behavioral analysis.
They provide continuous monitoring of endpoint activity, identifying abnormal patterns such as unauthorized data access or suspicious application launches.
For example, EDR software can stop fileless malware that runs in-memory and doesn’t leave traditional signatures for other antivirus tools to find.
Such capabilities are essential for keeping up with today’s advanced cyber threats, where adversaries employ innovative techniques to avoid detection and slip through the cracks.
According to our friends at AV-Comparatives, every day over 450,000 new malware samples appear.
To safeguard your systems from these ever-changing threats, comprehensive cybersecurity strategies with deeper detection capabilities are essential.
Advanced Threat Detection Scenarios
EDR’s strength comes from its detection of sophisticated threats. For one, it can stop human-driven ransomware such as Hive that easily evades antivirus solutions.
EDR’s ability to detect insider threats like compromised accounts with access to sensitive data illustrates its proactive nature.
It actively remediates threats on its own, limiting reliance on human resources. Merging antivirus and EDR capabilities make for an excellent layered security model.
This blend of antivirus, EDR, behavioral analysis, and machine learning helps protect you against all attack vectors including in-memory attacks and data exfiltration.
Enhancing Incident Response
EDR enhances incident response with real-time alerts and automated containment capabilities to lessen damage.
It does offer a treasure trove of actionable insights during post-incident analysis, assisting your team in proactively shoring up defenses.
When we consider active breaches, for instance, EDR gives security teams the ability to automatically and immediately quarantine compromised endpoints, reducing both downtime and downstream impact.
When to Use Antivirus
Antivirus software is still a bedrock of cybersecurity, especially in environments with less complex security requirements.
This tried-and-true solution protects reliably against run-of-the-mill malware and other known threats. It equally gives them vital protection features at an economical charge.
Using a combination of signature-based, heuristic, and behavioral detection methods, antivirus software protects devices by identifying and neutralizing potential risks.
Its simplicity and affordability make it a practical choice for small businesses, legacy systems, and networks with minimal exposure to advanced threats.
Ideal Scenarios for Antivirus
For organizations with limited budgets, antivirus provides affordable protection against malware without demanding significant IT resources.
Workspaces with minimal internet access or limited threat exposure can rely on antivirus to safeguard against basic vulnerabilities.
Underfunded and aging systems are not compatible with today’s cutting-edge solutions. Antivirus helps keep these systems secure, and you don’t want to rip everything out and start over.
Antivirus is incredibly useful for scanning USB drives and external storage, stopping the spread of malware through physical devices.
Advantages of Antivirus Use
Antivirus tools are an economical way to establish baseline security for SMBs. Easy installation and administration also make antivirus perfect for small businesses with no IT staff.
It effectively shields against common malware types and email-based threats, which account for nearly 80% of malware infections.
Many industries require basic security measures, and antivirus helps maintain compliance with these standards.
Best Practices for Antivirus
Ensure virus definitions are regularly updated to defend against emerging threats.
Schedule regular scans to detect dormant or overlooked malware.
Promote safe browsing habits to complement antivirus efforts and reinforce cybersecurity awareness.
As many as 90% of successful cyberattacks originate at endpoint devices, underscoring the critical need for robust endpoint security measures.
When to Use EDR
That’s because in today’s cybersecurity environment, what worked in years past isn’t enough to meet the advanced challenges businesses are up against.
Here, Endpoint Detection and Response (EDR) becomes the enterprise’s highly advanced knight in shining armor, providing one of the most powerful protections against even the most sophisticated threats.
While antivirus primarily focuses on known threats, EDR provides extensive visibility, detection, and response capabilities, making it indispensable in certain scenarios.
Ideal Scenarios for EDR
Very large enterprises with complex IT ecosystems stand to gain a tremendous amount from EDR.
Its unparalleled capacity for monitoring endpoints across a complicated network helps make sure that even the most discreet threat is detected and quickly mitigated.
Organizations managing sensitive data, such as those in healthcare or finance, require EDR to safeguard against breaches and unauthorized access.
Companies under sustained, ongoing cyber-attack or zero-day threats consider EDR critical for its proactive, continuous threat hunting coupled with real-time response.
Advantages of EDR Use
EDR excels at detecting both known and unknown threats, including fileless attacks or unusual behavior, offering unparalleled protection.
It’s threat hunting capabilities greatly strengthen security through actively searching for vulnerabilities or dormant risks, minimizing exposure.
Through automation, EDR reduces the need for human involvement, enabling security professionals to focus on more critical activities.
Rich analytics and reporting deliver real-time insights to focus your efforts, allowing for prioritized, data-driven decisions that maximize security outcomes.
Best Practices for EDR
To ensure you are getting the most value from EDR, configuration should be reviewed frequently and refined to capture new and evolving threats.
Security teams must be given regular training to take advantage of all EDR features and respond effectively to incidents.
By integrating EDR with other tools, including firewalls or SIEM as an example, it strengthens the cohesive and layered cybersecurity strategy.
Hybrid Security Model
Combining EDR with antivirus creates a hybrid model, leveraging antivirus for basic protection while EDR addresses advanced threats.
Using this layered or defense in-depth approach helps to fill multiple gaps and provide more comprehensive security.
Together, they fulfill not just the classic cybersecurity needs, but the new-age ones, providing organizations with a scalable and comprehensive security solution.
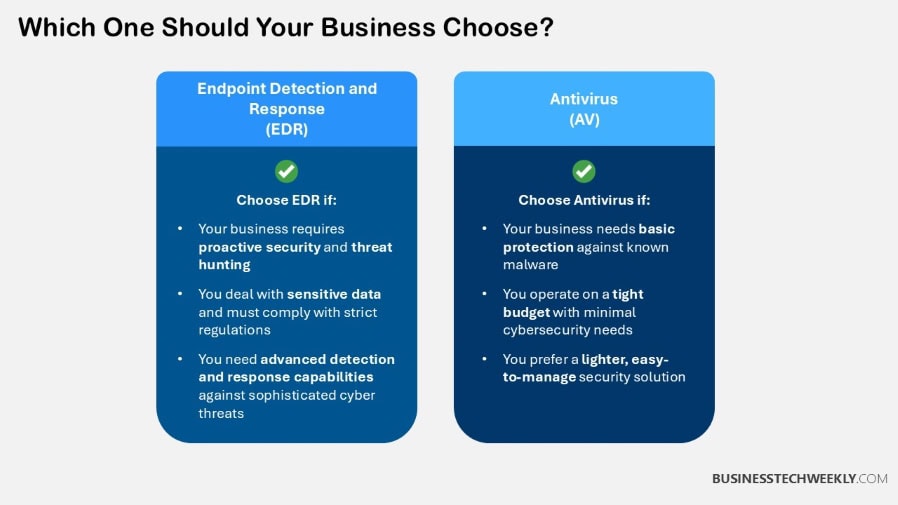
Hybrid Security Model
The answer is a hybrid security model that provides the best of all solutions. It combines Endpoint Detection and Response (EDR) with legacy antivirus (AV) to provide superior protection.
This model builds a defense system of layers upon layers of protection, focusing on previously identified and incoming threats.
While AV specializes in signature-based detection, EDR incorporates real-time monitoring and response, allowing them to work together as complementary tools.
Combining EDR and Antivirus
The integration of EDR with AV provides the deepest level of protection by complementing their unique features.
With the benefit of known good and bad signatures, AV can rapidly detect and quarantine malware.
EDR, as opposed to such, identifies and monitors suspicious activity and acts on sophisticated attacks.
When combined, these tools give the best protection against all types of attacks, including phishing email and ransomware.
For instance, AV might successfully quarantine a known virus.
Conversely, EDR is able to monitor for suspicious lateral movement across a network, preventing any further escalation of the attack. This important redundancy means that when one tool fails to detect a threat, the other tool is equipped to cover it.
That’s why compatibility is key when integrating these solutions together. Both systems need to work together smoothly, though, so there aren’t operational conflicts or gaps in coverage.
What’s true is that frequent updates and patches are necessary to keep them effective against ever-changing threats.
With continuous monitoring, a hybrid system can constantly evolve past emerging vulnerabilities, giving businesses a continuously resilient defense mechanism.
Benefits of a Layered Approach
A hybrid security model adds risk across several solutions, lessening the likelihood of having one point of failure.
This hybrid strategy meets today’s challenges by leveraging EDR for continuous prevention and monitoring of advanced threats and AV for protection against known legacy malware.
For SMEs, striking this balance means they can afford the protection they need, without exhausting their operational resources.
Frequent evaluations allow for recalibrating these tools according to the direct business risks on hand, making sure that each investment puts real value back in their pockets.
Optimizing Security Investments
When transitioning to EDR, organizations should evaluate existing infrastructure and involve key stakeholders.
Identifying gaps and preparing staff for proactive threat management ensures a smooth shift.
This cultural shift toward continuous improvement strengthens long-term cybersecurity resilience.
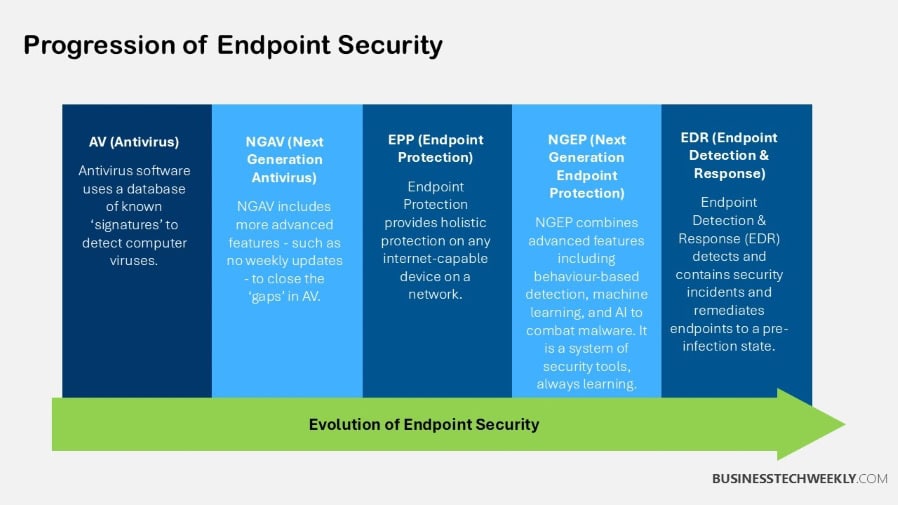
Transitioning to EDR
Businesses are under attack by ever more sophisticated duplicitous cyber adversaries.
To address these threats, organizations need to move beyond legacy antivirus platforms and adopt Endpoint Detection and Response (EDR). Unlike antivirus that’s limited to static definitions, EDR allows for dynamic threat detection with real-time analysis of endpoint activity.
This proactive approach is extremely important as more than 450,000 new malware types are reported daily.
By comparison, legacy antivirus solutions can only hope to catch around a measly 1% of those. Transitioning to EDR requires careful advanced planning to ensure it is effective and beneficial while avoiding unnecessary disruptions.
Key Considerations for Migration
A complete and detailed migration plan is key to implementing EDR successfully. Begin with an audit of your existing security products to see where the compatibility holes are.
While most EDR solutions will be able to fit nicely into current systems, misalignments can create roadblocks or even waste time and effort.
Evaluate your security team’s skill level because implementing EDR requires the ability to parse complex alerts and recognize sophisticated threat activity.
Organizations usually struggle to redirect resources to address EDR alerts, making training necessary. Prepare for interruptions in service when deploying.
Pilot programs are an effective means to test the functionality and deployment of EDRs in a controlled environment prior to or instead of a larger rollout.
Set measurable goals and deadlines to ensure the migration process stays focused on your company’s business objectives.
Planning Your EDR Implementation
Prioritizing scalability, integration capabilities, and available support services are critical factors.
Features to look for include real-time monitoring, automated or semi-automated incident response, and operations across your current hardware and software infrastructure.
Most providers provide a free trial or demo, allowing you to see how effective the system would be before you invest in one.
Doing your research on the vendor up front will help you choose an EDR solution that meets your overall security requirements.
Many legacy AVs offer add-ons like firewall management or data encryption.
These features are limited in their scope when contrasted with the depth that EDR can provide.
Evaluating EDR Solutions
Addressing threats such as ransomware requires adaptive security strategies. Staying ahead of evolving threats like ransomware requires adaptive security strategies.
Where EDR truly shines is in providing ongoing enhancement via more sophisticated detection and response techniques.
That’s why good endpoint security is a constant evolution and should prioritize consistently shifting your strategy to meet new and evolving risks.
Key Points to Note
So EDR vs antivirus, which is better? Ultimately, the choice between EDR and antivirus lies in knowing your organization’s requirements and exposure.
For some, a mixture of both tools could be a happy medium.
- Traditional antivirus AV is still an important piece of security to detect and defeat known malware threats. To start, it gives you basic protection with real-time monitoring, malware scanning, and scheduled security scans. Continuous updates are necessary to keep it effective.
- Traditional antivirus solutions simply cannot do enough in the face of advanced threats such as unknown malware variants and targeted cyberattacks. For one, they depend almost exclusively on signature-based detection—detection methods that fall short when it comes to innovative threats.
- Endpoint Detection and Response (EDR) provides organizations with powerful capabilities. These powerful capabilities include real-time monitoring, behavioral analysis, and automated threat response. It has a greater ability to detect both known and unknown threats, making it a more robust security solution.
- EDR remote access enables organizations to hunt for threats proactively, monitor for anomalies, and respond to incidents faster. Its rich forensic analysis capabilities are a great fit for organizations with complex IT environments and high security demands.
- A unified security strategy that integrates the capabilities of both antivirus and EDR solutions delivers the layered protection you need. This model strikes the perfect balance between the simplicity of antivirus and the robust capabilities of EDR, defending against a full spectrum of cyber threats.
- Organizations should evaluate their security needs, IT infrastructure, and budget when deciding between antivirus, EDR, or a hybrid model. Implementing best practices, such as regular updates and team training, maximizes the effectiveness of both tools.

